

If your organization uses RSA SecurID to authenticate users, you can use the capabilities of RSA SecurID to authenticate users login to CA ControlMinder Enterprise Management. When you integrate the Enterprise Management Server with RSA SecurID, CA ControlMinder Enterprise Management does not authenticate users on login. CA ControlMinder Enterprise Management detects that users authentication is done by a third-party program.
The following process explains how to integrate CA ControlMinder Enterprise Management with RSA SecurID:
The web server acts as a reverse proxy server for all login authentication requests.
RSA SecurID prevents users from accessing CA ControlMinder Enterprise Management directly.
Define only those users that you want to grant access to CA ControlMinder Enterprise Management.
Important! If you are using Active Directory you do not need to complete this step.
RSA Authentication Agent intercepts user access requests and forwards the requests to RSA Authentication Manager.
RSA Authentication Manager authenticates users access requests.
Each time a user tries to log in to CA ControlMinder Enterprise Management, RSA SecurID prompts the user for a valid RSA SecurID credentials instead of CA ControlMinder Enterprise Management user account details. If authenticated, RSA SecurID logs the user in to CA ControlMinder Enterprise Management.
Note: For more information about the RSA SecurID web Agent and Authentication Manager, refer to the RSA SecurID website.
When you integrate the Enterprise Management Server with RSA SecurID, each time a user logs into CA ControlMinder Enterprise Management,RSA SecurID authenticates the login request.If RSA SecurID validates the user login, the user automatically gains access to CA ControlMinder Enterprise Management.
The following diagram illustrates how RSA SecurID authenticates user logins to CA ControlMinder Enterprise Management:
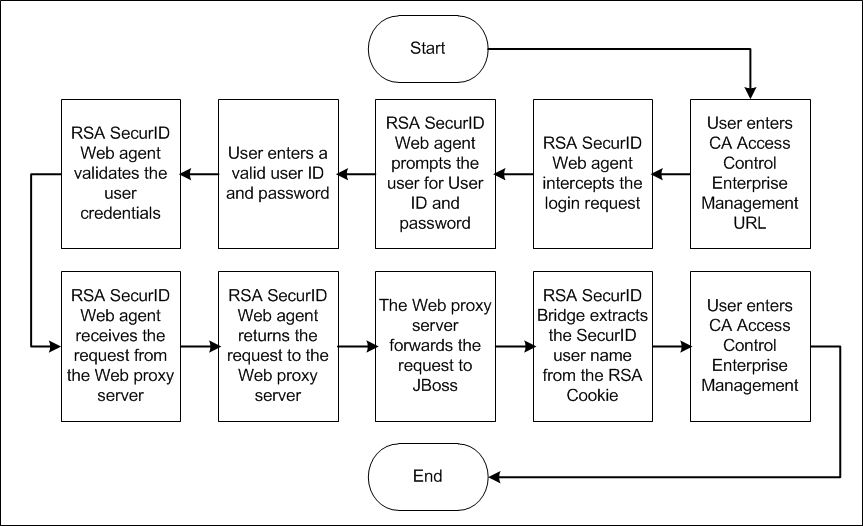
When a user attempts to login to CA ControlMinder Enterprise Management, RSA SecurID intercepts the request and prompts the user for a valid SecurID user name and password. The Web server you installed acts as a reverse proxy server that receives login requests from the RSA Authentication Web agent on the Enterprise Management Server and forwards the requests to the RSA Authentication Manager.
A reverse proxy is a gateway for other servers that enables one web server to provide content from another.
In this example, Steve the system administrator installed the Enterprise Management Server and Internet Information Services (IIS) 7.0 on a Windows Server 2008 with the Application Request Routing (ARR) module installed. The ARR module enables the IIS to act as a proxy server.
The internet Information Services (IIS) Manager console opens.
The Application Request Routing Cache management console opens.
Steve has enabled the IIS proxy settings.
The URL Rewrite configuration console opens.
The Add Rules window opens.
The Edit Inbound Rule configuration window opens.
http://enterprise_host:8080/{R:0}
The new inbound rule is created.
Steve has configured the IIS to forward requests to the Enterprise Management Server.
The RSA SecurID settings window opens.
HKEY_LOCAL_MACHINE\SOFTWARE\SDTI\RSAWebAgent
Steve has configured Internet Information Services as a reverse proxy server.
In this example, Steve the system administrator installed the Enterprise Management Server on a Red Hat Enterprise Linux 5.0. Steve now needs to install and configure the Apache Web Server 2.2.6 as a reverse proxy server.
tar -zxvf httpd_2.2.6.tar.gz ./configure --prefix=/usr/local/apache --enable-proxy --enable-proxy-http make make install
The Apache Web Server 2.2.6 is installed with the proxy module.
# Used for proxy to the Enterprise Management Server ProxyPass /iam http://196.168.1.1:8080/iam ProxyPass /castylesr5.1.1 http://192.168.1.1:8080/castylesr5.1.1 ProxyPassReverse /iam http://192.168.1.1:8080/iam
Steve configured the Apache Web Server 2.2.6 to act as a reverse proxy server.
/usr/local/apache/rsawebagent/
Steve has configured the RSA web agent to ignore the web browser IP address for cookie validation.
rsacookieapi.tar
JBOSS_HOME/server/default/deploy/IderntityMinder.ear/library
JBOSS_HOME/server/default/deploy/IderntityMinder.ear/user_console.war/WEB-INF/lib/
Steve configured the RSA web agent to enable SSO for CA ControlMinder Enterprise Management.
|
Copyright © 2013 CA Technologies.
All rights reserved.
|
|