

Using the Information Card Authentication Scheme (ICAS) feature of SiteMinder, you can create multiple information card authentication schemes. Each one is configured as a custom authentication scheme.
Information cards are like the physical cards that we carry in our wallets. Each information card represents a set of identity information. For example, an information card that represents a driver's license might contain the following sensitive identity information: photo, birth date, first and last name, and driver's license number.
Information cards let users manage their identity information. Users can view their information cards and the associated identity information. They can choose from the available cards for a given information exchange. And they can authorize the release of the identity information associated with a selected card.
Information cards are exposed by an Identity Selector.
An Identity Selector is an application that lets users manage their identity information and their online relationships with Relying Parties and Identity Providers. A Relying Party (RP) is the web site, application or service that requires identity information to authenticate the user. The Identity Provider (IdP) is a third party that authenticates identity information and creates security tokens that the user can share with the Relying Party.
Identity Selectors allow users to access Web-based resources without having to manage a multitude of user names and passwords. Likewise, businesses no longer have to maintain a database of user identity information that can be inaccurate, out-of-date, and vulnerable to misuse, thus reducing risk and liability and enhancing agility.
Identity Selectors also give the user control over exactly what identity information is released to each Relying Party. And finally, Identity Selectors provide users with a consistent user interface and better user experience.
Windows CardSpace, Microsoft's implementation of an Identity Selector, provides users with a consistent user interface for interacting with any Relying Party or Identity Provider. SiteMinder supports Windows CardSpace through a custom authentication scheme called Information Card Authentication Scheme (ICAS).
SiteMinder Information Card Authentication Scheme (ICAS) is a SiteMinder authentication scheme that supports Windows CardSpace. Each instance of ICAS is configured as a custom authentication scheme in the Administrative UI and implemented like any other SiteMinder custom authentication scheme.
Authenticating a user with SiteMinder ICAS is a process that involves these components and steps:
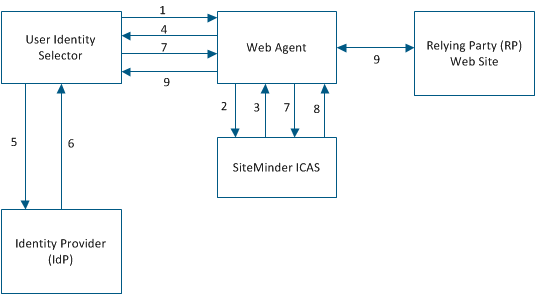
Note: The user can select a card that contains optional claims not required by the RP.
The following terms are useful for understanding ICAS:
An architecture that specifies how identity information can be shared by users, Relying Parties, and Identity Providers.
The person whose identity information is being shared. Sometimes, the user is called the subject.
The Web site that requests and consumes identity information.
A third party that authenticates identity information and shares the information with Relying Parties by creating security tokens. Credit card companies, banks, government agencies, employers, and insurance companies are all examples of Identity Providers.
The technology used by Identity Providers to create security tokens. A Security Token Service:
Note: SiteMinder supports SAML 1.0 and 1.1.
A cryptographically signed and encrypted set of claims.
An assertion of truth. Each token contains one or more claims about the user's identity. Examples of claims are first name, last name, email address, birth date, and so on. Claims can be made by the user or a third-party Identity Provider.
A set of identity information. Information cards are comparable to the physical cards that we carry in our wallets. For example, an information card that corresponds to a driver's license might contain the following sensitive identity information: photo, birth date, first and last name, driver's license number, state, height, and sex.
An information card that contains claims that the user asserts about himself, but that are not corroborated by a third party. A personal card contains a Private Personal Identifier (PPID) that is generated when the card is created. Personal cards are appropriate for low-sensitivity identity information, such as an email address.
Note: Personal cards are also called self-issued cards.
An information card contains claims that the user asserts about himself and that are corroborated by a third party. A managed card contains a Private Personal Identifier (PPID) that is generated when the card is created and a pointer to the Identity Provider's STS. Managed cards are appropriate for sensitive identity information, such as a credit card number.
An application that lets users manage their relationships with Relying Parties and Identity Providers and control how their identity information is shared and used. An identity selector:
Microsoft's Identity Selector for the Windows operating system.
Support for Windows Cardspace, Microsoft's Identity Selector, implemented in SiteMinder as a custom authentication scheme.
Identifier generated by the Identity Selector when an information card is created.
SiteMinder uses two files to configure each instance of ICAS: the fcc file and the properties file.
Specifies the authentication settings that SiteMinder requires and that can be customized for each instance of ICAS.
A sample fcc file that is shipped with the Web Agent kit
Specifies how an instance of ICAS behaves.
A sample properties file
Note: When configuring an instance of ICAS in the Administrative UI, the administrator specifies the path to the properties file.
|
Copyright © 2012 CA.
All rights reserved.
|
|