Solution 11 illustrates how you can set up a parallel web application and federation environments to solve Use Case 11.
SiteMinder's security zones can be used to eliminate the need for persistent user sessions associated with every request for applications protected by the SAML 1.x or SAML 2.0 artifact profiles.
A security zone is a segment of a single cookie domain, used as a method of partitioning applications to assign different security requirements. Security zones are implemented by Web Agents and can be configured for the producer-side Web Agents that are protecting the requested federated resources.
The following figure illustrates a deployment that uses two different SiteMinder environments at a single producing authority site. One SiteMinder environment is for federation functionality and the other is for web application protection.
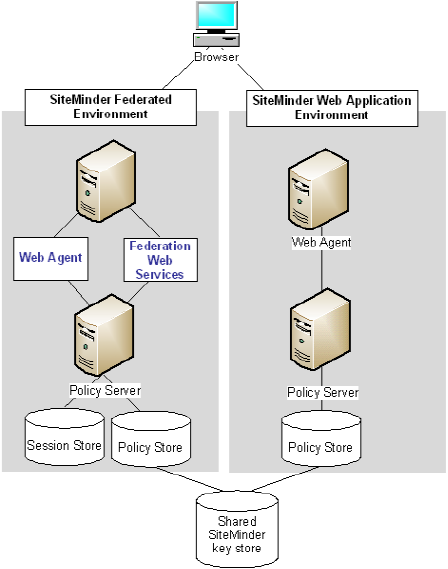
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the SiteMinder Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the CA SiteMinder Secure Proxy Server Administration Guide.
The figure reflects the following set up:
Web application environment
|
Agent Configuration Object or Local Configuration File |
Trusted Security Zones |
Cookies that Can be Read by the Web Agent for the Zone |
|---|---|---|
|
DefaultAgent |
SM (default)--primary zone |
The DefaultAgent configuration enables the Web Agent to read and write the default session cookie, SMSESSION and is backwards compatible with SiteMinder 5.x. |
Federation Environment
|
Agent Configuration Object or Local Configuration File |
Trusted Security Zones |
Cookies that Can be Read by the Web Agent for the Zone |
|---|---|---|
|
FedWA used by the Web Agent |
FED--primary zone SM--additionally accepted zone |
The FedWA configuration enables the Web Agent to read and write SESSIONSIGNOUT cookies, and read SMSESSION cookies. |
|
FedFWS used by the FWS application |
FED--primary zone only |
Configures the FWS to read and write SESSIONSIGNOUT cookies. |
All resources protected in the Web application environment use non-persistent user sessions. As a result, when users are authenticated and authorized, the SMSESSION cookie contains a non-persistent user session specification. The non-persistent session specification ensures that requests to web applications do not incur the performance penalty of calling the session server.
When the Web Agent in the federation environment receives a request, this request is directed to the Authentication URL to establish a user session. This user already has an SMSESSION cookie established by a prior authentication in the Web application environment, but the user has no SESSIONSIGNOUT cookie.
The Authentication URL, which authenticates users federating to a partner site, is protected by a persistent user session in the federation environment. This is why the Web Agent in the federation environment writes a SESSIONSIGNOUT cookie with a persistent user session specification and with the same session ID as the SMSESSION cookie.
The Web Agent in the federation environment reads the SMSESSION cookie and writes a SESSIONSIGNOUT cookie in accordance with the security zones associated with the FedWA configuration.
The FWS application in the federation environment reads the SESSIONSIGNOUT cookie. This cookie contains a persistent user session, therefore, a call to the session server is not necessary. The FWS application can successfully process federation requests that requires a persistent user session.
| Copyright © 2010 CA. All rights reserved. | Email CA about this topic |