

Federation Security Services Guide › Configure SiteMinder as a SAML 1.x Consumer › SAML 1.x Authentication Schemes
SAML 1.x Authentication Schemes
A consumer is a site that uses a SAML 1.x assertion to authenticate a user.
Note: A site can be a SAML producer and a SAML consumer.
Any SiteMinder site with Federation Security Services functionality can consume SAML 1.x assertions and can use these assertions to authenticate users. When an assertion is consumed, the site has to be able to compare the information from the assertion against a user directory to complete the authentication process.
SiteMinder provides the following SAML 1.x authentication methods:
- SAML Artifact profile
- SAML POST profile
The SAML-based authentication schemes let a consumer site authenticate a user. Consuming a SAML assertion and establishing a SiteMinder session enables cross-domain single sign-on. After the user is identified, the consumer site can authorize the user for specific resources.
The following illustration shows the major components for authentication at the consumer site.
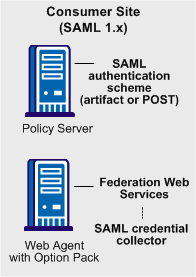
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The SAML 1.x authentication scheme is configured at the consumer-side Policy Server. The SAML credential collector is a component of the Federation Web Services application. The credential collector is installed on the consumer-side Web Agent, or on an SPS federation gateway. The credential collector obtains information from the SAML authentication scheme at the Policy Server, then uses that information to access a SAML assertion.
The SAML assertion becomes the credentials that grant access to the Policy Server at the consumer site. The user is authenticated and authorized, and if authorization is successful, the user is redirected to the target resource.
SAML 1.x Artifact Authentication Scheme Overview
The following illustration shows how the SAML 1.x artifact authentication scheme processes requests.
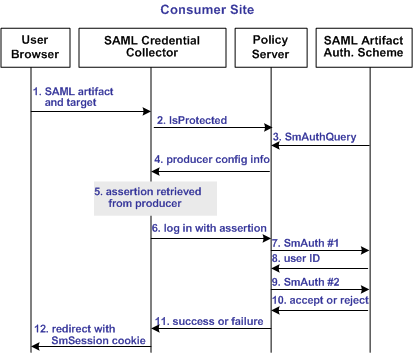
Note: An SPS federation gateway, or the Web Agent and Web Agent Option Pack, provide the Agent and SAML Credential Collector functionality.
Unless otherwise stated, all activity in this process occurs at the Consumer site:
- A user is redirected to the SAML credential collector with a SAML artifact and a target URL.
The artifact and target URL are originally generated from the Web Agent at the producer site.
- The SAML credential collector calls the Policy Server to determine whether the SAML artifact authentication scheme protects the requested resource.
- The Policy Server passes the necessary data to the SAML artifact authentication scheme, which extracts the producer configuration information.
- The Policy Server returns the producer configuration information to the SAML credential collector. This information enables the credential collector servlet to call a producer site and retrieve a SAML assertion.
- The SAML credential collector takes the data from the Policy Server and uses it to retrieve the SAML assertion.
- Once an assertion is returned, the credential collector uses the assertion as credentials, and logs in to the Policy Server.
- The Policy Server makes the initial user disambiguation call to the SAML authentication scheme.
- Using the authentication scheme data and the assertion, the scheme locates the user and returns a unique identifier for the user to the credential collector.
- The Policy Server makes the second user authentication call to the authentication scheme.
Note: The SiteMinder Authentication AP dictate the two-step authentication process. For more information, see the SiteMinder Programming Guide for C or the SiteMinder Programming Guide for Java.
- The scheme validates the SAML assertion and returns an accept or reject message to the Policy Server.
- The Policy Server sends the accept or reject message to the credential collector.
- The SAML credential collector creates a session cookie and places it in the browser, and then redirects the user to the target resource. If the login fails, the credential collector redirects the user to a No Access URL.
SAML 1.x POST Profile Authentication Scheme Overview
The following illustration shows how the SAML 1.x POST profile authentication scheme processes requests.
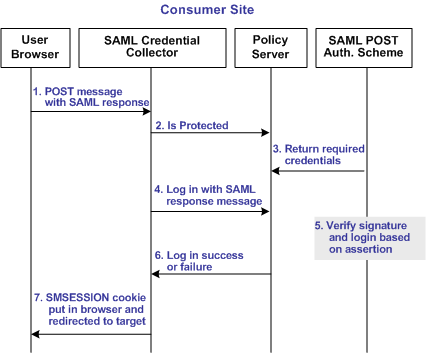
Note: The SPS federation gateway or the Web Agent Option Pack provide the SAML Credential Collector functionality.
Unless otherwise stated, the following process takes place at the consumer site:
- A browser posts an HTML form to the SAML credential collector URL. This form contains a SAML response message and the address of the target URL, originally generated at the producer.
- The SAML credential collector contacts the Policy Server to determine whether the target resource is protected.
- The Policy Server replies that the SAML POST profile authentication scheme protects the target URL. A signed response from the posted form is the expected credential for the login call.
- The SAML credential collector makes a login call to the Policy Server, passing the digitally signed SAML response as credentials.
- The SAML POST profile authentication scheme verifies the signature and other fields of the response and the assertion.
- If the checks succeed and the user is found in the directory, then authentication succeeds. If any of the checks fail, authentication fails.
- The SAML credential collector creates an SMSESSION cookie. This cookie is put in the browser and the user is redirected to the target resource. If the login fails, the credential collector redirects the user to the configured No Access URL.
Copyright © 2012 CA.
All rights reserved.
 
|
|




