

You can record information about the assertion attributes to the audit logs. Use these logs for a security audit, or during an investigation. The type of event determines the information that is recorded in the log. The following events are recorded when you enable assertion‑attribute logging:
The logging of assertion attributes is disabled by default. Enable assertion‑attribute logging on your Policy Server.
The following graphic describes how to enable assertion‑attribute logging:
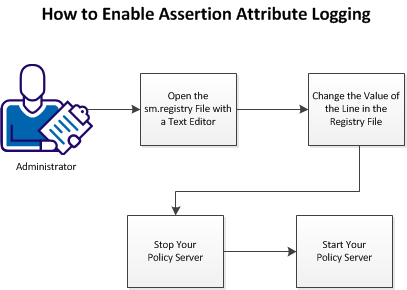
Follow these steps:
Change this setting on UNIX or Linux operating environments by opening the sm.registry file with a text editor. The sm.registry file is stored on your Policy Server.
Follow these steps:
Installation_Directory/registry
Specifies the location in the file system where the Policy Server is installed.
Default: /opt/CA/siteminder
sm.registry
You can now change the settings.
The following entry in the sm.registry file controls attribute assertion logging:
Indicates whether attribute assertions are recorded in the audit logs. A value of 2 enables logging. A value of 3 enables logging and records the authentication method of the user. A value of 4 enables logging for Enhanced Session Assurance with DeviceDNA™
Limits: 0, 2, 3, 4
Default: 0 (logging disabled)
Follow these steps:
HKEY_LOCAL_MACHINE\SOFTWARE\Netegrity\SiteMinder\CurrentVersion\Reports=
Enable Enhance Tracing= 0; REG_DWORD
Enable Enhance Tracing= 2; REG_DWORD
Enable Enhance Tracing= 3; REG_DWORD
Enable Enhance Tracing= 4; REG_DWORD
The value of the line in the registry file is changed.
Stopping a Policy Server has the following results:
Follow these steps:
installation_path/siteminder/stop-all
The Policy Server logs all UNIX executive activity in the installation_directory/log/smexec.log file. Log entries are always appended to the existing log file.
Starting Policy Server has the following results:
Start all Policy Server processes, with one of the following actions:
installation_path/siteminder/start-all
The Policy Server logs all UNIX executive activity in the installation_directory/log/smexec.log file. Log entries are always appended to the existing log file.
|
Copyright © 2013 CA.
All rights reserved.
|
|