

A consumer is a site that uses a SAML 1.x assertion to authenticate a user.
Note: A site can be a SAML producer and a SAML consumer.
Any CA SiteMinder® site with legacy federation functionality can consume SAML 1.x assertions and can use these assertions to authenticate users. When an assertion is consumed, the site has to be able to compare the information from the assertion against a user directory to complete the authentication process.
CA SiteMinder® provides the following SAML 1.x authentication methods:
The SAML-based authentication schemes let a consumer site authenticate a user. Consuming a SAML assertion and establishing a CA SiteMinder® session enables cross-domain single sign-on. After the user is identified, the consumer site can authorize the user for specific resources.
The following illustration shows the major components for authentication at the consumer site.
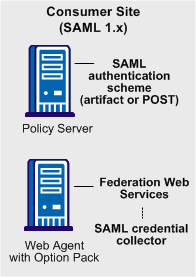
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The SAML 1.x authentication scheme is configured at the consumer-side Policy Server. The SAML credential collector is a component of the Federation Web Services application. The credential collector is installed on the consumer-side Web Agent, or on an SPS federation gateway. The credential collector obtains information from the SAML authentication scheme at the Policy Server, then uses that information to access a SAML assertion.
The SAML assertion becomes the credentials that grant access to the Policy Server at the consumer site. The user is authenticated and authorized, and if authorization is successful, the user is redirected to the target resource.
The following illustration shows how the SAML 1.x artifact authentication scheme processes requests.
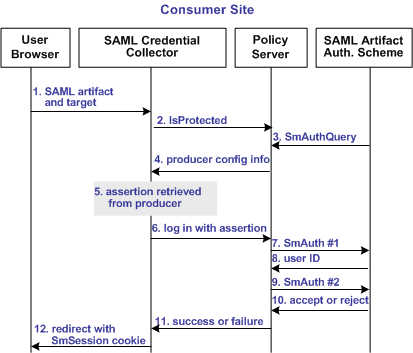
Note: An SPS federation gateway, or the Web Agent and Web Agent Option Pack, provide the Agent and SAML Credential Collector functionality.
Unless otherwise stated, all activity in this process occurs at the Consumer site:
The artifact and target URL are originally generated from the Web Agent at the producer site.
Note: The CA SiteMinder® Authentication AP dictate the two-step authentication process. For more information, see the CA SiteMinder® Programming Guide for C or the CA SiteMinder® Programming Guide for Java.
The following illustration shows how the SAML 1.x POST profile authentication scheme processes requests.
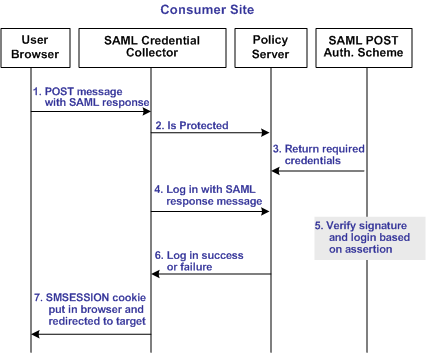
Note: The SPS federation gateway or the Web Agent Option Pack provide the SAML Credential Collector functionality.
Unless otherwise stated, the following process takes place at the consumer site:
The prerequisites for configuring a SAML authentication scheme are as follows:
The CA SiteMinder® Policy Server includes legacy federation functionality.
To install the Policy Server, refer to the Policy Server Installation Guide.
Federation Web Services (FWS) is a web application. FWS provides the SAML credential collector servlet, which consumes assertions and other services for federated network configurations.
To use the FWS application features, install the Web Agent and Web Agent Option Pack or the SPS federation gateway, which has FWS embedded at the producer and consumer sites.
For installation and configuration instructions, refer to the following guides:
Specify a Value for the DefaultAgentName Setting
When you install a Web Agent, define a value for the Web Agent parameter DefaultAgentName for all consumer Web Agents. This value specifies a Web Agent identity.
Include the specified Agent identifying the DefaultAgentName in the Resource Filter of the realm that protects the target resource. Configure the DefaultAgentName parameter in the Agent Configuration Object or the local Agent configuration file. Omitting the DefaultAgentName parameter or using the value specified in the AgentName parameter in the realm resource filter causes SAML 1.x authentication to fail, regardless of the single sign-on profile.
To use the SAML POST profile for passing assertions, the producer must sign the SAML response that contains the assertion. The assertion consumer at the consumer site must verify that signature.
To accomplish these tasks, add a private key/certificate pair to the certificate data store for signing, verification or both. The certificate data store lets you manage and retrieve keys and certificates, which are required to sign and validate SAML responses.
For more information about the certificate data store, see the Policy Server Configuration Guide.
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|