Use this procedure to enable a CA Audit client to send events to both CA Enterprise Log Manager and the CA Audit collector database. By adding a new target to the Route or Collector actions on an existing rule, you can send collected events to both systems. As an alternative, you can also modify specific policies or rules to send events only to the CA Enterprise Log Manager server.
CA Enterprise Log Manager collects events from CA Audit clients using the CA Audit SAPI Router and CA Audit SAPI Collector listeners. (CA Enterprise Log Manager can also collect events using the iTech plugin directly, if you configured any iRecorders to send directly to the CA Enterprise Log Manager server.) Collected events are stored in the CA Enterprise Log Manager event log store only after you push the policy to the clients and it becomes active.
Important: Configure the CA Enterprise Log Manager listeners to receive events before you modify and activate the policy. If you do not do this configuration first, you can incorrectly map events between the time that the policy becomes active and the listeners can correctly map the events.
To modify an existing policy rule action to send events to CA Enterprise Log Manager
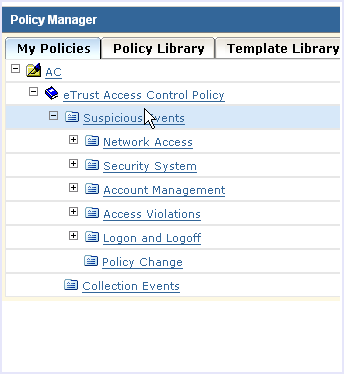
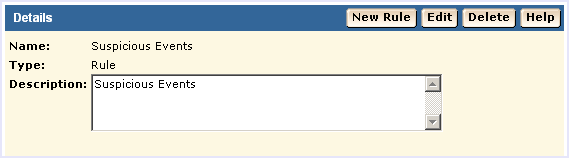
The rule wizard starts:
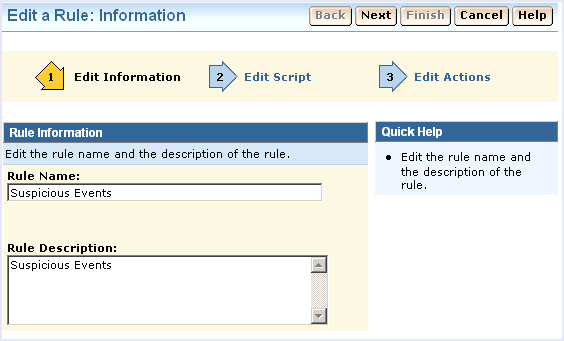
The rule actions page displays:
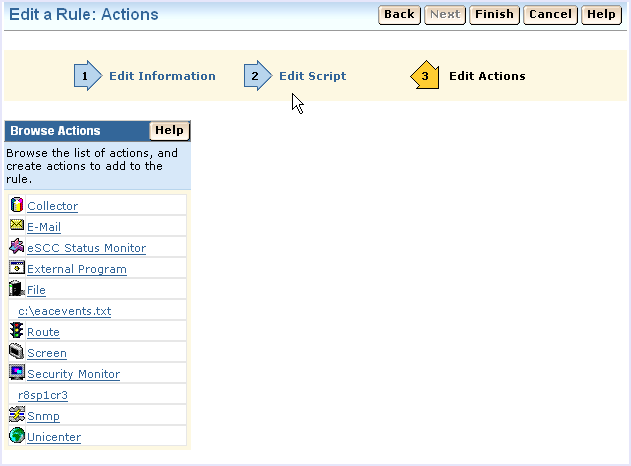
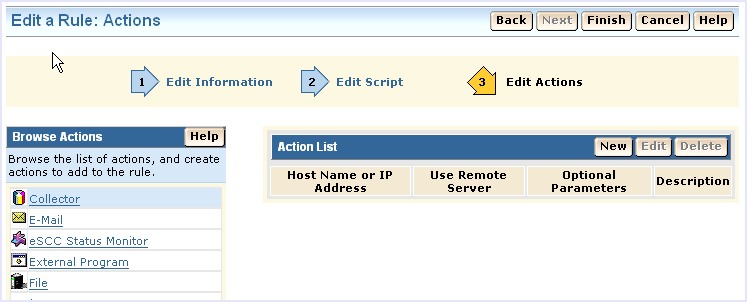
You could also use the Route action, but the collector action offers the additional benefit of an alternate host name for basic failover processing.
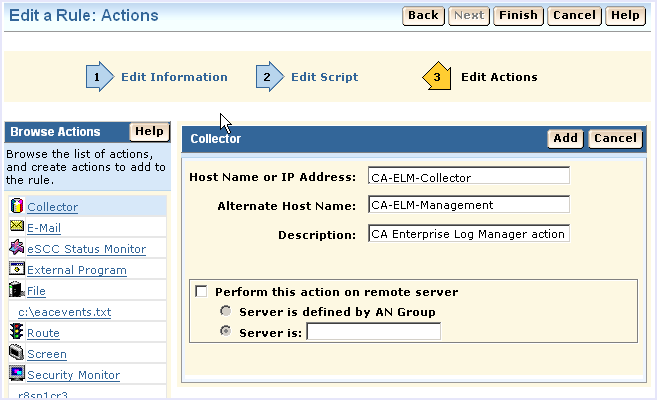
For a CA Enterprise Log Manager implementation with two or more servers, you can enter a different CA Enterprise Log Manager host name or IP address in the Alternate Host Name field. This takes advantage of CA Audit's automatic failover feature. If the first CA Enterprise Log Manager server is not available, CA Audit automatically sends events to the server named in the Alternate Host Name field.
Note: Next you check and activate the policy, so do not log out of the CA Audit Policy Manager.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |