

Link security limits a remote system's authorization to attach your transactions and access your resources. Each time a request is made to access a remote resource, a security check is performed against the userid defined in the session definition or the CICS TOR userid, if userid is omitted. Since security calls are being made against the link, the CICS region userid for the link must have permission to these resources, or have the NORESCHK and NOLCFCHK attributes defined to the ACID.
No signon for the link takes place if the requesting system passes a userid that matches the receiving CICS region's userid. Therefore, if you want to apply effective link security, the userid on one side of an MRO link must not match the userid on the other side.
It is suggested that MRO region ACIDs be set up with the following attributes:
Since these CICS region ACIDs are usually created without a password so that the operator does not have to enter the password when the region is started, the CICS region ACID might be compromised. To prevent a user signing on with the CICS region ACID as a user on a facility to which it is authorized, the SOURCE(INTRDR) restriction is recommended. The NORESCHK and NOLCFCHK attributes are necessary because of LINK SECURITY considerations. NOSUBCHK is necessary for correct handling of job submission.
Link security works by signing on to each end of a session (via receive terminals) using the userid specified on the SESSION definition or, if omitted, the default user.
The following figure shows how to define link security for both MRO and ISC connections
RDO definition DEFINE SESSION CONNECTION(connect) USERID(userid)
An example of how link security works in MRO and ISC connections is shown in the following figure.
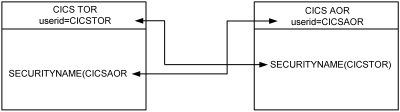
The SESSION ACID should not be identical across the link or the signon is not performed and the link will fail. The SESSION ACID provides a focal point to decide if individual remote transactions and resources are permitted to the local region. For the purpose of link security, the region's permission for remote resources is represented as the SESSION USERID. This user‑acid can be modeled similar to the remote region ACID, but might have more stringent restrictions than the region ACID to prevent specific types of access by all users signed on to the region.
In the previous example, the PAY transaction is being routed to the AOR. Before the transaction is initiated, CA Top Secret issues a link security check against the CICS region ACID specified in the SECURITYNAME definition as CICSTOR. This security check determines if the PAY transaction can run in the AOR region.
The PAY transaction (depending on the mode) is not able to execute in the AOR region if the CICS SESSION ACID USER1:
Link security is checked at the time a remote transaction is about to be executed, or when a remote resource is about to be attached. Link security involves not only the CONNECTION (DFHTCT TYPE=SYSTEM), but also the SESSION definition (DFHTCT TYPE= ).
RDO definition RDM definition DEFINE SESSION ( ) DFHTCT TYPE= ( )
Link security limits the originating region's authorization to attach local transactions and to access local resources. The following CONNECTION considerations are important for link security:
The following SESSION considerations are important for link security:
Specifying other values will cause link security to avoid signon for the originating region ACID. Link security will then default to the destination region ACID with often paradoxical results.
|
Copyright © 2014 CA Technologies.
All rights reserved.
|
|