![Previous Topic: Request and Install a Policy Server Token Signing Certificate [3]](574.png)

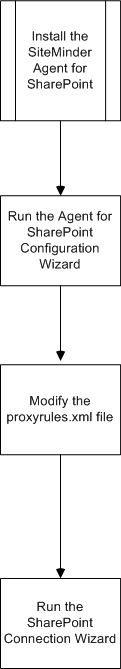
The following illustration describes the tasks you perform when configuring the CA SiteMinder® Agent for SharePoint:
The CA SiteMinder® Agent for SharePoint supports the requirements for cryptographic modules that are specified in the Federal Information Processing Standards (FIPS) 140-2 standard. Select the level of FIPS support that you want during installation.
During a new installation, select one of the following FIPS modes:
The FIPS mode that you select during installation usually is the same as the FIPS mode configured on the Policy Server.
Before you install the CA SiteMinder® Agent for SharePoint, the Policy Server must be configured. Verify that the following items are complete:
To use the CA SiteMinder® Agent for SharePoint, the system where you plan to install it must have at least 256 MB of RAM. Other prerequisites differ based on the server system.
For detailed information, see the CA SiteMinder® Agent for SharePoint Support Matrix at http://ca.com/support.
Note: Installation prerequisites pertain to the system on which you run the CA SiteMinder® Agent for SharePoint, not the destination servers to which the CA SiteMinder® Agent for SharePoint routes incoming requests.
The CA SiteMinder® Agent for SharePoint installation consists of two tasks:
Note: Throughout the installation instructions, there are references to Agent-for-SharePoint_home in directory paths. This variable represents the installation directory of the CA SiteMinder® Agent for SharePoint.
The default installation location for the agent on 32-bit Windows operating environments is: C:\Program Files\CA\Agent-for-SharePoint. On 64-bit Windows operating environments, the default installation location is C:\CA\Agent-for-SharePoint.
Important! The CA SiteMinder® Agent for SharePoint cannot be installed on a computer that hosts any other web server. The CA SiteMinder® Agent for SharePoint operates as a stand-alone proxy-based solution.
To run the agent installer on Windows operating environments, you need local Administrator privileges.
Note: We recommend installing the agent on an NTFS file-system partition.
Follow these steps:
ca-sp2010agent-version-operating_environment.exe
The installation program starts.
Note: The installer displays all Java executables that are installed in the system. Pick a Java component and version that is equal to or greater than the one shown by the installer. If the installer does not detect any Java executables by default, then browse and select the appropriate path. For more information about the required Java executables or other third-party software requirements, see the platform support matrix.
The default installation location is user_home/CA/Agent-for-SharePoint. The folder where you install the agent requires sufficient permissions (755). Do not install the agent under the /root folder, because its default permissions (750) are insufficient.
Important! The CA SiteMinder® Agent for SharePoint cannot be installed on a computer that hosts any other web server. The CA SiteMinder® Agent for SharePoint operates as a stand-alone proxy-based solution.
Note: On the Solaris or Linux operating environments, the agent runs under the "nobody" user account. If you prefer not to run the agent under this user account, create an alternate user and assign the necessary permissions. Do not run this program as a root user.
Follow these steps:
Note: The installer displays all Java executables that are installed in the system. Pick a Java component and version that is equal to or greater than the one shown by the installer. If the installer does not detect any Java executables by default, then browse and select the appropriate path. For more information about the required Java executables or other third-party software requirements, see the platform support matrix.
After you install the CA SiteMinder® Agent for SharePoint, configure the agent for the requirements of your SharePoint environment. Configuring the agent requires several separate procedures, which are described in the following process:
Note: To operate the CA SiteMinder® Agent for SharePoint with the CA DataMinder content classification service (CCS), configure different proxy rules instead.
The CA SiteMinder® Agent for SharePoint configuration wizard helps you register a trusted host, configure the embedded Apache web server
Verify the prerequisites before continuing.
To establish a connection between the CA SiteMinder® Agent for SharePoint and the Policy Server, register a trusted host with the Policy Server. After registration is complete, the registration tool creates the SmHost.conf file. When this file is created successfully, the CA SiteMinder® Agent for SharePoint is allowed to communicate with the Policy Server.
The following lists the required host registration information:
Name of a SiteMinder administrator who has privileges to create a trusted host.
Password of the SiteMinder administrator.
Name of the trusted host assigned during configuration.
Note: The name you enter for the trusted host must be unique.
Name of a host configuration object already defined in the Policy Server administrative UI.
Name of an existing Agent Configuration Object defined in the Policy Server administrative UI.
Note: Include a port number for the Policy Server. For example, 121.111.12.11:44442.
Identifies the SmHost.conf file, which Web Agents and custom Agents use to act on behalf of the trusted host. Using this file, the host can find a Policy Server and establish a connection. The wizard lists the default location.
The email address for the administrator Default: admin@example.com.
Specifies the hostname of the CA SiteMinder® Agent for SharePoint, this hostname is the address users enter in their web browser:
spagent.example.com
The port listening for HTTP requests Default: 80.
The port listening for SSL requests Default: 443.
The HTTP port used for Claims web service.
The SSL port used for Claims web service.
Note: No default values are provided for the Claims WS HTTP and SSL Ports. However, use a port that is free, which Tomcat can use to host the web application. For UNIX and Linux, the ports must be greater than 1024. Nobody account works with ports above 1024.
Indicates if the configuration wizard enables (starts) the agent automatically. This setting produces the same results as editing the EnableWebAgent parameter value in the WebAgent.conf file with a text editor.
Default: No (clear check box)
After you install the CA SiteMinder® Agent for SharePoint, run the configuration wizard. The configuration wizard registers the CA SiteMinder® Agent for SharePoint with the Policy Server and performs some administrative tasks for the embedded Apache web server.
Before you run the wizard, verify that the required Policy Server objects exist.
Note: Tomcat uses the nobody user by default because it is the least privileged user.
Important! If you have previously run the configuration wizard on your CA SiteMinder® Agent for SharePoint, create a backup copy of your proxyrules.xml file. The configuration wizard creates a default proxyrules.xml file each time it runs on a computer.
Follow these steps:
The wizard starts. The Host Registration screen appears.
Note: In Windows, you can alternatively navigate to Agent-for-SharePoint_home/install_config_info and double-click ca-spagent-config.exe.
The information you enter must be defined at the Policy Server where the trusted host registers. This screen also includes an optional check box for enabling shared secret rollover.
The name you enter for the trusted host must be unique. The name for the Host Configuration Object must already be defined at the Policy Server where the trusted host is registered.
Note: Include a port number for the Policy Server. For example, 121.111.12.11:44442.
Enter the name of the ACO built from the SharePoint2010DefaultSettings ACO template defined in the Policy Server.
Note: On Solaris or Linux, an additional screen prompts for the name of the user under which Tomcat and Apache run. This user cannot be root.
Note: No default values are provided for the Claims WS HTTP and SSL Ports. However, use a port that is free, which Tomcat can use to host the web application. For UNIX and Linux, the ports must be greater than 1024. Nobody account works with ports above 1024.
The files are installed.
Note: If you run the Configuration Wizard again for any reason, SSL must be reinitialized. The installer contacts the Policy Server and attempts to register the Trusted Host to create the host configuration file. If trusted host registration does not succeed, the CA SiteMinder® Agent for SharePoint cannot contact the Policy Server and operate properly.
After you install the CA SiteMinder® Agent for SharePoint, but before changing the proxy rules, you can verify that the server is functioning. You can request index.html file by using the server and port number you specified during installation. For example, if you installed the CA SiteMinder® Agent for SharePoint on server1.example.com and selected port 88 for HTTP communication, you can request the following URL with a browser:
http://server1.example:com:88
If the CA SiteMinder® Agent for SharePoint is working properly, the request redirects to the main CA website (www.ca.com). The default proxy rules file specifies this URL for all redirects.
The CA SiteMinder® Agent for SharePoint operates as a proxy-based solution. To protect your SharePoint resources, edit the default proxy rules files.
Note: To operate the CA SiteMinder® Agent for SharePoint with the CA DataMinder content classification service (CCS), configure different proxy rules instead.
Follow these steps:
Agent-for-SharePoint_home\proxy-engine\conf\proxyrules.xml
Important! Do not modify any other configuration files or settings unless explicitly told to do so by CA support personnel.
<nete:forward>http://www.ca.com$0</nete:forward>
If the URL is sharepoint.example.com, edit the line to match the following example:
<nete:forward>http://www.sharepoint.example.com$0</nete:forward>
Note: The proxyrules.xml file used by the Agent for SharePoint supports redirection to one URL. The CA SiteMinder® Agent for SharePoint does not provide any built-in load-balancing functions.
The proxy rule is set.
The CA SiteMinder® Agent for SharePoint supports dynamic Policy Server clusters. These dynamic Policy Server clusters automatically report when individual Policy Servers are added to or removed from a cluster. A restart of the CA SiteMinder® Agent for SharePoint is not required.
Follow these steps:
Agent-for-SharePoint_home\proxy-engine\conf\defaultagent\SmHost.conf
enabledynamichco="NO"
enabledynamichco="YES"
Support for dynamic policy servers is enabled. The CA SiteMinder® Agent for SharePoint automatically detects changes to Policy Server clusters.
The CA SiteMinder® Agent for SharePoint uses an embedded Apache web server. Install the Policy Server signing certificate you want to use for your SharePoint Connection. We recommend using a certificate signed by a Certificate Authority. After copying the certificate and related key files to your CA SiteMinder® Agent for SharePoint, edit the configuration file for the embedded Apache web server.
Follow these steps:
Agent-for-SharePoint_home\httpd\conf\extra\httpd-ssl.conf
On the UNIX or Linux operating environments, the user account under which the CA SiteMinder® Agent for SharePoint runs requires permissions to create log files.
After running the CA SiteMinder® Agent for SharePoint configuration wizard on a UNIX or Linux operating environment, grant the user account the permissions shown in the following table:
|
Grant these permissions: |
To these directories: |
|---|---|
|
Read, Execute |
Agent-for-SharePoint_home directory and all subdirectories |
|
Write |
Agent-for-SharePoint_home/proxy-engine/logs |
The SharePoint connection wizard takes you through the process of configuring and managing SharePoint connections with CA SiteMinder®.
Before running the wizard, gather the following information:
Specifies the Policy Server name or IP address.
Example: host_name:port_number
Note: Specify the Administration port number if the port number is different from the default port number 44444.
Specifies the Policy Server administrator username.
Specifies the Policy Server administrator password.
Specifies the name of the 4.x-compatible Agent object on your Policy Server. The connection with the Policy Server is established using the details given in the Agent Name.
Specifies the shared secret key that is associated with the 4.x-compatible Agent object on your Policy Server.
Specifies the name of the policy domain you created in the Policy Server to protect your SharePoint resources.
Specifies a name for the SharePoint connection. This name is also used as the file name of the PowerShell script that the wizard creates.
Note: Use a unique name across all Resource Partners and SharePoint connections.
Specifies the port number that is associated with the predefined protected URL which the SharePoint connection wizard adds automatically. When users try accessing a protected SharePoint resource without a SiteMinder session, they are redirected to the Authentication URL.
If you are using a default port number (such as 80 for HTTP or 443 for HTTPS), delete the <port> setting from this field.
Note: We recommend using HTTPS on production environments and pages which handle user credentials, such as login pages.
Specifies a name for a SharePoint realm that uniquely identifies this connection between SiteMinder and SharePoint. This name is used to create the trusted identity provider.
Limits: Unique value across all SharePoint servers, farms and within the SiteMinder environment. This value cannot be used with any other identity providers.
Specifies the number of seconds used as a time difference between the Policy Server (token producer) and the SharePoint server (token consumer). This skew time accommodates for SharePoint connections using clocks that are acting as an account partner but are not synchronized with the Policy Server.
Note: This setting also affects the frequency of the SAML autopost operation.
Limits: Positive integers.
Specifies the number of seconds for which a session remains valid. If the validity duration expires, a logout message is generated. The user that is associated with the invalid session is logged out.
Note: This setting also affects the frequency of the SAML autopost operation.
Specifies the alias that the key store uses to identify the private key that is associated with the certificate your Policy Server uses to sign the tokens.
Note: We recommended verifying that the private key exists in the central key store before you specify its associated alias in this field. Open the Administrative UI, and then click Infrastructure, X.509 Certificate Management, Trusted Certificates and Private Keys for a list of certificates and their aliases.
Specifies the protection level that is assigned to the resource partner object the connection wizard creates. This protection level setting must be equal to or lower than the protection level assigned to the authentication scheme that protects your SharePoint resources.
Limits: 1-1000 (higher numbers indicate a higher protection level).
Specifies name of the attribute mapping in your user directory which identifies the unique value that is associated with each user.
Example: useridentifier
Specifies the directory attribute in your directory that is associated with the specified Identifier Claim name.
Example: (LDAP directory) uid
Example: (Active directory) sAMAccountName
Specifies an attribute name for one of the following claim types:
For multi–valued attributes, prefix FMATTR:
Example: (group–based claim) smusergroups
Example: (role-based claim) userrole
Example: (multiv–alued attributes) FMATTR:LastName
Specifies an attribute value that is associated with the specified attribute name.
For group-based claims, use the friendly role of your groups. The people picker in SharePoint displays the description and distinguished name (DN) of the group. Permissions are tied to the DN of the group, not the friendly name.
Example: (LDAP directory group-based claim) description
Example: (LDAP directory role-based claim) employeeType
Example: (Active Directory group-based claim) name
Example: (Active Directory role-based claim) countryCode
Indicates if the single log out feature is enabled for the associated cleanup URLs and the associated confirm URLs.
Specifies the URLs of the cleanup pages for the single log out feature.
Limits: Separate multiple URLs with a semicolon (;)
Specifies the URLs of the confirmation pages for the single log out feature.
Limits: Separate multiple URLs with a semicolon (;)
Before you run the SharePoint Connection Wizard, perform the following steps:
|
Copyright © 2014 CA.
All rights reserved.
|
|