Implementation Guide › Considerations for CA Access Control Users › How to Modify CA Audit Policies to Send Events to CA Enterprise Log Manager › Check and Activate the Changed Policy
Check and Activate the Changed Policy
After you change an existing policy to add a rule action, check (compile) it and then activate it.
To check and activate a CA Access Control policy
- Select the Rules tab in the lower right pane, and then select a rule to check.
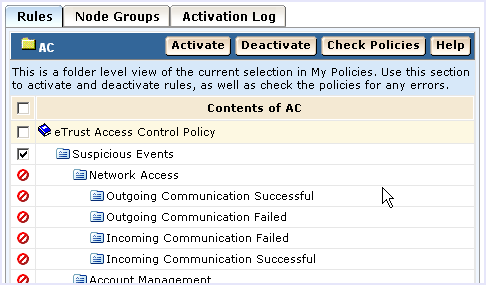
- Click Check Policies to check the changed rule with the new actions to ensure that it compiles properly.
Make any needed modifications to the rule and ensure that it compiles correctly before you activate it.
- Click Activate to distribute the checked policy that contains the new rule actions you added.
- Repeat this procedure for each rule and policy with collected events you want to send to CA Enterprise Log Manager.
