

The procedure for enabling Secure Sockets Layer (SSL) communications on the CA SiteMinder® Agent for SharePoint has the following parts:
The following graphic describes these procedures:
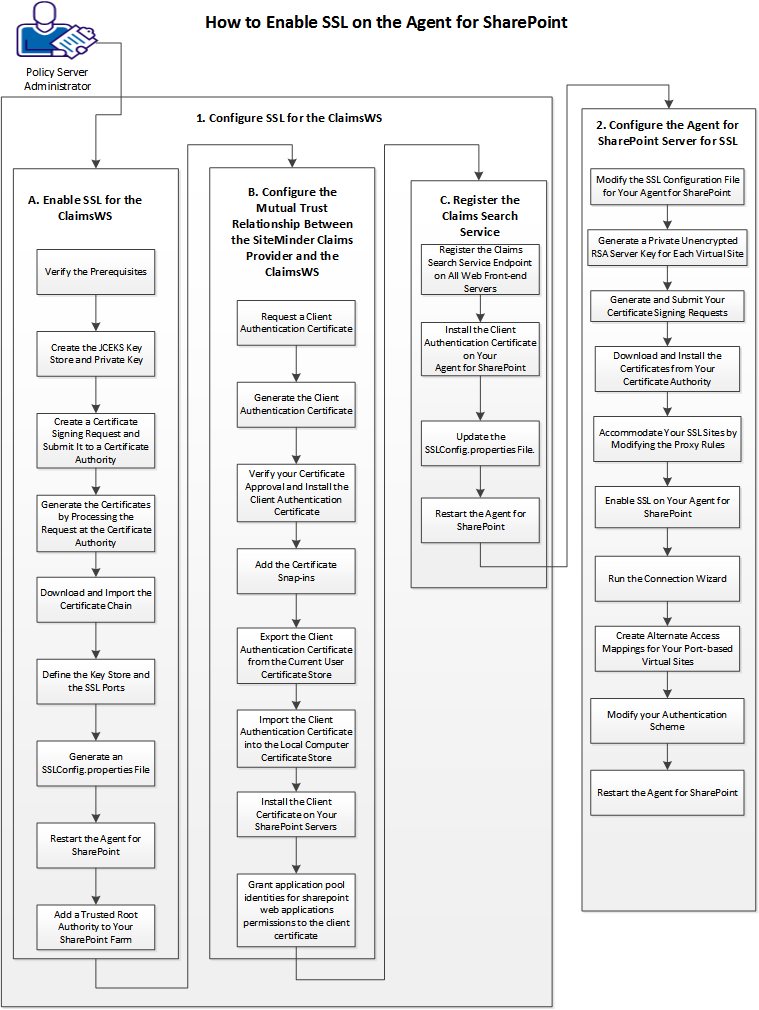
Follow these steps:
The first step in protecting the ClaimsWS service is verifying the prerequiites.
Verify the following prerequisites before protecting the Claims WS service with SSL:
Agent-for-SharePoint_home\ca_sps_env.sh
The next step in protecting the ClaimsWS service is creating a JCEKS key store and private key.
The JCEKS key store is a repository for the certificates and their related private keys. The certificates that you create are stored in the JCEKS key store. Creating a key store also creates a server certificate. This process requires the following information:
Follow these steps:
Agent_for_SharePoint_home\SSL\keys
Indicates the directory where the CA SiteMinder® Agent for SharePoint is installed.
Default: (Windows) [32-bit] C:\Program Files\CA\Agent-for-SharePoint
Default: (Windows) [64-bit] C:\CA\Agent-for-SharePoint
Default: (UNIX/Linux) /opt/CA/Agent-for-SharePoint
keytool -genkeypair -keyalg RSA -keystore .\ServerCert.jceks -alias Alias_Name -storetype JCEKS -storepass keystore_password
The following table lists the prompts from the JCEKS keytool utility and sample responses:
|
Keytool Prompt: |
Sample Response: |
Purpose: |
|
What is your First and Last Name? |
agentforsharepointserver.example.com |
Fully qualified domain name (FQDN) of the server hosting your CA SiteMinder® Agent for SharePoint. |
|
What is your Organizational Unit? |
support |
Department or group name |
|
What is your Organization? |
example |
Name of your organization |
|
What is your City or Locality? |
Your City |
City or Town |
|
What is your State? |
YS |
Two-letter state or province abbreviation |
|
What is your Country Code? |
YC |
Two-letter country code |
The keytool utility displays a confirmation resembling the following example:
Is the following correct: cn=agentforsharepointserver.example.com,ou=support,o=example,l=Your City,st=YS,c=YC
The keystore and private key are created.
The next step in protecting the ClaimsWS service involves creating a certificate signing request for the server certificate in your JCEKS key store.
A signing request submits the certificate to a certificate authority. The certificate authority validates (signs) the certificate. Certificates that are signed third-party certificate authorities are considered more secure than self-signed certificates.
Self-singed certificates are acceptable for evaluation or testing environments.
To submit a certificate signing request, you need the following information:
Follow these steps:
keytool -certreq -v -alias Alias_Name -sigalg MD5withRSA -file .\file_name_of_certificate_request.csr -keypass keystore_password -keystore ServerCert.jceks -storepass keystore_password -storetype JCEKS
The keytool utility produces a certificate signing request similar to the following example:
-----BEGIN NEW CERTIFICATE REQUEST----- MIIBrzCCARgCAQAwbzELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAk1BMRMwEQYDVQQHEwpGcmFtaW5n aGFtMQswCQYDVQQKEwJDQTEPMA0GA1UECxMGU01URVNUMSAwHgYDVQQDExdzbXNwczIwMTAuc210 ... ... ... dsrZKqtNaqym7DrkSql7LsUGcsACUp1K4PU6t3P16CKvagspJ18zwTqTRpkGtbu6emvEwpcQveuW k27YooCZ4XDzFxtpAnv9EIl7L4N4QHHxXCa8kIULOdGtJ4vD -----END NEW CERTIFICATE REQUEST-----
Note: This procedure demonstrates submitting a request to a Microsoft Active Directory Certificate Services certificate authority.
https://fully_qualilfied_domain_name_of_server_running_active_directory_certificate_services/certsrv
Note: An example of such a URL is http://certificateauthority.example.com/certsrv.
Note: Under the type of certificate needed drop-down list, verify that Client Authentication Certificate appears.
A confirmation dialog appears.
The request is submitted. Note your request ID for future reference.
The next step in protecting the ClaimsWS service is having a certificate authority process your request.
After the certificate authority receives your certificate signing request, they will process the request and will return the signed certificate.
Some organizations use third-party certificate authorities to sign their certificate requests. Other organizations could possibly have an internal group that operates a certificate authority.
The following procedure demonstrates the process for approving a certificate with Microsoft Active Directory Certificate services:
Certificate administrators approve or reject certificate requests. Certificate administrator privileges are separate from the Administrator privileges in the Windows operating environment. Not all users who have accounts on the computer hosting Active Directory Certificate services have sufficient privileges to approve or reject certificates.
Use this procedure if you have certificate administrator privileges. Otherwise, ask the certificate administrator in your organization to issue the certificate for you.
Follow these steps:
The certsrv snap-in appears.
A list of pending certificate requests appears.
The certificate is issued. Continue with the next step of downloading and importing the certificate.
The next step in protecting the ClaimsWS service is downloading and importing the certificate chain.
After your certificate has been signed, download and install the following items to the server hosting your CA SiteMinder® Agent for SharePoint:
The certificate chain validates your certificate to the web browsers of your users.
This process requires the following information:
Follow these steps:
Agent_for_SharePoint_home/SSL/keys
keytool -importcert -v -noprompt -alias Alias_Name -file .\certnew.p7b -keypass keystore_password -keystore ServerCert.jceks -storepass keystore_password -storetype JCEKS
The next step in protecting the ClaimsWS service is defining the key store and SSL ports.
After downloading and importing the certificate chain to the server hosing the CA SiteMinder® Agent for SharePoint, add the following settings:
These settings are defined in the server.conf file.
Follow these steps:
Agent_for_SharePoint_home\proxy-engine\conf\server.conf
Locate the following section of the file:
<localapp>
#local.https.port=port_number
local.https.port=2525
#local.https.keyStoreFileName="tomcat.keystore"
local.https.keyStoreFileName="ServerCert.jceks"
The next step of protecting the ClaimsWS service involves generating an SSLConfig.properties file for the keystore.
Follow these steps:
GenerateSSLConfig -keystorepass keystore_password
Important! Do not enable client authentication yet.
Starting or stopping the CA SiteMinder® Agent for SharePoint involves the following separate procedures:
Change the value of the EnableWebAgent parameter to accomplish either of the following tasks:
Follow these steps:
Agent-for-SharePoint_home\proxy-engine\conf\defaultagent\WebAgent.conf
EnableWebAgent="NO"
You can change the states of the related services on your CA SiteMinder® Agent for SharePoint.
Note: To start or stop your CA SiteMinder® Agent for SharePoint, change the value of the EnableWebAgent parameter first.
Follow these steps:
The Services dialog appears.
The states of the services and CA SiteMinder® Agent for SharePoint are changed.
Agent-for-SharePoint_home/proxy-engine
./sps-ctl start
The service and the CA SiteMinder® Agent for SharePoint start. The CA SiteMinder® Agent for SharePoint stops or starts according to the value you set in the EnableWebAgent parameter.
Agent-for-SharePoint_home/proxy-engine
./sps-ctl stop
The service and the CA SiteMinder® Agent for SharePoint stop.
The next step in protecting the ClaimsWS service is adding a trusted root authority to your SharePoint farm.
Your SharePoint farm requires a new trusted root authority to identify and authenticate the information that it receives from the claims service. Create a trusted root authority on your SharePoint 2010 central administration server.
Follow these steps:
The Create Trusted Relationship dialog appears.
The trusted root authority is created.
A mutual trust relationship between the following components is required for secure communications:
The first step in creating this relationship is requesting a client authenticate certificate. This certificate is installed on all SharePoint web front-end (WFE) servers. The client authentication certificate allows the ClaimsWS service to verify the identities of the WFE servers.
Several third-party tools are available for creating certificates. This procedure provides one possible example using Active Directory Certificate services and IIS 7.
If your organization uses different tools or procedures to create client certificates, use those tools or procedures instead.
If you already have a client authentication certificate, skip this procedure.
Follow these steps:
https://fully_qualilfied_domain_name_of_server_running_active_directory_certificate_services/certsrv
An example of such a URL is http://certificateauthority.example.com/certsrv.
The Request a certificate screen appears.
An Advanced Certificate Request form appears.
Name: SiteMinderClaimsProvider E-Mail: admin@support.example.com Company: Example Department: Support City: your_city State: your_state Country/Region your_country Type of Certificate Needed: Client Authentication Certificate Mark keys as exportable: ENABLED Friendly Name: SiteMinderClaimsProvider
Note: Under the type of certificate needed drop-down list, verify that Client Authentication Certificate appears.
A confirmation dialog appears.
The request is submitted.
The next step in configuring a mutual trust relationship between the claims search service and the claims provider is generating the client authentication certificate.
The next step in protecting the ClaimsWS service is having a certificate authority process your request.
After the certificate authority receives your certificate signing request, they will process the request and will return the signed certificate.
Some organizations use third-party certificate authorities to sign their certificate requests. Other organizations could possibly have an internal group that operates a certificate authority.
The following procedure demonstrates the process for approving a certificate with Microsoft Active Directory Certificate services:
Certificate administrators approve or reject certificate requests. Certificate administrator privileges are separate from the Administrator privileges in the Windows operating environment. Not all users who have accounts on the computer hosting Active Directory Certificate services have sufficient privileges to approve or reject certificates.
Use this procedure if you have certificate administrator privileges. Otherwise, ask the certificate administrator in your organization to issue the certificate for you.
Follow these steps:
The certsrv snap-in appears.
A list of pending certificate requests appears.
The certificate is issued. Continue with the next step of downloading and importing the certificate.
The next step in creating a mutual trust relationship is verifying your approval and installing your client authentication certificate. Your IIS web server must have the client authentication certificate installed first before installing it on any SharePoint central administration or web front-end (WFE) servers.
Verify the status of your certificate request using the same IIS web server and Web browser from which you submitted the request. If your certificate is approved, install the certificate on your IIS web server first.
Follow these steps:
https://fully_qualilfied_domain_name_of_server_running_active_directory_certificate_services/certsrv
An example of such a URL is https://certificateauthority.example.com/certsrv.
A list of your certificate requests appears.
The Certificate Issued screen appears. If it does not, contact the certificate administrator in your organization for more information.
A confirmation dialog appears.
The certificate is installed under My User Account on your IIS web server. Continue with the next step of installing the certificate snap-ins on your IIS web server.
The next step for creating a mutual trust relationship between the Claims WS and the CA SiteMinder® claims provider is adding the certificate snap-ins.
The following accounts on your IIS web server require the certificate snap-in:
Follow these steps:
The Run dialog appears.
The Microsoft Management console appears.
The Add or Remove Snap-ins dialog appears.
The Certificates snap-in dialog appears.
The Certificates snap-in dialog closes. The Certificates snap-in appears in the Selected snap-ins list.
The Certificates snap-in dialog appears.
The Add or Remove Snap-ins dialog closes. The certificate snap-ins are added.
The next step for creating the mutual trust relationship is exporting the client certificate from the current user certificate store.
The Windows operating environment uses several different locations within the same computer to store certificates. These locations vary depending on the user account type. Installing your client authentication certificate on your IIS web server placed it in the following store:
Export the certificate from the current user certificate store so it can be added to the other certificate stores on the computer.
Follow these steps:
The Run dialog appears.
The Microsoft Management console appears.
A list of certificates appears.
The certificate export wizard opens.
The client certificate is exported. Continue with the next step of importing the certificate into the local computer certificate store.
The next step for creating the mutual trust relationship is importing the client authentication certificate into the local computer certificate store.
Import the client authentication certificate into the following certificate store on your IIS web server.
Follow these steps:
The Run dialog appears.
The certificates folder appears.
The certificate appears.
The next step in establishing the mutual trust relationship is installing the client-authentication certificate on more servers.
Install the client authentication certificate that you exported from your IIS web server on the following servers in your SharePoint environment:
Follow these steps:
The Run dialog appears.
Right-click the certificates folder, and then click All Tasks, Import.
The certificate appears.
The client authentication certificate is installed. Continue with the next step of granting permissions to the application pools.
All application pool identities that are associated with protected SharePoint web applications need read-only permissions to the client authentication certificate. Perform this procedure on all the following servers in your environment:
Follow these steps:
The Run dialog appears.
The Microsoft Management console appears.
The permissions dialog appears.
The permissions are granted. Continue with the next step of registering the claims search service endpoint on all WFE servers.
The next step in establishing the mutual trust relationship is registering the claims search service endpoint on all WFE servers in your SharePoint farm.
Registering a new end point for the claims search service associates the secure connection with the client authentication certificate. A PowerShell script that is installed with the claims provider automates the registration process. Register the new end point for all of the web front end (WFE) servers in your SharePoint environment.
Follow these steps:
SharePointClaimsProvider_directory\scripts\Remove-SMClaimSearchService.ps1 -WebApplication "url_of_SharePoint_web_application"
The following example describes removing the registration of a previous claims search service endpoint for the following web applications:
.\Remove-SMClaimSearchService.ps1 -WebApplication "http://SharePoint_webapplication.support.example.com:8189/"
.\Remove-SMClaimSearchService.ps1 -WebApplication "http://SharePoint_webapplication.support.example.com:8286/"
Specifies the URL associated with a SharePoint web application.
Example: http://SharePoint_webapplication.support.example.com:/ (runs on the default port).
Example: http://SharePoint_webapplication.support.example.com:81/ (runs on port 81).
Example: http://SharePoint_webapplication.support.example.com:82/ (runs on port 82).
Specifies the URL of the claims search service.
Limits: If the claim search service uses SSL, specify the https: protocol.
Example: https://claim_search_service.support.example.com:8002/ClaimsWS/services/WSSharePointClaimsServiceImpl
Specifies the value in the Issued To: field of your client authentication certificate. This client certificate protects the Claims WS (web service).
Example: SiteminderClaimsProvider
SharePointClaimsProvider_directory\scripts
.\Add-SMClaimSearchService.ps1 -WebApplication url_of_web_application url -ClaimSearchService https://claims_search_service_url -EnableSSLClientAuthentication -ClientCertificateName name_in_Issued-To:_field_of_Certificate
The first end point is registered.
.\Add-SMClaimSearchService.ps1 -WebApplication http://SharePoint_webapplication.support.example.com81/ -ClaimSearchService
https://claim_search_service.support.example.com:8002/ClaimsWS/services/WSSharePointClaimsServiceImpl -EnableSSLClientAuthentication
-ClientCertificateName SiteminderClaimsProvider
.\Add-SMClaimSearchService.ps1 -WebApplication http://SharePoint_webapplication.support.example.com:82/ -ClaimSearchService
https://claim_search_service.support.example.com:8002/ClaimsWS/services/WSSharePointClaimsServiceImpl-EnableSSLClientAuthentication
-ClientCertificateName SiteminderClaimsProvider
The claims serach service endpoint is registered. Continue with the next step of creating a trusted store for the root certificate authority certificate.
The server on which your CA SiteMinder® Agent for SharePoint runs also requires a separate trusted store for the root certificate authority certificates. If you use certificates signed by a third-party certificate authority, import the certificate authority certificate signed by the third party into this trusted store. If you are using a self-signed certificate import either the self-signed certificate or the associated public key into this trusted store.
Important! Do not use self-signed certificates in production environments. We recommend using self-signed certificates in test environments only.
Follow these steps:
Note: This procedure provides one possible example of how to configure this feature using third-party tools. CA Technologies did not develop nor provide these tools. These tools are subject to change at any time by the third party without notice. Use this procedure as a guide for configuring this feature in your specific environment. The actual steps that are required in your situation could be different from the steps that are shown here.
Keytool -importcert -alias alias_name -file path_to_root_certificate -trustcacerts -keystore relative_path_to_trusted_store -storepass trusted_store_password -storetype JCEKS
Note: We recommend using a relative location under the Agent-for-SharePoint_home\SSL\keys directory
The next step of the process of creating a mutual trust relationship is updating the SSLConfig.properties file.
The server that runs your CA SiteMinder® Agent for SharePoint requires a password-protected location (trust store) for the client authentication certificate. Specify a password for the trust store when creating it.
Follow these steps:
GenerateSSLConfig -keystorepass keystore_password -truststore TrustStore.jceks -truststorepass truststore_password
A confirmation prompt for your trust store password appears.
A confirmation prompt for client authentication appears.
The SSLConfig.properties file is updated. Continue with the next step of restarting your CA SiteMinder® Agent for SharePoint.
Starting or stopping the CA SiteMinder® Agent for SharePoint involves the following separate procedures:
Change the value of the EnableWebAgent parameter to accomplish either of the following tasks:
Follow these steps:
Agent-for-SharePoint_home\proxy-engine\conf\defaultagent\WebAgent.conf
EnableWebAgent="NO"
You can change the states of the related services on your CA SiteMinder® Agent for SharePoint.
Note: To start or stop your CA SiteMinder® Agent for SharePoint, change the value of the EnableWebAgent parameter first.
Follow these steps:
The Services dialog appears.
The states of the services and CA SiteMinder® Agent for SharePoint are changed.
Agent-for-SharePoint_home/proxy-engine
./sps-ctl start
The service and the CA SiteMinder® Agent for SharePoint start. The CA SiteMinder® Agent for SharePoint stops or starts according to the value you set in the EnableWebAgent parameter.
Agent-for-SharePoint_home/proxy-engine
./sps-ctl stop
The service and the CA SiteMinder® Agent for SharePoint stop.
This section describes configuring secure communications between your CA SiteMinder® Agent for SharePoint reverse proxy and the Public URLs of your SharePoint web applications.
The first step in configuring the reverse proxy for secure communications is modifying the SSL configuration file.
The SSL configuration file requires the following modifications:
Follow these steps:
Agent-for-SharePoint_home\httpd\conf\extra\httpd-ssl.conf
Indicates the directory where the CA SiteMinder® Agent for SharePoint is installed.
Default: (Windows) [32-bit] C:\Program Files\CA\Agent-for-SharePoint
Default: (Windows) [64-bit] C:\CA\Agent-for-SharePoint
Default: (UNIX/Linux) /opt/CA/Agent-for-SharePoint
The previous example assumes that you already have three web applications listening for HTTP requests on ports 80, 81 and 82. The previous example shows how to add HTTPS ports 443, 481 and 482 respectively.
<VirtualHost _default_:443>
# General setup for the virtual host
DocumentRoot "C:/CA/Agent-for-SharePoint/httpd/htdocs"
ServerName SMSPA2010.smtest.ca.com:443
ServerAdmin Admin@smtest.ca.com
# ErrorLog logs/error_log.log
# TransferLog logs/access_log.log
SSLEngine on
SSLCertificateFile "C:/CA/Agent-for-SharePoint/SSL/certs/smspa2010.smtest.ca.com.cer"
SSLCertificateKeyFile "C:/CA/Agent-for-SharePoint/SSL/keys/smspa2010.smtest.ca.com.key"
</VirtualHost>
<VirtualHost *:481>
DocumentRoot "C:/CA/Agent-for-SharePoint/httpd/htdocs/481smspa2010"
ServerName smspa2010.smtest.ca.com
ServerAdmin Admin@smtest.ca.com
ErrorLog logs/481smspa2010_error_log.log
TransferLog logs/481smspa2010_access_log.log
SSLEngine on
SSLCertificateFile C:/CA/Agent-for-SharePoint/SSL/certs/smspa2010.smtest.ca.com.cer
SSLCertificateKeyFile C:/CA/Agent-for-SharePoint/SSL/keys/smspa2010.smtest.ca.com.key
CustomLog logs/cipher_log_481smspa2010 \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
<VirtualHost *:482>
DocumentRoot "C:/CA/Agent-for-SharePoint/httpd/htdocs/482smspa2010"
ServerName smspa2010.smtest.ca.com
ServerAdmin Admin@smtest.ca.com
ErrorLog logs/482smspa2010_error_log.log
TransferLog logs/482smspa2010_access_log.log
SSLEngine on
SSLCertificateFile C:/CA/Agent-for-SharePoint/SSL/certs/smspa2010.smtest.ca.com.cer
SSLCertificateKeyFile C:/CA/Agent-for-SharePoint/SSL/keys/smspa2010.smtest.ca.com.key
CustomLog logs/cipher_log_482smspa2010 \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
The previous example describes the virtual host entries that are created to match the port settings in Step 2.
The SSL Configuration file is modified. Continue with the next step of generating certificates and keys for each unique server (FQDN) in your environment.
The next step in configuring the reverse proxy for secure communications is to generate a private (Windows) RSA Key (server key) for each virtual site with a fully qualified domain name (FQDN). Do one of the following procedures:
Generate a private key for each virtual site with a fully qualified domain name (FQDN). This procedure describes how to generate an unencrypted private key.
Follow these steps:
Agent-for-Sharepoint_home\SSL\bin
Indicates the directory where the CA SiteMinder® Agent for SharePoint is installed.
Default: (Windows) [32-bit] C:\Program Files\CA\Agent-for-SharePoint
Default: (Windows) [64-bit] C:\CA\Agent-for-SharePoint
Default: (UNIX/Linux) /opt/CA/Agent-for-SharePoint
.\openssl genrsa -out ..\keys\server_FQDN.key [numbits]
Specifies the fully qualified domain name of the server.
(Optional) Specifies the size of the private key to generate in bits.
Default: 512
Range: 512 - 2048
The following example describes creating a 2048-bit key for a server named smspa2010:
.\openssl genrsa -out ..\keys\smspa2010.example.com.key 2048
The private unencrypted server keys are created. Continue with the next step of generating a certificate signing request.
Generate a private key for each virtual site with a fully qualified domain name (FQDN). This procedure describes how to generate an encrypted private key.
Follow these steps:
Agent-for-Sharepoint_home\SSL\bin
Indicates the directory where the CA SiteMinder® Agent for SharePoint is installed.
Default: (Windows) [32-bit] C:\Program Files\CA\Agent-for-SharePoint
Default: (Windows) [64-bit] C:\CA\Agent-for-SharePoint
Default: (UNIX/Linux) /opt/CA/Agent-for-SharePoint
.\openssl genrsa -des3 -out ..\keys\server_FQDN.key [numbits]
Specifies the fully qualified domain name of the server.
(Optional) Specifies the size of the private key to generate in bits.
Default: 512
Range: 512 - 2048
The following example describes creating a 1024-bit key for a server named smspa2010:
.\openssl genrsa-des3 -out ..\keys\smspa2010.example.com.key 1024
The private encrypted server keys are created and written to the specified key output file.
The key output file will be in encrypted ASCII PEM (from “Privacy Enhanced Mail") format.
Because the file is encrypted, you will be prompted for a pass-phrase to protect it and decrypt it later if you want. If you do not want your key to be protected, do not use the -des3 argument in the command line.
To view the details of this RSA key, enter the following command:
openssl rsa -noout -text -in server.key
The next step in configuring the reverse proxy for secure communications is generating the certificate signing requests for each of the virtual servers.
Follow these steps:
.\openssl req -config .\openssl.cnf -new -key ..\keys\server_FQDN .key -out ..\keys\server_FQDN.csr
The following example describes creating a certificate request for a server named smspa2010 on the support.example.com domain:
.\openssl req -config .\openssl.cnf -new -key ..\keys\smspa2010.support.example.com.key -out ..\keys\smspa2010.support.example.com.csr
Country: Your_Country State: Your_State Locality: Your_Town Organization: Example Org. Unit: support CN: smspa2010.support.example.com E-Mail: admin@support.ca.com Challenge Pwd: firewall Optional name: blank
Note: The value for the common name (CN) must match the fully qualified domain name (FQDN) of the web server.
The system generates a certificate request with the certificate file name and a request number, as shown in the following example:
smspa2010.support.example.com.csr 8
The certificate signing requests are generated and submitted. Continue with the next step of downloading your certificates from your certificate authority.
The next step in configuring the reverse proxy for secure communications is downloading the signed certificates from the certificate authority.
The virtual host sections in your SSL configuration file specify a certificate location for each virtual host. The SSLCertificateFile line in the following example specifies the location for the spa2010.support.example.com server:
SSLCertificateFile "Agent-for-SharePoint_home/SSL/certs/smspa2010.support.example.com.cer
Indicates the directory where the CA SiteMinder® Agent for SharePoint is installed.
Default: (Windows) [32-bit] C:\Program Files\CA\Agent-for-SharePoint
Default: (Windows) [64-bit] C:\CA\Agent-for-SharePoint
Default: (UNIX/Linux) /opt/CA/Agent-for-SharePoint
Follow these steps:
The certificates are downloaded. Continue with the next step of accommodating your SSL sites by modifying the proxy rules.
The next step in configuring the reverse proxy for secure communication is modifying the proxy rules for the server on which your CA SiteMinder® Agent for SharePoint runs.
Note: Even if you are using only SSL, the proxy rules files require rules for both HTTP and HTTPS protocols.
Follow these steps:
Agent-for-SharePoint_home\proxy-engine\conf\proxyrules.xml
Indicates the directory where the CA SiteMinder® Agent for SharePoint is installed.
Default: (Windows) [32-bit] C:\Program Files\CA\Agent-for-SharePoint
Default: (Windows) [64-bit] C:\CA\Agent-for-SharePoint
Default: (UNIX/Linux) /opt/CA/Agent-for-SharePoint
<nete:proxyrules xmlns:nete="http://smspa2010.smtest.ca.com/" debug="yes"> <nete:cond type="host" criteria="endswith"> <nete:case value="81"> <nete:forward>http://w2k8r2.smtest.ca.com:14056$0</nete:forward> </nete:case> <nete:case value="82"> <nete:forward>http://w2k8r2.smtest.ca.com:31415$0</nete:forward> </nete:case> <nete:case value="481"> <nete:forward>http://w2k8r2.smtest.ca.com:14056$0</nete:forward> </nete:case> <nete:case value="482"> <nete:forward>http://w2k8r2.smtest.ca.com:31415$0</nete:forward> </nete:case> <nete:default> <nete:forward>http://w2k8r2.smtest.ca.com:31567$0</nete:forward> </nete:default> </nete:cond> </nete:proxyrules>
The proxy rules are modified. Continue with the next step of enabling SSL on your CA SiteMinder® Agent for SharePoint.
The next step in configuring the reverse proxy for secure communication is enabling SSL on the server that runs your CA SiteMinder® Agent for SharePoint.
To enable SSL on your CA SiteMinder® Agent for SharePoint, do one of the following procedures, as appropriate.
To enable SSL for an unencrypted private key on Windows, generate an spsapachessl.properties file.
Follow these steps:
Agent-for-SharePoint_home\httpd\bin
configssl.bat -enable
Note: If an overwrite warning appears, confirm that you want to overwrite the existing spsapachessl.properties file.
To enable SSL for an unencrypted private key on UNIX, edit the spsapachessl.properties located in the following location:
Agent-for-Sharepoint_home/httpd/conf/spsapachessl.properties
Follow these steps:
apache.ssl.enabled=
apache.ssl.enabled=Y
To enable SSL for an encrypted private key, generate an spsapachessl.properties file.
Follow these steps:
Note: If an overwrite warning appears, confirm that you want to overwrite the existing spsapachessl.properties file.
The next steps in configuring the reverse proxy for secure communications involve the following tasks:
Follow these steps:
Agent-for-SharePoint_home/sharepoint_connection_wizard
The SharePoint Connection wizard starts.
The Login Details screen appears.
Specifies the Policy Server name or IP address.
Specifies the Policy Server administrator username.
Specifies the Policy Server administrator password.
Specifies the Agent-4x. The connection with the Policy Server is established using the details given in the Agent Name.
Specifies the shared secret key that is associated with the Agent.
The Select Action screen appears.
The SharePoint Connection Properties screen appears.
The Save Complete screen appears.
The partnership details are saved, the SharePoint Connection is modified, and the wizard closes.
Set-SPTrustedIdentityTokenIssuer "LDAP-Claims" -SignInUrl https://smspa2010.support.example.com/affwebservices/public/wsfeddispatcher
Note: For more information about the Set-SPTrustedIdentityTokenIssuer command, see http://technet.microsoft.com/en-us/library/ff607792.aspx
The protocol is changed. Continue with the next step of creating alternate access mappings for your port-based virtual sites.
The next step in configuring the reverse proxy for secure communication is creating alternate access mappings on your SharePoint server for the port-based virual hosts on your CA SiteMinder® Agent for SharePoint.
Port-based proxy rules require the following alternate access mappings on your SharePoint central administration server:
Follow these steps:
|
Public URL |
Internal URL |
|
https://support.example.com |
https://spa2010.support.example.com\443 |
The alternate access mappings are created. Continue with the next step of modifying the ConfigSLL.bat file.
The next step in configuring the reverse proxy for secure communication is modifying your CA SiteMinder® authentication scheme to use SSL.
Authentication schemes use HTTP unless you specify HTTPS when creating the authentication scheme.
Follow these steps:
A confirmation screen appears.
The authentication scheme is modified. Continue with the next step of restarting your CA SiteMinder® Agent for SharePoint.
Starting or stopping the CA SiteMinder® Agent for SharePoint involves the following separate procedures:
Change the value of the EnableWebAgent parameter to accomplish either of the following tasks:
Follow these steps:
Agent-for-SharePoint_home\proxy-engine\conf\defaultagent\WebAgent.conf
EnableWebAgent="NO"
You can change the states of the related services on your CA SiteMinder® Agent for SharePoint.
Note: To start or stop your CA SiteMinder® Agent for SharePoint, change the value of the EnableWebAgent parameter first.
Follow these steps:
The Services dialog appears.
The states of the services and CA SiteMinder® Agent for SharePoint are changed.
Agent-for-SharePoint_home/proxy-engine
./sps-ctl start
The service and the CA SiteMinder® Agent for SharePoint start. The CA SiteMinder® Agent for SharePoint stops or starts according to the value you set in the EnableWebAgent parameter.
Agent-for-SharePoint_home/proxy-engine
./sps-ctl stop
The service and the CA SiteMinder® Agent for SharePoint stop.
|
Copyright © 2014 CA.
All rights reserved.
|
|