

This section contains the following topics:
Security Considerations for Impersonation
Policy Server Objects for Impersonation
Sample Implementation of Impersonation
Impersonation provides a method for a privileged user to assume the role of another user without ending the privileged user’s session. This feature facilitates the following:
Impersonation provides a secure solution in the preceding situations. In all cases, passwords are not disclosed to allow one user to impersonate another user.
The following terms are used when describing impersonation:
A user session created for the purpose of assuming another user's identity.
The user whose identity is assumed by a privileged user.
The privileged user that is able to assume the identities of other users.
A method for authenticating a user that allows a privileged user to assume the identity of another user while preserving the identity of the impersonator.
Also known as user session. This term is the time between authenticating and logging out.
Also known as the Session Ticket or Session Spec, this term is the information held in a proprietary format on the Policy Server that describes a user and the characteristics of the current session.
The name of the Web Agent cookie that contains the Policy Server’s Session Specification.
Note: For information about sessions, see the Policy Server Administration Guide.
The process of impersonating another user consists of the following:
The Policy Server determines whether or not the impersonator may be impersonated using a series of policies.
To begin an impersonated session, an impersonator accesses an .fcc file directly that has a target that points to a resource in the realm protected by the impersonation authentication scheme.
The following diagram shows an example of impersonation where a customer service representative (CSR) accesses an .fcc file directly to begin an impersonation session.
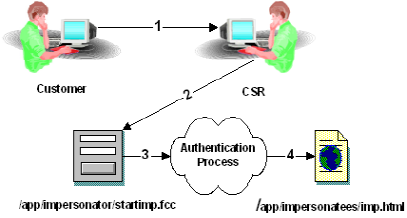
While impersonating a customer, an impersonator’s session specification will look to CA SiteMinder® much like the session specification of any customer. The major difference is that the impersonator’s distinguished name and the user directory in which the impersonator originally authenticated will be present as additional fields. This allows all impersonated access to resources to be passed through additional checks. It also allows the Policy Server to record impersonated activities for auditing.
The impersonated session specification is also used to prevent impersonation chaining. When the Policy Server determines that the fields for the impersonator DN and user directory are in use, it will not allow further impersonation and will reject the login attempt. This stops impersonators from stacking one impersonation on top of another to gain access to otherwise restricted resources.
While impersonating a user, the protection level at which an impersonator originally authenticated will not be checked. Normally, when accessing resources in a new realm protected by an authentication scheme at a higher level, the user would be challenged for new credentials. However, since an impersonator should be a privileged user, these types of challenges will not occur during an impersonation session. Protection levels are meant to indicate the strength of credentials used to access resources in a realm. In the case of impersonation, there are no credentials specific to the user being impersonated, therefore protection levels are not considered.
Note: Once the impersonated session ends, protection levels are once again enforced normally.
During an impersonated session, an impersonator’s original session can possibly idle out. This depends on the idle timeout value for the realm in which the impersonator originally authenticated. If the impersonator impersonates a user for a longer period than their original idle timeout, the impersonation session ends with the impersonator’s original session. To avoid this situation, increase the session idle timeout for realms in which impersonators commonly authenticate.
|
Copyright © 2013 CA.
All rights reserved.
|
|