

The Remote Monitoring AIM accesses an RM system through a WMI connection to the root\CIMV2 namespace utilizing DCOM. DCOM requires local system administrator user and password credentials. If you want to monitor a Windows computer, you must provide these credentials which the RM AIM stores in a file. The password is encrypted.
Remote Monitoring collects and provides Windows system information performing WMI queries (port 135) on the monitored RM systems. WMI uses port 135 (default).
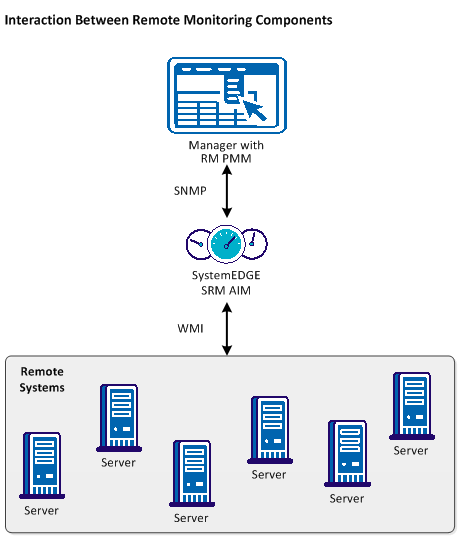
The following diagram illustrates these relationships.
|
Copyright © 2013 CA.
All rights reserved.
|
|