

This section provides a sample scenario of how you can create scope records to decentralize security administration. Assume that your site has six security administrators. You want to limit the control of five of these administrators to certain resources. To do this, create INF entries for each CA ACF2 Option for DB2 rule set that you want to limit them to. By scoping administrators to certain rule sets, you control the resources that they can access. By masking the INF entries, you create scope records that apply to multiple resources. For simplicity’s sake, scope the security administrators to database resources only. (If you want to include more resources in their scopes, you must add INF entries that include other types of rule sets.) Using a naming convention for your resources makes scoping at a lower level easier.
The following chart shows how you might want to decentralize security administration by scoping security administrators to certain areas of responsibility.
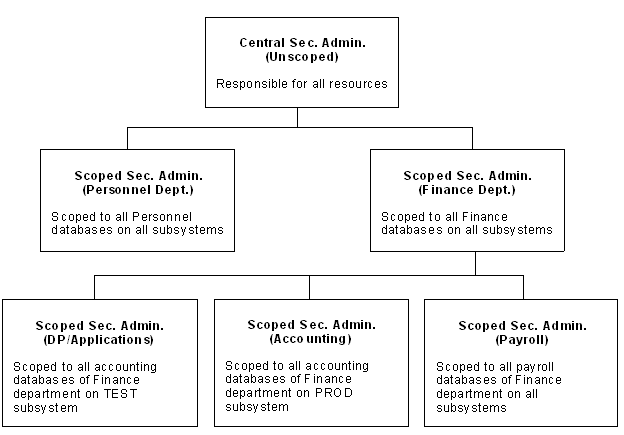
The scope records that are assigned to each scoped security administrator might look like the following. Each box shows the scope record name that each administrator would have in the SCPLIST field of his logonid record. Each box also shows the INF entry that you must add to each scope record.
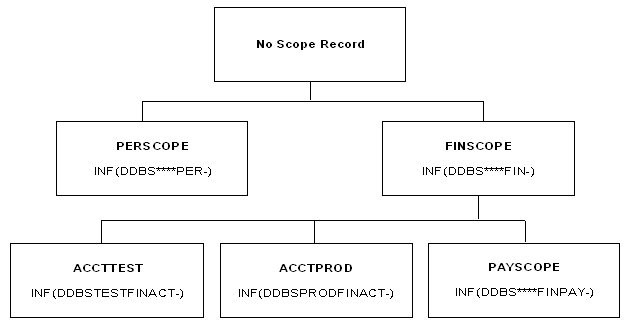
These scope records rely on a naming convention for database resources. For example, all Personnel databases begin with PER and all Finance databases begin with FIN. Therefore, the PERSCOPE scope record includes all database resources that begin with PER. The FINSCOPE record gives the finance security administrator control over all database resources that begin with FIN (including the resources covered by the ACCTTEST, ACCTPROD, and PAYSCOPE scope records). The ACCTTEST scope record is more specific and covers only database resources that begin with FINACT on the DB2 subsystem TEST. ACCTPROD enables the security administrator in the accounting area to control only databases that begin with FINACT on the PROD DB2 subsystem. The payroll security administrator can control access to any database that begins with FINPAY.
|
Copyright © 2011 CA Technologies.
All rights reserved.
|
|