

In addition to scope of authority, the security administrator must also be assigned particular types of administrative authorities. These authorities define the security functions the control ACIDs can perform for ACIDs within their scope.
Upper level security administrators can grant administrative authorities to lower level administrators within their scope, provided the higher level administrators already possess the appropriate authorities.
This corporate structure illustrates the ACIDs related to each structural element:
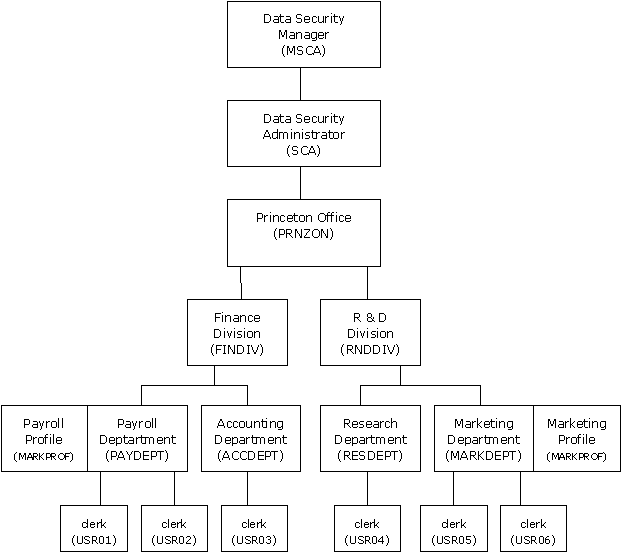
The following table describes how CA Top Secret ACIDs correspond to elements within the corporate structure shown in the corporate structure.
|
Corporate Element |
Corresponding ACID |
|
Data Security Manager/Chief |
MSCA is a control ACID |
|
Data security administrator |
SCA is a control ACID |
|
Princeton Office |
PRNZON is a zone ACID |
|
Finance Division R & D Division |
xxxDIV are division ACIDs |
|
Payroll Department Accounting Department Research Department Marketing Department |
xxxDEPT are department ACIDs |
|
Payroll functions Accounts Receivable functions Accounts Payable functions |
xxxPROF are profile ACIDs |
|
Clerks |
USRxx are user ACIDs |
An ACID's authority determines what can be done with the administration of ACIDs, resources, facilities, and the display of security database information. The administrative authorities are:
Each type of authority approximately corresponds to a different set of security environment control and maintenance functions (for example, ACID maintenance or resource maintenance).
A group of operands is associated with each type of authority. Each operand designates a specific functional authority. For example, ACID(CREATE) authority lets the control ACID create and delete ACIDs within their scope, while RESOURCE(INFO) lets the control ACID perform certain inquiries for any resource within their scope.
You cannot assign administrative authorities to a division, department, or profile ACID.
To give every ACID the ability to perform specified administrative functions, the administrator can assign the administrative authority to the ALL record. For example, assigning MISC1(LTIME) to the ALL record gives all ACIDs the authority to set their own terminal lock time interval. The ALL record can also contain resources access levels.
Only administrators with MISC9(GLOBAL) authority can assign administrative authorities to the ALL Record.
|
Copyright © 2014 CA Technologies.
All rights reserved.
|
|