

CA SiteMinder® responses can be used to return RADIUS attributes to the NAS device if the user is authenticated. Attributes configure the characteristics of the session once the user is authenticated and define the user profile of the authenticated user. The user profile can be used by the NAS device. For example, using attributes in a response, you can define time limits for the RADIUS user session.
Using responses, you can provide the NAS device with user profile information that assigns privileges to the user. For example, you could allow one user unlimited access to a resource, yet limit another user’s access to the same resource. Used in this way, responses give you the ability to authorize users even though RADIUS is primarily only a mechanism for authentication.
Note: If the NAS specifies authentication only, by default, CA SiteMinder® does not return RADIUS attributes. To return RADIUS attributes when the NAS specifies authentication only, follow the instructions in Configure SiteMinder to Always Return RADIUS Attributes.
RADIUS responses are paired with rules that authenticate. If a rule authenticates a user successfully, the RADIUS response is triggered. If the rule does not authenticate the user, the response is not triggered.
If a response is triggered, the Policy Server sends the attributes contained in the response to the NAS device. This information is used to customize the user’s session, as shown in the following diagram:
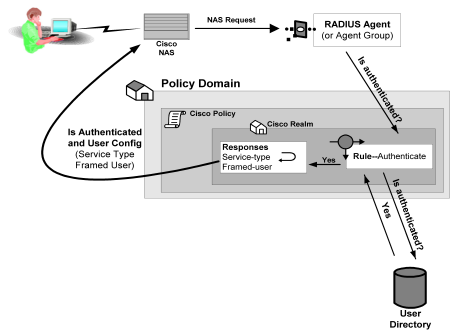
You can use the following attributes in responses:
These attributes return information associated with a user in an LDAP, WinNT, or ODBC user directory. User attributes are retrieved from the user directory and can used to modify the behavior of the RADIUS device.
These attributes return profile information associated with an LDAP directory object related to the user. For example, the DN attribute could return information about LDAP objects such as the user’s group or organizational unit (OU).
These attributes return values from a custom library that was developed using the CA SiteMinder® Authorization API. An active response is generated when CA SiteMinder® invokes a function in the custom library.
These attributes return values defined by the following Agent type attributes:
Generic RADIUS attributes, as defined by the RADIUS Protocol specification, Request for Comment (RFC) 2138. The identifiers for these attributes include 1-25 and 27-63. Some of these attributes may be used multiple times in the same response.
Any RADIUS Agent type can return a response that includes generic RADIUS attributes.
Attributes defined in the Dictionary file of the NAS device. These attributes define values that are not defined by generic RADIUS attributes and are specific to the type of NAS device in use. The unique identifiers for these attributes extend beyond the range reserved for generic RADIUS attributes, starting with 64. For example, Lucent provides an extended RADIUS attribute called Ascend-Disconnect-Cause, which uses the identifier 195.
Only Agent types that match the vendor type of the extended RADIUS attribute can use the attribute. For example, a Shiva Agent type can use the extended RADIUS attributes defined for Shiva, but a Cisco Agent type cannot use Shiva extended attributes in a response. The extended attributes that are used in a response must match the attributes defined in the Dictionary file of the RADIUS client.
By default, CA SiteMinder® provides pre-defined RADIUS extended attributes for some Agent Types that use these attributes, such as Ascend (Lucent). You can also define additional RADIUS extended attributes for any of the RADIUS Agent types, if necessary.
Attributes defined in the Dictionary file of the NAS device, which use 26 as an identifier. Vendor-specific attributes enable you to define attributes for values that are not provided by the generic RADIUS attributes. Some vendors use vendor-specific attributes in place of or in addition to RADIUS extended attributes. For example, Cisco does not use RADIUS Extended attributes; however, this NAS device supports several vendor-specific attributes, such as Cisco AV–pair and Account-Info.
You can use vendor-specific attributes to pass information to other protocols. For example, you can define a vendor specific attribute for the Cisco AV–pair attribute to pass TACACS+ information to a TACACS+ server.
Vendor-specific attributes can only be defined in responses that match the vendor type of the RADIUS client.
By default, CA SiteMinder® provides pre-defined vendor-specific attributes for some Agent Types that use these attributes, such as the Network Associates' Sniffer Agent type. You can also define additional RADIUS extended attributes to any of the RADIUS Agent types, if necessary.
Note: For more information about RADIUS attributes, see Request for Comment (RFC) RADIUS Protocol 2138.
Some NAS devices always expect RADIUS responses in the Access-Accept, even if the NAS specifies authentication only. If the NAS specifies authentication only, by default, CA SiteMinder® does not return RADIUS attributes.
To always return RADIUS attributes to a NAS device, create a new registry value with the following parameters:
Note: The install program does not create a registry entry for AlwaysReturnRadiusAttrs. Until you create and set the entry, CA SiteMinder® uses the default value of 0.
After you set AlwaysReturnRadiusAttrs to a value greater than zero, the following message will appear in the Authentication Server’s debug log:
Radius Attributes will be returned regardless of RA_SERVICE_TYPE_AUTHENTICATE_ONLY
Before you can use an attribute in a response, the attribute must be made available to the Agent type returning the response. Attributes are made available to Agent types by defining the attributes in Agent types. Although many Agent types are pre-configured with vendor-specific and RADIUS extended attributes, you can add additional extended RADIUS, generic RADIUS, and vendor-specific attributes to Agent types, as needed.
You can define multiple instances of a vendor-specific attribute for the same Agent type. When you define multiple instances of a vendor-specific attribute, you can send a different value to the NAS device for each instance of the attribute. For example, for a Cisco Agent, you can define the following vendor-specific attributes, all using the same identifier (26):
The settings that define the number of times an attribute can be used within a response are located on the Modify Agent Type Attribute page of the Administrative UI.
To configure the attribute to be used multiple times, the Access Accept value must be set to Zero or Many.
The type of attribute that you define must match the vendor type of the Agent returning the response. For example, a vendor-specific Cisco attribute can only be returned by a Cisco Agent.
When the response is returned by the Agent, the packet structure of the response reflects the type of RADIUS Agent that sent the response. For example, the packet structure of a response returned by a Cisco Agent would include the vendor ID and the length of the string.
To define an attribute for an Agent type
The Agent Types page appears.
A list of Agent types that match the search criteria appears.
The View Agent Type page appears.
The settings and controls become active.
Verify that Create a new object of type Agent Type Attribute option is selected.
The Create Agent Type Attribute page appears.
The attribute identifier is defined in the RADIUS protocol specification. Although it is possible to overwrite the identifier of a Generic RADIUS attribute, you should generally retain the pre-defined Generic RADIUS attribute definitions, which match the RADIUS specification (RFC 2138).
Example: To create an attribute for the Callback-Id variable, type 20 in the Identifier field.
The attribute identifier is defined in the vendor documentation.
Example: To create an attribute for the Ascend-Callback attribute, type 246 in the Identifier field.
The attribute identifier is 26.
Example: To create an attribute for a Cisco Agent that enables the Agent to use TACACS+, type 26 in the Identifier field.
Note: For more information about attribute identifiers, see your RADIUS vendor documentation.
Attribute cannot be used in a response.
One instance or no instances of the attribute can be returned in the same response. If this value is selected, and you use the attribute in a response, the attribute will be removed from the Attribute list after you have used the attribute in a response.
Multiple instances or no instances of the attribute can be returned in the same response.
One instance of the attribute must be returned in a response. If this value is selected, and you use the attribute in a response, the attribute will be removed from the Attribute list after you have used the attribute in a response.
The RADIUS-specific fields are as follows
Provides information used to determine whether or not a user is allowed access to a specific NAS. The Access Request packets also provide information for any special services requested for that user.
Provides specific configuration information necessary to begin delivery of service to the user.
Note: You must set the Access Accept value to Zero or One, Zero or Many, or One and Only One in order to use the attribute in a response.
Sends information if any value of the received Attributes is not acceptable. This code is often used for reply messages.
Sends information if the NAS device has been configured for challenge/response.
Describes the type of service being delivered and the user to whom it is being delivered.
Sends information if the Accounting Request was recorded successfully. A RADIUS Accounting-Response is not required to have any attributes in it.
The Modify Agent Type Attribute page reappears, and the attribute name-value pair is added.
Note: To create multiple attribute name-value pairs, repeat steps 11 and 12. By mapping symbolic names to values, you only need to remember names.
The Modify Agent Type page reappears, and the Agent type attribute is added.
The attribute is defined for the selected Agent Type.
Note: When the task is complete and you create a response for this Agent type, you can select the Agent type attribute that you just added to the Agent type from an attribute list.
You can modify attributes that you created and attributes that have been pre-defined for a RADIUS Agent. For example, you can modify the pre-defined Ascend-PPP-Address attribute for the Ascend Agent type.
Note: When you modify an existing attribute, the attribute is not updated dynamically in responses that already use the attribute. If an attribute is used in a response, you must recreate the response using the updated attribute.
All RADIUS Agent types have been pre-configured to use the generic RADIUS attributes, as defined in RFC 2138. These attributes are available to be used by each RADIUS Agent type.
Important! If you overwrite a generic attribute or define a new attribute in the Generic RADIUS Agent, the change is applied to all RADIUS Agents. For example, if you modify the Filter ID attribute in the Generic RADIUS Agent, the modification is also made to all of the other RADIUS Agent types, such as Cisco, Shiva, Livingston, Ascend, and Checkpoint.
To modify agent type attributes
The Modify Agent Type pane opens.
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|