

Policy Server Guides › Policy Server Configuration Guide › Using the Policy Server as a RADIUS Server › Policies in RADIUS Environments
Policies in RADIUS Environments
A CA SiteMinder® RADIUS policy is enforced by a RADIUS Agent and is created by binding the following elements together:
- An authentication rule
- A response
- A user or user group, and
- Optionally, an IP address, Time, and an active policy.
The basic structure of a policy is shown in the following diagram.
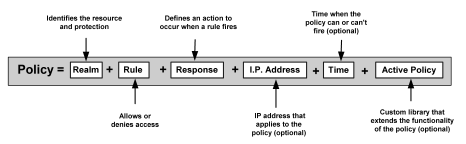
Although RADIUS policies are composed of the same elements that are contained in policies used by CA SiteMinder® Agents, RADIUS Agents interpret the components differently. Rules, realms, and responses perform different functions, as shown in the following table.
|
Policy Component
|
In a RADIUS Policy, this item:
|
In a CA SiteMinder® Agent Policy, this item:
|
|
Realm
|
- Identifies the Agent.
- Identifies the authentication scheme.
- Defines session timeouts.
|
- Defines the resource filter (directory within the domain that the CA SiteMinder® Agent will govern).
- Identifies the Agent.
- Identifies the authentication scheme.
- Defines the state (protected or unprotected) of the resource.
- Identifies which events (authentication or authorization) to process.
- Defines session timeouts.
|
|
Rule
|
- Authenticates only.
- Allows or denies access.
- Defines time or active rule restrictions.
|
- Defines the resource filter.
- Defines the action (Web Agent action, authorization event, or authentication event.
- Allows or denies access.
- Authorizes and authenticates.
- Defines time or active rule restrictions.
|
|
Response
|
- Defines the values to return for authentication events.
|
- Defines the value to return for an authorization event.
- Defines the values to return for authentication events.
- Defines the values to return for authorization reject events.
- Defines the values to return for authentication reject events.
|
RADIUS vs. Non-RADIUS Resources
The elements of a RADIUS policy are treated differently in part because of how resources are identified in a RADIUS environment. In a CA SiteMinder® Agent environment, specific resources are identified using a resource filter in the definition of the realm. The resource filter identifies the directory location of the resources. The realm definition also identifies the Web Agent and the authentication scheme, as shown in the following diagram:
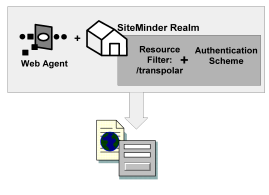
As shown in the following diagram, protected resources are located differently in a RADIUS environment. Instead of the realm identifying the resource using a filter, the RADIUS Agent identifies the resource using a realm hint. A realm hint is an attribute that enables the Policy Server to establish the domain in which to authenticate users. The realm hint either identifies a specific realm that the Agent protects or signifies that the Agent must protect the entire NAS device.
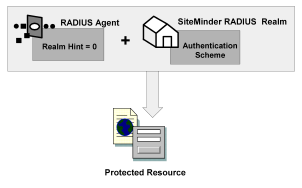
Use Realm Hints
How does a RADIUS Agent protect a NAS device that must authenticate users in different domains, such as domainA and domainB? A realm hint is a RADIUS attribute that enables CA SiteMinder® to determine the correct domain in which to authenticate a user. You must provide a RADIUS Agent with one of the following realm hint values:
- 0--(Default) Signifies that there is only one realm in the policy domain and therefore, a hint is not needed. The realm is bound to the NAS device directly.
- 1--(RADIUS User-Name attribute) CA SiteMinder® parses the realm name from the user name in this attribute, then finds the associated domain, as explained below.
- An attribute that contains the actual name of the domain. This attribute is not available for all NAS devices. see your NAS device product documentation for more information.
When the realm hint is set to 1, the realm name is parsed from the user name attribute. The user_name-realm separator must be “@” or “/”.
- If the separator is “@” then the element following the “@” is the realm name. For example, in jack@realmA.com, the realm is realmA.com.
- If the separator is “/” then the element preceding the “/” is the realm name. For example, in x5/jack, the realm is x5.
The following diagram and explanation shows how a proxy server determines the correct CA SiteMinder® domain in which to authenticate a user.
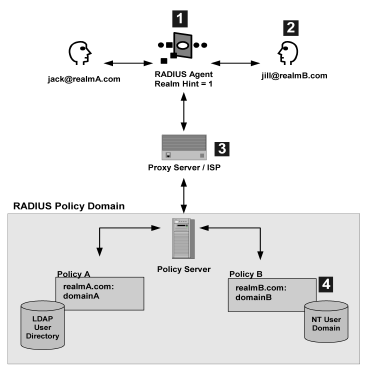
- One RADIUS agent protects both CA SiteMinder® domains. The RADIUS Agent is configured with the realm hint value of 1.
- When Jill tries to access the ISP’s proxy server, the RADIUS agent intercepts the request and forwards Jill’s user name attribute jill@realmB.com to the Policy Server.
- The Policy Server parses the user_name and realm_name from the user name attribute.
Example: jill@realmB.com, where jill is the user_name and realmB.com is the realm_name.
The Policy Server identifies the domain associated with the realm_name. The domain associated with realmB.com is domainB.
- The Policy Server authenticates the user_name in the appropriate directory. The user_name jill is authenticated in the NT user domain defined for Policy B: realmB.com:domainB.
Copyright © 2015 CA Technologies.
All rights reserved.
 
|
|





