

The policies and access filter defined in steps 2, 3, and 4 of this example enable the Win-Admin user to view System Access reports, with limits on the data. With this access alone, the Win-Admin user cannot schedule a report, schedule an alert, or annotate a report. To do these things, add Win-Admin to the Analyst Auditor Report Server Access Policy and the Analyst Create-Schedule-Annotate policy. Example of these policies with Win-Admin added follow:
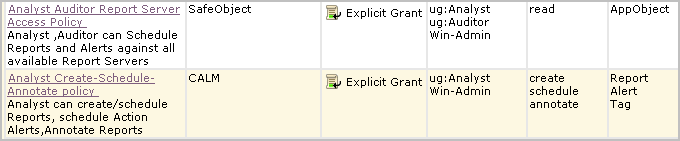
For Win-Admin to be able to create a report, this user needs write access added to the Win-Admin System Access policy. This requires opening the Win-Admin System Access policy for editing and adding write to the permitted actions.
![]()
For Win-Admin to be able to use prompts, the filter for Win-Admin System Access can be modified such that the attribute calmTag equals either System Access or Event Viewer.
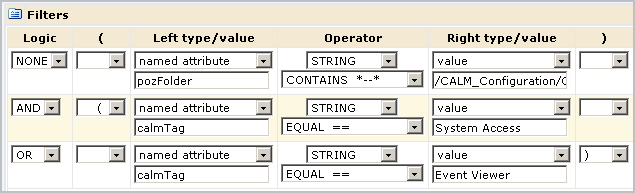
|
Copyright © 2013 CA.
All rights reserved.
|
|