In use case 12, an Identity Provider, IdPA.com, wants to include attributes in an assertion that are from a Web application. This use case is only applicable to SAML 2.0 deployments.
For this use case, single sign-on can be initiated at the Identity Provider or the Service Provider. The protocols IdPA.com uses is SAML 2.0 (POST and Artifact) and WS-Federation.
The following figure shows an example of attributes gathered from a Web application and used for single sign-on.
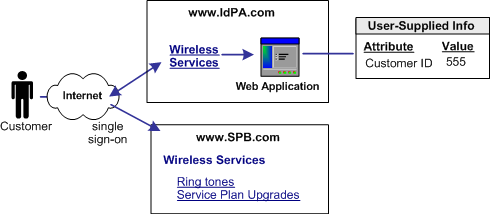
IdP-initiated Single Sign-on with Web Application Attributes
IdPA.com has created a Web application for access to protected resources at its business partner SPB.com. When the customer logs in at IdPA.com, they click on a link for the business partner and they are sent to the Web application, where they are prompted to enter a customer ID. This information needs to be sent to SPB.com so that the customer is permitted access to the appropriate services.
SP-initiated Single Sign-on with Web Application Attributes
A customer has clicked on a link at SPB.com, the Service Provider. This link is for protected resources, so he is redirected to IdpA.com to be authenticated. After the user successfully authenticates at IdPA.com, he is redirected to the Web application where he provides specific user information. Upon submitting the information, the customer is sent back to SPB.com to complete single sign-on for the requested resource.
| Copyright © 2010 CA. All rights reserved. | Email CA about this topic |