

Suppose you install an agent on your host and do not want anyone but you to execute operators on your host. To use Touchpoint Security to protect a host that is critical to you, consider performing the needed tasks in the following sequence.
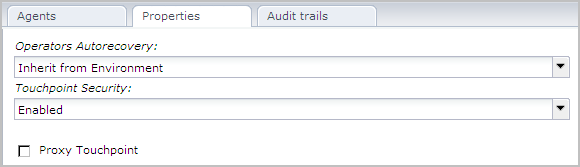
Example: Set Touchpoint Security to Enabled on My PC Touchpoint
The Touchpoint Security parameter for the selected Touchpoint, MyPC-TP, is set to Enabled.
Example: Create a Touchpoint Security Policy that Allows only Me to Execute Operators on My PC Touchpoint
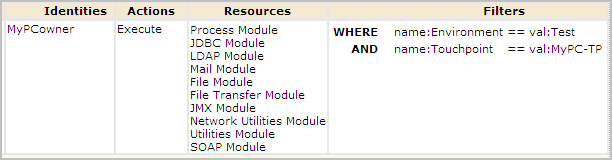
In the following example, assume that the protected host belongs to a user named MyPCowner. Notice that MyPCowner is the only Identity authorized to execute operators on the touchpoint, MyPC-TP. Here, the Access Control IDs are associated with all categories with operators that can execute on an agent host. In this case, the references include categories of operators that do not make changes to the host. The idea in this example is that the user wants no access to the host associated with the MyPC-TP touchpoint by any outside user. Only MyPCowner can run processes on MyPC-TP when Touchpoint Security is enabled.
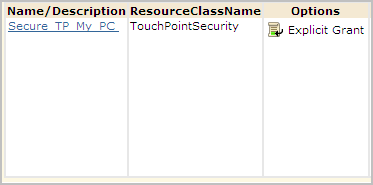
The touchpoint name is specified as the value in the filter.
|
Copyright © 2014 CA.
All rights reserved.
|
|