

The following figure is a detailed process flow for how a privileged user initiates an impersonation session.
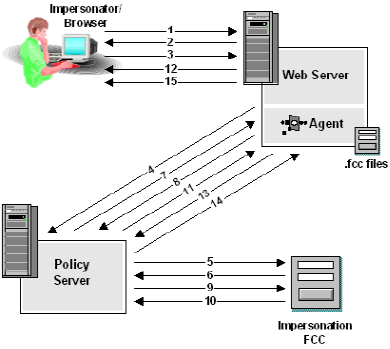
Note: Since the impersonator has not accessed any resources, no impersonation has taken place.
The session specification, is returned to the Web Agent. It contains the DN of the impersonatee and the DN of the impersonator, as well as the directories where both the impersonator and the impersonatee were located.
The Web Agent moves the existing SMSESSION to SMSAVEDSESSION and sets a new SMSESSION cookie equal to the new session spec due to a @pushsession directive in the FCC.
|
Copyright © 2013 CA.
All rights reserved.
|
|