You can configure the Adapter for risk evaluation only by integrating a SiteMinder authentication scheme. A SiteMinder authentication scheme that is part of the integration is known as backing authentication.
If you use a SiteMinder authentication scheme as backing authentication, the Shim acts as an interface between SiteMinder and the SiteMinder authentication scheme.
Note: For more information about backing authentication, see the CA Arcot Adapter for CA SiteMinder Installation and Configuration Guide. Not all SiteMinder authentication schemes are supported for backing authentication. For more information, see the r6.0 SP6 SiteMinder Platform Support Matrix.
To deploy SiteMinder authentication and Arcot risk analysis
Important! The integration requires that a SiteMinder Custom authentication scheme is configured. The SiteMinder Custom authentication scheme calls the required Adapter library. This library is required even if you are deploying backing authentication.
Note: For more information about user flows and the corresponding parameter values, see the CA Arcot Adapter for CA SiteMinder Installation and Configuration Guide.
Note: For more information about configuring a backing authentication scheme, see the CA Arcot Adapter for CA SiteMinder Installation and Configuration Guide.
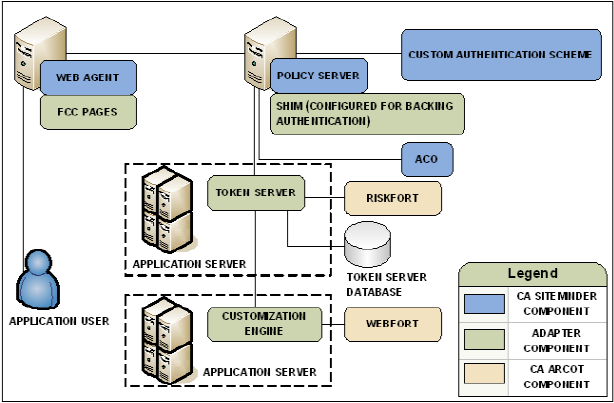
The following diagram illustrates this deployment scenario:
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |