

Administer Advanced CA EEM Security › Touchpoint Security with CA EEM › Limit Access to Hosts with Sensitive Information
Limit Access to Hosts with Sensitive Information
Touchpoint Security answers the need to limit access to business-critical hosts and hosts on which you store sensitive information. The following illustration suggests an approach to accomplish this security goal.
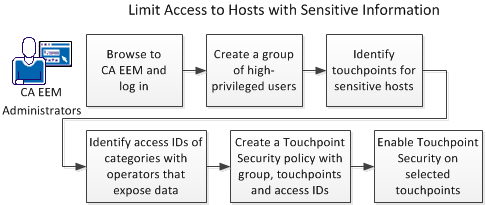
Follow these steps:
- Browse to CA EEM and log in.
- Create a group of high-privileged users.
See Create the Custom ContentAdmin Group.
- Identify the touchpoints that are associated with sensitive hosts.
See View the Touchpoints and Host Groups for a Selected Agent.
- Identify the categories with operators that expose data.
- Identify the Access Control IDs associated with the categories.
- Create a Touchpoint Security policy with this group, operator categories, and touchpoints.
See Create a Touchpoint Security Policy.
- Enable Touchpoint Security on selected touchpoints.
More information:
Approach to Configuring Touchpoint Security
Copyright © 2014 CA.
All rights reserved.
 
|
|


