

This section contains the following topics:
Use the Policy Server as a Radius Server
The RADIUS Client/Server Architecture
How RADIUS Authentication Works with the Policy Server
Policies in RADIUS Environments
Responses in RADIUS Policy Domains
Deploy SiteMinder in a RADIUS Environment
Guidelines for Protecting RADIUS Devices
How to Authenticate Users in a Homogeneous RADIUS Environment
Authenticate Users in Heterogeneous RADIUS Environments with One User Directory
How to Authenticate Users in Heterogeneous RADIUS Environments with Two User Directories
Remote Authentication Dial-In User Service (RADIUS) is a protocol that enables you to exchange session authentication and configuration information between a Network Access Server (NAS) device and a RADIUS authentication server. You can use the Policy Server as the RADIUS authentication server.
The RADIUS protocol is often used by NAS devices that serve as:
RADIUS is designed to simplify security by separating the communication technology provided by a NAS device from the security technology provided by the authentication server. RADIUS security protects remote access to networks and network services using a distributed client/server architecture. The Policy Server is the RADIUS server. The RADIUS client is the NAS device.
A NAS device performs one of the following:
The Policy Server can serve as the RADIUS authentication server when configured as described in this chapter. As the RADIUS server, the Policy Server authenticates RADIUS users using a RADIUS authentication scheme and a pre-defined user directory.
Note: To use RADIUS accounting, you must configure a separate RADIUS accounting server. The Policy Server will satisfy the NAS device by sending the ACK response to the accounting server. However, you can log accounting information to files.
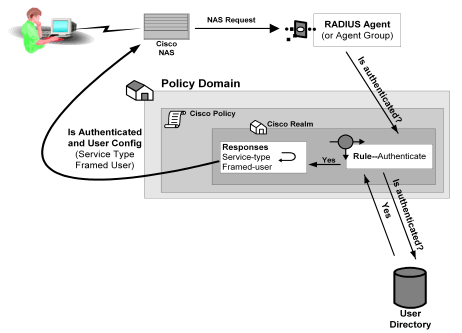
The Policy Server authenticates users through a series of communications with the NAS device. When SiteMinder authenticates a user, the NAS provides that user with access to the appropriate network services.
This authentication process is depicted in the following graphic:
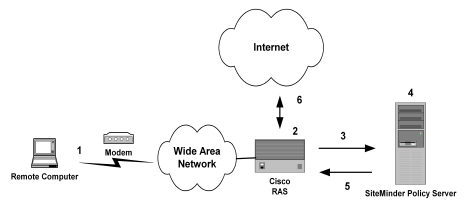
PAP is a PPP authentication protocol that provides a simple method for a host to establish its identity in a two-way handshake. Authentication takes place only upon initial link establishment and does not use encryption.
CHAP is also a secure PPP authentication protocol. CHAP provides a way to periodically verify the identity of a host using a three-way handshake and encryption. Authentication takes place upon initial link establishment. The RAS can repeat the authentication process any time after the connection takes place.
The RAS notifies the Policy Server that the session has begun and when the session ends.
A SiteMinder RADIUS policy is enforced by a RADIUS Agent and is created by binding the following elements together:
The basic structure of a policy is shown in the following diagram.
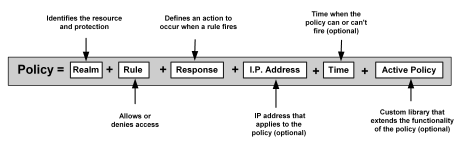
Although RADIUS policies are composed of the same elements that are contained in policies used by SiteMinder Agents, RADIUS Agents interpret the components differently. Rules, realms, and responses perform different functions, as shown in the following table.
|
Policy Component |
In a RADIUS Policy, this item: |
In a SiteMinder Agent Policy, this item: |
|---|---|---|
|
Realm |
|
|
|
Rule |
|
|
|
Response |
|
|
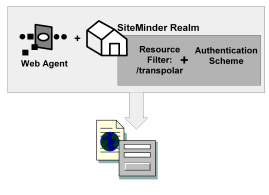
The elements of a RADIUS policy are treated differently in part because of how resources are identified in a RADIUS environment. In a SiteMinder Agent environment, specific resources are identified using a resource filter in the definition of the realm. The resource filter identifies the directory location of the resources. The realm definition also identifies the Web Agent and the authentication scheme, as shown in the following diagram:
As shown in the following diagram, protected resources are located differently in a RADIUS environment. Instead of the realm identifying the resource using a filter, the RADIUS Agent identifies the resource using a realm hint. A realm hint is an attribute that enables the Policy Server to establish the domain in which to authenticate users. The realm hint either identifies a specific realm that the Agent protects or signifies that the Agent must protect the entire NAS device.
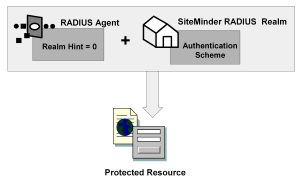
How does a RADIUS Agent protect a NAS device that must authenticate users in different domains, such as domainA and domainB? A realm hint is a RADIUS attribute that enables SiteMinder to determine the correct domain in which to authenticate a user. You must provide a RADIUS Agent with one of the following realm hint values:
When the realm hint is set to 1, the realm name is parsed from the user name attribute. The user_name-realm separator must be “@” or “/”.
The following diagram and explanation shows how a proxy server determines the correct SiteMinder domain in which to authenticate a user.
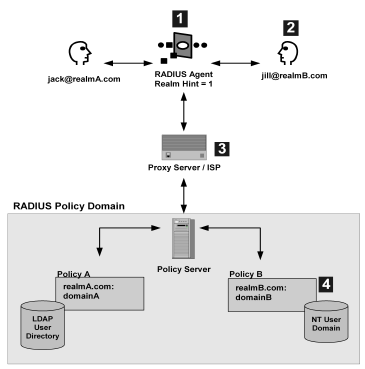
Example: jill@realmB.com, where jill is the user_name and realmB.com is the realm_name.
The Policy Server identifies the domain associated with the realm_name. The domain associated with realmB.com is domainB.
SiteMinder responses can be used to return RADIUS attributes to the NAS device if the user is authenticated. Attributes configure the characteristics of the session once the user is authenticated and define the user profile of the authenticated user. The user profile can be used by the NAS device. For example, using attributes in a response, you can define time limits for the RADIUS user session.
Using responses, you can provide the NAS device with user profile information that assigns privileges to the user. For example, you could allow one user unlimited access to a resource, yet limit another user’s access to the same resource. Used in this way, responses give you the ability to authorize users even though RADIUS is primarily only a mechanism for authentication.
Note: If the NAS specifies authentication only, by default, SiteMinder does not return RADIUS attributes. To return RADIUS attributes when the NAS specifies authentication only, follow the instructions in Configure SiteMinder to Always Return RADIUS Attributes.
RADIUS responses are paired with rules that authenticate. If a rule authenticates a user successfully, the RADIUS response is triggered. If the rule does not authenticate the user, the response is not triggered.
If a response is triggered, the Policy Server sends the attributes contained in the response to the NAS device. This information is used to customize the user’s session, as shown in the following diagram:
You can use the following attributes in responses:
These attributes return information associated with a user in an LDAP, WinNT, or ODBC user directory. User attributes are retrieved from the user directory and can used to modify the behavior of the RADIUS device.
These attributes return profile information associated with an LDAP directory object related to the user. For example, the DN attribute could return information about LDAP objects such as the user’s group or organizational unit (OU).
These attributes return values from a custom library that was developed using the SiteMinder Authorization API. An active response is generated when SiteMinder invokes a function in the custom library.
These attributes return values defined by the following Agent type attributes:
Generic RADIUS attributes, as defined by the RADIUS Protocol specification, Request for Comment (RFC) 2138. The identifiers for these attributes include 1-25 and 27-63. Some of these attributes may be used multiple times in the same response.
Any RADIUS Agent type can return a response that includes generic RADIUS attributes.
Attributes defined in the Dictionary file of the NAS device. These attributes define values that are not defined by generic RADIUS attributes and are specific to the type of NAS device in use. The unique identifiers for these attributes extend beyond the range reserved for generic RADIUS attributes, starting with 64. For example, Lucent provides an extended RADIUS attribute called Ascend-Disconnect-Cause, which uses the identifier 195.
Only Agent types that match the vendor type of the extended RADIUS attribute can use the attribute. For example, a Shiva Agent type can use the extended RADIUS attributes defined for Shiva, but a Cisco Agent type cannot use Shiva extended attributes in a response. The extended attributes that are used in a response must match the attributes defined in the Dictionary file of the RADIUS client.
By default, SiteMinder provides pre-defined RADIUS extended attributes for some Agent Types that use these attributes, such as Ascend (Lucent). You can also define additional RADIUS extended attributes for any of the RADIUS Agent types, if necessary.
Attributes defined in the Dictionary file of the NAS device, which use 26 as an identifier. Vendor-specific attributes enable you to define attributes for values that are not provided by the generic RADIUS attributes. Some vendors use vendor-specific attributes in place of or in addition to RADIUS extended attributes. For example, Cisco does not use RADIUS Extended attributes; however, this NAS device supports several vendor-specific attributes, such as Cisco AV–pair and Account-Info.
You can use vendor-specific attributes to pass information to other protocols. For example, you can define a vendor specific attribute for the Cisco AV–pair attribute to pass TACACS+ information to a TACACS+ server.
Vendor-specific attributes can only be defined in responses that match the vendor type of the RADIUS client.
By default, SiteMinder provides pre-defined vendor-specific attributes for some Agent Types that use these attributes, such as the Network Associates' Sniffer Agent type. You can also define additional RADIUS extended attributes to any of the RADIUS Agent types, if necessary.
Note: For more information about RADIUS attributes, see Request for Comment (RFC) RADIUS Protocol 2138.
Some NAS devices always expect RADIUS responses in the Access-Accept, even if the NAS specifies authentication only. If the NAS specifies authentication only, by default, SiteMinder does not return RADIUS attributes.
To always return RADIUS attributes to a NAS device, create a new registry value with the following parameters:
Note: The install program does not create a registry entry for AlwaysReturnRadiusAttrs. Until you create and set the entry, SiteMinder uses the default value of 0.
After you set AlwaysReturnRadiusAttrs to a value greater than zero, the following message will appear in the Authentication Server’s debug log:
Radius Attributes will be returned regardless of RA_SERVICE_TYPE_AUTHENTICATE_ONLY
Before you can use an attribute in a response, the attribute must be made available to the Agent type returning the response. Attributes are made available to Agent types by defining the attributes in Agent types. Although many Agent types are pre-configured with vendor-specific and RADIUS extended attributes, you can add additional extended RADIUS, generic RADIUS, and vendor-specific attributes to Agent types, as needed.
|
Copyright © 2012 CA.
All rights reserved.
|
|