

Policy Server Guides › Policy Server Configuration Guide › CA SSO/WAC Integration
CA SSO/WAC Integration
This section contains the following topics:
Overview
SiteMinder and CA SSO Integration Architectural Examples
CA SiteMinder® and CA SSO Integration Prerequisites
Configure Single Sign-On from SiteMinder to CA SSO
Configure Single Sign-On from CA SSO Client to SiteMinder
Configure Single Sign-On from CA SSO to SiteMinder
Configure an smetssocookie Web Agent Active Response Attribute
Configure an smauthetsso Custom Authentication Scheme
Overview
CA SiteMinder® provides single sign-on from CA SiteMinder® to the CA SSO environments. Users log in to a CA SiteMinder® or CA SSO environment, and once authenticated by CA SiteMinder®, are authenticated for both environments. Authenticated users can access protected resources in either environment without having to reenter credentials, as long as they are authorized. User authorization is based on the policies in effect within each environment.
When allowing users to access secure resources, CA SiteMinder® and CA SSO each maintain user credentials in their own session stores. They also have their own proprietary session credentials that cannot be read by the other and, thus, user credentials are maintained separately. Since these credentials reside in different stores, to enable single sign-on, the CA SiteMinder® Policy Server and CA SSO Policy Server must be part of the same cookie domain and must share the same user or authentication store.
In this single sign-on configuration, the CA SiteMinder® and CA SSO Policy Servers can be on the same or on different machines. CA SiteMinder® can contain a Web Agent, CA SiteMinder® SPS, or both. You use a Web Agent or CA SiteMinder® SPS based on your own CA SiteMinder® environment. CA SSO uses the eTrust Web Access Control (WAC) Web Agent, and you do not need to modify your current environment to enable single sign-on with CA SiteMinder®.
Note: You must be intimately familiar with CA SiteMinder® and CA SSO before configuring single sign-on between the products. For a list of supported CA SiteMinder®, CA SiteMinder® SPS, CA SSO, and eTrust WAC versions, refer to the 6.0 CA SiteMinder® and Agents Platform Matrix on the Technical Support site.
More information:
SiteMinder and CA SSO Integration Architectural Examples
SiteMinder and CA SSO Integration Architectural Examples
The following are three examples of single sign-on between CA SiteMinder® and CA SSO environments:
- A user authenticates to CA SiteMinder® using a Web browser and then accesses an CA SSO-protected resource (see Example 1: User Accesses SiteMinder-Protected Resource Before CA SSO).
- A user authenticates to CA SSO through a desktop CA SSO Client and then accesses a CA SiteMinder®-protected resource using a Web browser (see Example 2: Authenticated CA SSO Client User Accesses SiteMinder Resource).
- A user authenticates to CA SSO using a Web browser and then accesses a CA SiteMinder®-protected resources (see Example 3: User Accesses CA WAC-Protected Resource Before SiteMinder).
Note: In these examples, the CA SiteMinder® and CA SSO Policy Servers authorization access steps to protected resources are omitted for clarity.
More information:
Configure Single Sign-On from CA SSO Client to SiteMinder
User Accesses SiteMinder-Protected Resource Before CA SSO
The following example illustrates a user accessing CA SiteMinder®-protected resource before a WAC-protected resource:
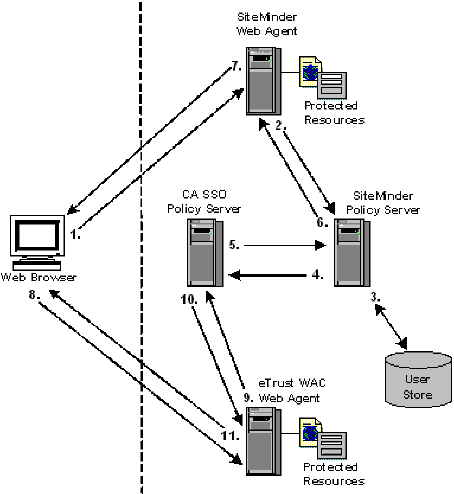
- The user tries to access a CA SiteMinder®-protected resource and the CA SiteMinder® Web Agent/CA SiteMinder® SPS intercepts the request. The user provides the Agent/SPS with authentication credentials.
- The Web Agent/CA SiteMinder® SPS forwards the credentials to the CA SiteMinder® Policy Server for validation.
- The CA SiteMinder® Policy Server verifies that the user’s credentials are valid in the user store.
- After successful authentication, the CA SiteMinder® Policy Server requests the CA SSO Policy Server to issue and return an CA SSO cookie for the CA SiteMinder® user.
- The CA SSO Policy Server validates the user and forwards the user’s CA SSO web authentication credentials to the CA SiteMinder® Policy Server.
- The CA SiteMinder® Policy Server forwards the CA SSO web authentication credentials to the CA SiteMinder® Web Agent/CA SiteMinder® SPS.
- The CA SiteMinder® Web Agent/CA SiteMinder® SPS sets the CA SSO web authentication and CA SiteMinder® cookies in the user’s browser and returns the resource to the user.
- The user tries to access an CA SSO resource and the eTrust WAC Web Agent intercepts the request.
- The eTrust WAC Web Agent validates the user’s CA SSO web authentication cookie credentials with the CA SSO Policy Server.
- The CA SSO Policy Server tells the eTrust WAC Web Agent that the user has valid credentials.
- The eTrust WAC Web Agent allows the user to access the CA SSO-protected resource.
Authenticated CA SSO Client User Accesses SiteMinder Resource
The following example illustrates an authenticated CA SSO client user accessing a CA SiteMinder® protected resource:
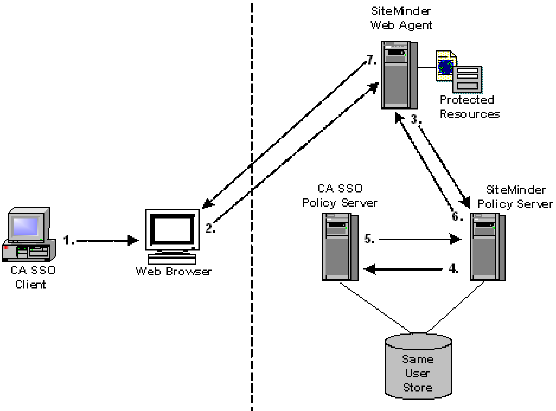
- An authenticated CA SSO Client user launches a Web browser. While this is happening, the CA SSO Client places an CA SSO Web authentication cookie into the browser.
- The user tries to access a CA SiteMinder®-protected resource using the Web browser and the request is intercepted by the CA SiteMinder® Web Agent/CA SiteMinder® SPS.
- The CA SiteMinder® Web Agent/CA SiteMinder® SPS forwards the CA SSO Web authentication cookie to the CA SiteMinder® Policy Server.
- The CA SiteMinder® Policy Server forwards the CA SSO Web authentication cookie to the CA SSO Policy Server.
- The CA SSO Policy Server validates the CA SSO Web authentication cookie and returns the user name to the CA SiteMinder® Policy Server.
- The CA SiteMinder® Policy Server verifies the returned user name in the CA SiteMinder® user store, then issues a corresponding CA SiteMinder® cookie and returns it to the CA SiteMinder® Web Agent/CA SiteMinder® SPS.
- The CA SiteMinder® Web Agent/CA SiteMinder® SPS returns the requested resource to the user, who now has the authentication cookie credentials necessary for CA SiteMinder® and CA SSO environments.
User Accesses eTrust WAC-Protected Resource Before SiteMinder
The following example illustrates a user accessing a WAC-protected resource before CA SiteMinder®.
Note: The example assumes the environment is using a IIS6 WAC Agent. An IIS6 WAC Agent is the only platform that the following example supports.
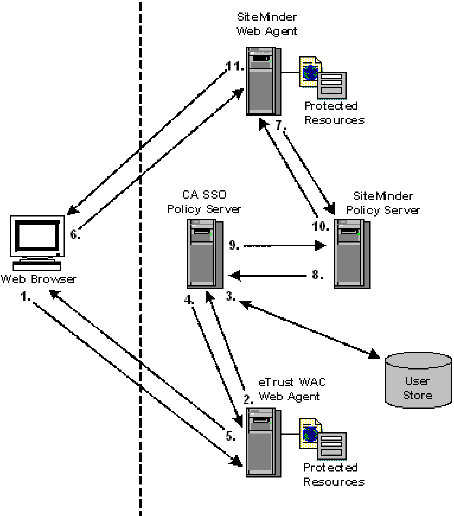
- The user tries to access an CA SSO-protected resource and the eTrust WAC Web Agent intercepts the request. The user provides the Agent with authentication credentials.
- The Web Agent forwards the credentials to the CA SSO Policy Server for validation.
- The CA SSO Policy Server makes sure that the user’s credentials are valid in the user store.
- The CA SSO Policy Server forwards the user’s eTrust SSO Web credentials to the eTrust WAC Web Agent.
- The eTrust WAC Web Agent sets the user’s CA SSO Web authentication cookie in the Web browser.
- The user tries to access a CA SiteMinder®-protected resource and the CA SiteMinder® Web Agent/CA SiteMinder® SPS intercepts the request.
- The CA SiteMinder® Web Agent/CA SiteMinder® SPS forwards the user’s CA SSO Web authentication credentials to the CA SiteMinder® Policy Server.
- The CA SiteMinder® Policy Server forwards the user’s CA SSO Web authentication credentials to the eTrust SSO Policy Server.
- The CA SSO Policy Server validates the user’s CA SSO Web authentication credentials and forwards the user name back to the CA SiteMinder® Policy Server.
- The CA SiteMinder® Policy Server verifies the returned user name in the CA SiteMinder® user store, then issues a corresponding CA SiteMinder® cookie and returns it to the CA SiteMinder® Web Agent/CA SiteMinder® SPS.
- The CA SiteMinder® Web Agent/CA SiteMinder® SPS sets the CA SiteMinder® cookies in the user’s browser and allows the user to access the requested resource.
CA SiteMinder® and CA SSO Integration Prerequisites
Before configuring a single sign–on integration between CA SiteMinder® and CA SSO:
- Install and configure CA SSO.
Note: When installing the CA SSO Policy Server, gather the following:
- An SSO administrator name and password. The CA SiteMinder® Policy Server uses the administrator name and password when authenticating to the CA SSO Policy Server through the smauthetsso authentication scheme.
- The SSO ticket encryption key. The CA SiteMinder® Policy Server smetssocookie active response requires this value.
- Be sure that the CA SiteMinder® environment and the CA SSO environment are operating in the same FIPS mode (AES encryption) of operation.
Important! The integration fails if both environments are not operating in the same FIPS mode of operation.
- Consider the following:
- If the integration is to operate in FIPS–only mode, CA SiteMinder® Policy Servers must be operating at r12.0 SP1 CR3 or later. If necessary, upgrade the CA SiteMinder® Policy Servers that are to communicate with the CA SSO Policy Server.
- Be sure that operating systems on which the Policy Servers are installed support the smauthetsso authentication scheme. The integration requires that you configure the smauthetsso authentication scheme. For more information, see the 12.52 CA SiteMinder® Platform Support Matrix.
Configure Single Sign-On from SiteMinder to CA SSO
CA SiteMinder® provides single sign-on from CA SiteMinder® to CA SSO environments.
To enable single sign-on from CA SiteMinder® to CA SSO using a CA SiteMinder® Web Agent or CA SiteMinder® SPS
Enable the CA SiteMinder® SSO Plug-in installed with the Web Agent or CA SiteMinder® SPS:
- For the 12.52 IIS 6.0 or Apache 2.0 Web Agent
-
- Remove the comment (#) character from one of the following lines in the WebAgent.conf file:
- (Windows operating environments) #LoadPlugin=Path_to_eTSSOPlugin.dll_file
- (UNIX or Linux operating environments) #LoadPlugin=Path_to_libetssoplugin.so_file
Note: Restart the Web server after you modify the WebAgent.conf file so the new configuration settings take effect.
- For the 6.0 CA SiteMinder® SPSr
-
Note: Restart CA SiteMinder® SPS after you modify the WebAgent.conf file so the new configuration settings take effect.
To enable single sign-on using the WAC Web Agent
- Configure the domain in the WAC Web Agent’s webagent.ini file by setting the following parameter:
DomainCookie=<domain>
where <domain> is the same domain (for example, test.com) for the CA SSO and CA SiteMinder® Web Agents.
The file is installed in the following location on the WAC Web Agent machine:
C:\Program Files\CA\WebAccessControl\WebAgent\webagent.ini
- Verify the following Web server and the authentication method settings in the webagent.ini file:
CA SSO Policy Manager Verification Steps
- Ensure that the CA SiteMinder® and CA SSO Policy Servers to use the same user or authentication store.
- Make sure you have the following:
- CA SiteMinder® Policy Server Configuration Steps
-
- Create a Web Agent, Agent Configuration Object, and Host Configuration Object using the Administrative UI. For more information, see the Policy Server Installation Guide and the Web Agent Installation Guide.
- Configure the CA SiteMinder® and CA SSO Policy Servers to use the same user or authentication store.
For CA SiteMinder® user store configuration instructions, see the User Directories chapter in this guide.
For the CA SSO authentication store, see the CA SSO documentation.
- Configure an smetssocookie (certificate) custom active response.
- Create a domain, realm, and rules using the Administrative UI to protect any resource with the CA SiteMinder® Web Agent.
Note: When creating the rules, append the smetssocookie custom active response to them.
Overall Verification Steps
- Configure the user with credentials to access resources protected by the CA SiteMinder® Web Agent and the WAC Web Agent.
- Restart the CA SiteMinder® Policy Server and Web server hosting the Administrative UI.
- Access the resource protected by the CA SiteMinder® Web Agent and provide this Web Agent with the appropriate user credentials.
- After gaining access to this resource, in the same browser session, request a resource protected by the WAC Web Agent.
You should gain access to this resource without being prompted for credentials.
More information:
WebAgent.conf File Locations
Realms
Rules
Domains
Configure Single Sign-On from CA SSO Client to SiteMinder
CA SiteMinder® provides single sign-on from the CA SSO Client to CA SiteMinder®.
To enable single sign-on from an CA SSO Client to CA SiteMinder®:
CA SiteMinder® Policy Server Configuration Steps
- Configure the smauthetsso custom authentication scheme using the Administrative UI.
- Create a domain, realm, and rules using the Administrative UI to protect any resource with the CA SiteMinder® Web Agent.
- Configure the smauthetsso custom authentication scheme to protect a resource.
- Create a policy that grants access to the protected resource to users who already have access the browser protected by the CA SSO Client.
CA SSO Client Verification Steps
Set the following in the CA SSO Client SsoClnt.ini file:
Note: The SsoClnt.ini file is installed in C:\Program Files\CA\CA SSO\Client on the CA SSO Client machine. More information on configuring the CA SSO Client exists in the CA SSO documentation.
DomainNameServer=<eSSO_WA_FQDN> <SM_WA_FQDN>
- eSSO_WA_FQDN
-
(Optional) Specifies the fully qualified domain name for the WAC Web Agent
- SM_WA_FQDN
-
Specifies the fully qualified name for the CA SiteMinder® Web Agent
Overall Verification Steps
- Restart the CA SSO Client, CA SiteMinder® Policy Server, and Web server hosting the Administrative UI.
- Access the protected browser through the SSO Client and enter the URL of the resource protected by the CA SiteMinder® Policy Server.
You should be able to access the resource without being rechallenged by CA SiteMinder®.
More information:
Realms
Rules
Domains
Configure Single Sign-On from CA SSO to SiteMinder
CA SiteMinder® provides single sign-on from CA SSO to CA SiteMinder®.
To enable single sign-on from CA SSO to CA SiteMinder®
CA SiteMinder® Policy Server Configuration Steps
- Configure the smauthetsso custom authentication scheme using the Administrative UI.
- Create a domain, realm, and rules using the Administrative UI to protect any resource with the CA SiteMinder® Web Agent.
For more information, see Domains, Grouping Resources in Realms, or Rules.
- Configure the smauthetsso custom authentication scheme to protect a resource.
WAC Web Agent Verification Steps
- Configure the domain in the WAC Web Agent’s webagent.ini file by setting DomainCookie=<domain>.
Note: The value you specify for the domain must be the same for the CA SSO and CA SiteMinder® Web Agents. The file is installed on the WAC Web Agent machine at C:\Program Files\CA\WebAccessControl\WebAgent\webagent.ini
- Verify the following Web server and the authentication method settings in the webagent.ini file:
- The "Authentication methods" and "The default authentication method" parameters should be configured as SSO.
- The WebServerName, PrimaryWebServerName, AgentName, NTLMPath and Secure should point to the machine where SSO Web Access Control is installed.
- The ServerName attribute should point to the IP Address of the machine where the CA SSO Policy Server is installed.
- For more information about configuring the WAC Web Agent, see the CA SSO documentation.
Note: For more information about configuring the WAC Web Agent, see the WAC documentation.
CA SiteMinder® Web Agent or CA SiteMinder® SPS Configuration Steps:
- Enable the SSO plug-in installed with the Web Agent or CA SiteMinder® SPS, so that SSO Client cookies can be authenticated, by removing the comment character (#) from the following line in the WebAgent.conf file:
#LoadPlugin=path_to_eTSSOPlugin.dll | path_to_libetssoplugin.so
Note: The WebAgent.conf file is located as follows:
- 12.52 IIS 6.0 or Apache 2.0 Web Agent
-
See the Web Agent Configuration Guide.
- 6.0 CA SiteMinder® SPS
-
SPS_install_dir\proxy-engine\conf\defaultagent\
SPS_install_dir
CA SiteMinder® SPS installation directory
- Restart the Policy Server.
Overall Verification Steps
- Restart the WAC Web Agent, CA SiteMinder® Policy Server, and Web server hosting the Administrative UI.
- Access a resource protected by the WAC Web Agent and provide valid credentials.
- Access a resource protected by the CA SiteMinder® Web Agent in the same browser.
You should be able to access the resource without being rechallenged by CA SiteMinder®.
Configure an smetssocookie Web Agent Active Response Attribute
The smetssocookie Web Agent active response generates and sends an SSO cookie to a Web browser. The SSO cookie lets a CA SiteMinder®-authenticated user access WAC or CA SSO protected content without having to reauthenticate.
To configure an smetssocookie Web Agent response attribute
- Click Policies, Domain.
- Click Responses.
The Responses page appears.
- Click Create Response.
The Create Response: Select Domain page appears.
- Select a domain from the list and click Next.
The Create Response: Define Response page appears.
- Define a Name and Description for the response.
- Verify that the CA SiteMinder® is selected and that Web Agent appears in the Agent Type list.
- Click Create Response Attribute.
The Create Response Attribute page appears.
- Verify that Create a new object is selected, and then click OK.
The Create Response Attribute: Name page appears.
- Select WebAgent-HTTP-Cookie-Variable from the Attribute list.
- Select Active Response in Attribute Kind.
Additional fields appear in Attribute Fields.
- In the Cookie Name field, type SSOTK.
- In the Library Name field, type smetssocookie.
- In the Function Name field, type GenEtssoCookie.
Note: The function name is case-sensitive.
- In the Parameters field, define the following ordered set of tokens :
<CA_PS_Host_Name>;<SSO_Auth_Host>;<SSO_AuthMethod>;<EncryptionKey>
- CA_PS_Host_Name
-
Specifies the host name of the CA SSO Policy Server.
- SSO_Auth_Host
-
Specifies the SSO authentication host name in the CA Policy Manager. You can specify this host name by going to Web Access Control Resources, Configuration Resources, Authentication Host.
Required value: SSO_Authhost
- SSO_AuthMethod
-
Defines the SSO authentication method.
Required value: SSO
- EncryptionKey
-
Defines the ticket encryption key for the SSO authentication host name in the CA Policy Manager.
The cookie script appears in the Script field.
Note: To improve legibility, you can type a space before and after any token.
- Click Submit.
The Create Response Attribute task is submitted for processing, and the Create Response: Define Response page re-appears.
- Click Finish.
The Create Response task is submitted for processing. When the task is complete, the response can be added to an OnAuthAccept rule.
Configure an smauthetsso Custom Authentication Scheme
The CA SSO CA SiteMinder® (smauthetsso) authentication scheme lets the CA SiteMinder® Policy Server validate CA SSO authentication credentials so that a user already authenticated in a CA SSO/WAC environment does not need to re-authenticate to CA SiteMinder®. This custom authentication scheme accepts a CA SSO Cookie as a login credential; has it validated by a CA SSO Policy Server; extracts the user name from it; and verifies that the name is present in the CA SiteMinder® user store. You can set this authentication scheme in a cookie, cookieorbasic, or cookieorforms mode.
You can configure one CA SSO Policy Server to failover to another CA SSO Policy Server when it fails for some reason. To configure failover, specify a comma-separated list of CA SSO Policy Servers as parameter field in Scheme Setup on the Authentication Scheme page.
Note: The following procedure assumes that you are creating an object. You can also copy the properties of an existing object to create an object. For more information, see Duplicate Policy Server Objects.
Follow these steps:
- Click Infrastructure, Authentication.
- Click Authentication Schemes.
The Authentication Schemes page appears.
- Click Create Authentication Scheme.
Verify that the Create a new object of type Authentication Scheme is selected.
- Click OK
The Create Authentication Scheme page appears.
Note: Click Help for descriptions of settings and controls, including their respective requirements and limits.
- Select Custom Template from the Authentication Scheme Type list.
Scheme-specific fields and controls open.
Note: Click Help for descriptions of settings and controls, including their respective requirements and limits.
- Enter smauthetsso in the Library field.
- Enter and confirm the password of the CA SSO Policy Server administrator in the Secret and Confirm Secret fields.
- Define an ordered set of tokens in the Parameter field with the following format:
Mode [; <Target>] ; AdminID ; CAPS_Host ; FIPS_Mode ; Identity_File
Note: Separate tokens with semicolons. You may enter a space before and after each token for improved legibility.
Example: cookie ; SMPS_sso ; myserver.myco.com ; 0 ; /certificates/def_root.pem
Example: cookieorforms ; /siteminderagent/forms/login.fcc ; SMPS_sso ; myserver.myco.com ; 1 ; /certificates/def_root.pem
- Mode
-
Specifies the type of credentials the authentication scheme accepts. Accepted values include cookie, cookieorbasic, or cookieorforms.
- cookie
-
Specifies that only CA SSO cookies are acceptable.
- cookieorbasic
-
Specifies that a basic authentication scheme is used to determine the login name and password if a CA SSO cookie is not provided.
- cookieorforms
-
Specifies that a forms authentication scheme is used to determine the login name and password if a CA SSO cookie is not provided.
- Target
-
Specifies the pathname of the .fcc file used by the HTML Forms authentication scheme.
Note: This value is only required for the cookieorforms mode.
- AdminID
-
Specifies the user name of the CA SSO Policy Server administrator for the CA SSO Policy Server. CA SiteMinder® uses the administrator’s user name and password to request validation of CA SSO cookies when authenticating to the CA SSO Policy Server.
- CAPS_Host
-
Specifies the name of the host where the CA SSO Policy Server resides.
- FIPS_Mode
-
Specifies the FIPS mode of operation in which the Policy Server is operating. Zero (0) specifies non-FIPS mode. One (1) specifies FIPS mode.
- Identity_File
-
Specifies the path to the CA SSO identity file. The Policy Server uses this file to communicate with the CA SSO Policy Server.
- Click Submit.
The authentication scheme is saved and can be assigned to a realm.
CA User Activity Reporting Module Integration
CA User Activity Reporting Module (CA UAR) provides CA SiteMinder® connector guides, which detail how to configure a CA UAR integration with CA SiteMinder®. The guide you use depends on whether CA SiteMinder® is configured to store audit information in a text file (smaccess.log) or an ODBC database.
To locate the CA UAR connector guides
- Go to the CA User Activity Reporting Module Integration Matrix.
- Click Authentication Service that is located under Product Integrations.
The CA SiteMinder® connector guides are based on the type of logsensor that CA UAR is to use.
- Do one of the following:
- If CA SiteMinder® stores audit information in a text file, use the connector guide for a File logsensor.
- If CA SiteMinder® stores audit information in an ODBC database, use the connector guide for an ODBC logsensor.
Each of these guides is also available from the CA UAR Administrative UI when you create the required connector. To access these guides when creating the connector, click Help.
Copyright © 2013 CA.
All rights reserved.
 
|
|




