

The smkeydatabase is a key and certificate database used for signing, verification, encryption, and decryption between a SiteMinder asserting party and a SiteMinder relying party. The database is made up of multiple files. You can manage and retrieve keys and certificates in this database using the SiteMinder tool called smkeytool.
The smkeydatabase can store multiple private keys and certificates. If you have multiple federated partners, you can use a different private key for each partner. Every certificate or key/certificate pair must have a unique alias. The alias enables you to reference any single certificate or key/certificate pair in the smkeydatabase.
If a signing alias is configured, SiteMinder uses the key associated with that alias to sign assertions. If no signing alias is configured, SiteMinder uses the key with the alias defaultenterpriseprivatekey to sign assertions. If there is no default enterprise private key found, then SiteMinder uses the first private key that it finds in the database to sign assertions.
Important! To store multiple keys in the database, you must define the first key you add with the alias defaultenterpriseprivatekey before you can add subsequent keys.
A given Policy Server may sign and/or verify responses. Keys and certificates for signing and validation can be added to the same key database, depending on what the Policy Server is doing. For single sign-on, if a site is only consuming assertions using SAML POST profile, then that consumer/Service Provider only verifies the response; it never signs it. In the case of single logout, it depends upon which site initiates the single logout that determines which side signs or verifies requests and responses.
The smkeydatabase is installed with a SiteMinder Policy Server. The Policy Server uses certified Federal Information Processing Standard (FIPS) 140-2 compliant cryptographic libraries, which enables a SiteMinder environment to use FIPS-compliant algorithms to encrypt sensitive data. As a result, all data in the smkeydatabase is encrypted using these FIPS-compliant algorithms.
Note: If you upgrade from a previous version of the Policy Server to r12.0 SP3, see the SiteMinder Upgrade Guide for instructions on migrating the smkeydatabase so that data is properly encrypted.
The following illustration shows the location of the key store in a SiteMinder federated network.
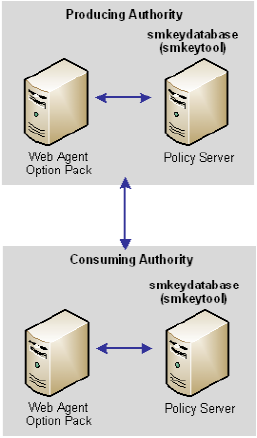
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
|
Copyright © 2012 CA.
All rights reserved.
|
|