

This section contains the following topics:
CA LDAP Server for z/OS Overview
CA Top Secret r12 (TSS) Backend Security Option
CA LDAP Server r15 for z/OS (RACF) Backend Security Option
CA LDAP Server r15 for z/OS (ACF2) Backend Security Option
You can configure a CA LDAP Server for z/OS as a user store by configuring a connection from the Policy Server to the LDAP Server. How you configure the connection from the Policy Server to the LDAP Server depends on the backend option that you are using to secure the LDAP Server:
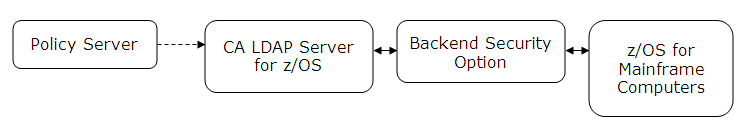
CA supports the following backend security options for CA LDAP Server:
Become familiar with the objectclass hierarchy for these backend security options before configuring the connection from the Policy Server to the LDAP Server. Also, add the backend-related objectclasses to the Policy Server registries in the LDAP namespace.
Note: z/OS is an IBM operating system for mainframe computers.
When you are using TSS to secure the CA LDAP Server for z/OS, complete the following steps before configuring the connection from the Policy Server to the CA LDAP Server:
The following diagram shows the hierarchy of objectclass entries in the CA Top Secret Directory Information Tree (DIT). Below the diagram is a description of each objectclass.
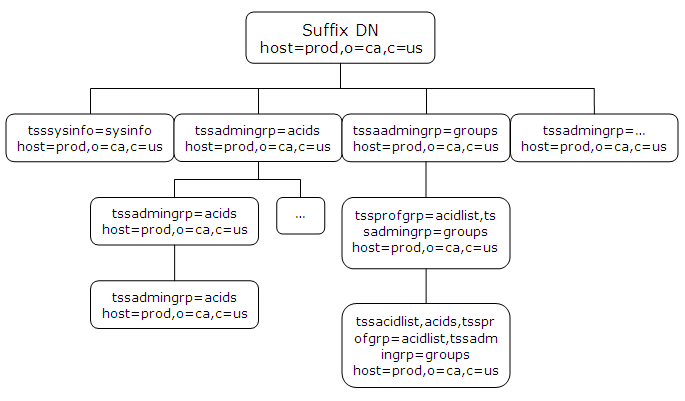
Object class used to start access to the objectclass hierarchy for a CA Top Secret database.
Object class used to create branches in the objectclass hierarchy below the host.
Object class used to create branches in the objectclass hierarchy below the host.
Values:
Object class used to access the ACID record fields of all user types.
Object class used to create the branches in the objectclass hierarchy below an acid.
The CA LDAP Server for z/OS contains different object classes than other LDAP servers. Before configuring a connection from the Policy Server to the CA LDAP Server, add the TSS objectclasses to certain Policy Server registry entries in the LDAP namespace. Substitute the replacement values for the default values of the following Policy Server registry entries:
Specifies the following registry entry location:
HKEY_LOCAL_MACHINE\SOFTWARE\Netegrity\SiteMinder\CurrentVersion\Ds.
Specifies the default value of the registry entry.
Specifies a new value containing the TSS objectclasses for the registry entry.
organization,organizationalUnit,groupOfNames,groupOfUniqueNames,group
class_filters_default_value,eTTSSAcidName,tssacidgrp,tssadmingrp
groupOfNames,groupOfUniqueNames,group
group_class_filters_default_value,eTTSSAcidName,tssacidgrp,tssadmingrp
organizationalPerson,inetOrgPerson,organization,organizationalUnit, groupOfNames,groupOfUniqueNames,group
policy_class_filters_default_value,eTTSSAcidName,tssacidgrp,tssadmingrp
Add the following TSS object classes to this registry entry:
|
TSS Objectclass |
Registry Key Type |
Data |
|
eTTSSAcidName |
REG_DWORD |
0x00000001(1) |
|
tssacid |
REG_DWORD |
0x00000001(1) |
|
tssacidgrp |
REG_DWORD |
0x00000002(2) |
|
tssadmingrp |
REG_DWORD |
0x00000003(3) |
Note: Some LDAP queries that the Policy Server issues (such as a full list of users) can take up to 60 seconds to complete. Under these conditions most of the queries from the Policy Server-side timeout. To improve connectivity, you can adjust this registry key entry as follows:
[HKEY_LOCAL_MACHINE\SOFTWARE\Netegrity\SiteMinder\CurrentVersion\Debug]
LDAPPingTimeout = 300; REG_DWORD
|
Copyright © 2012 CA.
All rights reserved.
|
|