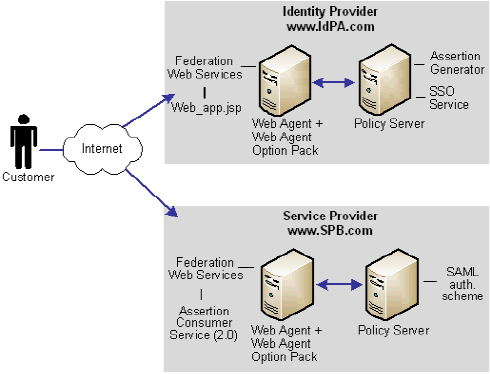
Solution 12 shows how SiteMinder Federation Security Services can be deployed at IdPA.com and SPB.com to solve Use Case 12.
SiteMinder is deployed at both sites by installing the Web Agent with the Web Agent Option pack on one machine, and the Policy Server on another machine.
In the following illustration, IdPA.com is the Identity Provider and SPB.com is the Service Provider and single sign-on is initiated at the Identity Provider.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the SiteMinder Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the CA SiteMinder Secure Proxy Server Administration Guide.
For IdP-initiated single sign-on, the sequence of events is as follows
Important! When the user goes to the SSO Service first, several query parameters (SPID, ProtocolBinding, RelayState) are included with the original SSO request. The SSO service groups this query data into one query parameter called SMPORTALSTATE, and then redirects the user (via a GET) to the web application.
Note: After the user is locally authenticated at the IdP, he is never redirected to the Authentication URL as long as he has a valid session.
Important! If the user starts at the SSO Service, and is redirected to the web application with the SMPORTALSTATE query parameter, the web application must POST the SMPORTALSTATE query parameter and the collected attributes back to the SSO Service.
Important! The SSO Service makes all the attributes available to the Assertion Generator, but an Assertion Generator plug-in must be written and configured to add the attributes to the assertion.
For SP-initiated single sign-on:
Note: In the case of SP-initiated single sign-on, the request must arrive at the SSO service directly from the SP, as dictated by SAML specifications. The user cannot go directly to the web application.
Important! When the user is directed to the SSO Service, several query parameters (SPID, ProtocolBinding, RelayState) are included with the original SSO request. The SSO service groups this query data into one query parameter called SMPORTALSTATE, and then redirects the user (via a GET) to the web application.
Important! The web application must maintain and POST the SMPORTALSTATE query parameter and the collected attributes back to the SSO Service.
Note: An Assertion Generator plug-in must be written and configured to add the attributes to the assertion.
| Copyright © 2010 CA. All rights reserved. | Email CA about this topic |