

Touchpoint security ensures that the ability to run operators on business-critical hosts is limited to a small group of high-privileged users. The easiest way to protect sensitive hosts is to create one Touchpoint Security policy and list each of the associated touchpoints in a filter. Then enable Touchpoint Security on the properties setting for each of these touchpoints.
Example: Touchpoint Security Configuration for a Critical Touchpoint
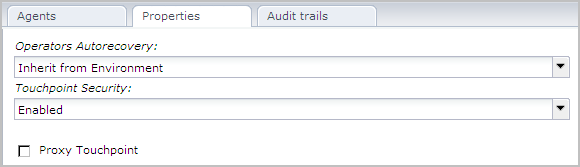
The following example shows the properties of a selected touchpoint. When Touchpoint Security is set to Enabled, the process evaluates each attempt to run an operator on this touchpoint against the Touchpoint Security policies.
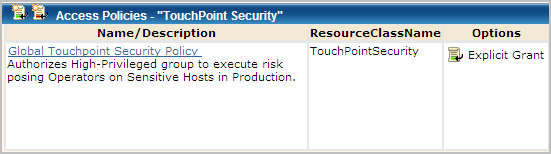
Example: Touchpoint Security Policy for Critical Touchpoints
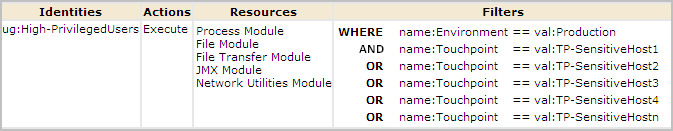
To ensure that only high-privileged users run operators on sensitive hosts in your production environment, create one Touchpoint Security policy. In the Touchpoint Security policy, add the Access Control ID associated with each category containing operators that could pose a risk. Add a filter for your environment. Add a filter for each touchpoint that references sensitive hosts.
Consider the following example Global Touchpoint Security Policy. The example policy grants the High-Privileged Users group authorization to run scripts or programs using operators in five categories on high-risk touchpoints. Access Control IDs represent the five categories. This policy applies to the specified touchpoints only in the Production environment.
|
Copyright © 2014 CA.
All rights reserved.
|
|