

This section contains the following topics:
How Single Sign-on Works in a Single Domain
Single Sign-On Across Multiple Domains
Single Sign-On and Authentication Scheme Protection Levels
Allow Automatic Access to Resources that use the OPTIONS Method
Track User Identity Across Anonymous Realms
Single Sign-on and Agent Key Management
How to Configure Single Sign-On
Configure Support for SDK Third-Party Cookies
Ignore the Cookie Provider for Unprotected Resources
Ignore the Cookie Provider for POST Requests
Implement Cookie Domain Resolution
Configure SecureUrls with Single Sign-on
Prevent Cookie Provider Replay Attacks
Integrate an IIS 6.0 Agent with SharePoint Portal Server 2003
Specify the Cookie Path for Agent Cookies
Agent Setting for Federation Domains
SiteMinder provides single sign-on functionality across single and multiple cookie domains. This simplifies using applications across different Web servers and platforms, and improves the user experience because the users do not have to re-authenticate as they move across a single sign-on environment.
A single domain is an environment where all resources exist in the same cookie domain. Multiple Web Agents in the same cookie domain can be configured for single sign-on if you specify the same cookie domain in each Web Agent’s configuration.
If single sign-on is enabled, it uses the following process:
Users who try to access resources with a higher protection level must re-authenticate before they are granted access.
The following illustration shows single sign-on in a single cookie domain:
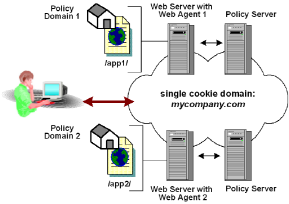
Note: If you are using replicated user directories with non replicated policy stores, the user directory must be named identically for all policy stores. Also, the session ticket key, which encrypts session tickets, must be the same for all key stores in the SSO environment. The session ticket determines the duration of a valid user session.
Without single sign-on, users are often required to log on and enter their credentials multiple times as they access different applications and resources on separate servers in different cookie domains. The ability to pass single sign-on information across multiple cookie domains enables a user to authenticate at a site in one cookie domain, and then go to a site in another cookie domain without being rechallenged for credentials. For the user, this seamless navigation makes related sites easier to use.
The following illustration shows single sign-on across multiple cookie domains.
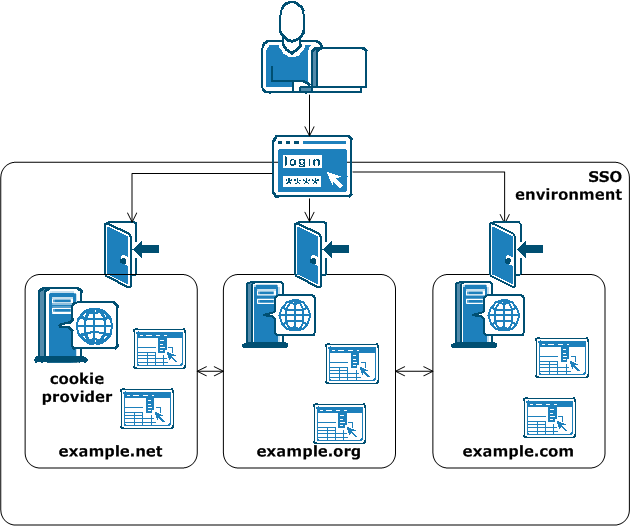
|
Copyright © 2012 CA.
All rights reserved.
|
|