

SiteMinder r12.0 introduced the EPM application. EPM is an application–centric access management model. EPM presents access management in the context of securing an application.
To protect an application, you are only required to provide data for configuration settings that do not have defaults. Modifying other settings is optional, and although not required, you can manage additional SiteMinder settings to modify EPM settings beyond the default settings to define more fine–grained protection.
If you are familiar with the core SiteMinder objects, there is a relationship between the application–oriented concepts and the underlying SiteMinder components. The following table summarizes this relationship.
|
Application Dialogs and Group Boxes |
Underlying SiteMinder Component |
|---|---|
|
General settings |
Defines the SiteMinder policy domain and the root location of the protected resources. |
|
Components |
Defines the realm and the location of the resources within the application that share the same security requirements. |
|
Resource |
Specifies the rule and the required authentication or authorization actions. |
|
Application Roles |
Replaces the function of user directory lookups. |
Unlike a SiteMinder policy object, you do not have to create the individual domain, realm, and rule objects. When you create the application, SiteMinder creates the objects automatically and binds them to identify resources, user populations, and the required actions when SiteMinder grants or denies access to the resource. As such, configuring an application does not require an understanding of these core objects.
Note: For more information about EPM applications, see the Policy Server Configuration Guide.
Which applications are you planning to secure? How do they map to the SiteMinder access management models?
Begin thinking about the individual applications in the organization and the individual resources (URLs) within each application that require the same level of protection. We recommend identifying the following:
Grouping resources in this way helps you map applications to the SiteMinder access management models.
When gathering information about each application, use a resource table similar to the following to help organization information:
|
Resource |
Domain/Application Resource Filter |
Realm/Component Resource Filter |
|---|---|---|
|
Example: Corporate Portal |
Example: Performance Management application |
Example: Manager resources |
Note: Identifying the applications that require protection also aids in capacity planning.
Defining a SiteMinder policy domain or an EPM application depends on identifying logical groups of resources, often an individual application, that are associated with one or more user populations. Grouping resources at this level helps you to identify the sets of individual resources (URLs) within an application that share the same security requirements.
Note: For more information about a SiteMinder policy domain or an EPM application, see the Policy Server Configuration Guide.
A strategy for determining these requirements is to review a site map of the organization.
For example, a fictitious company, has a corporate intranet that the following site map represents:
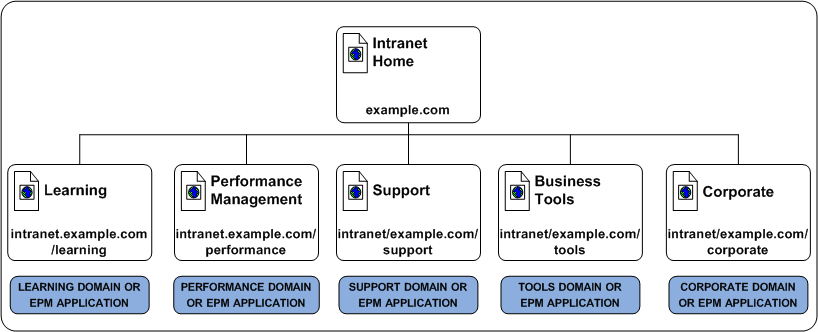
In this example, the corporate portal is separated into the following logical groups of resources:
The resource table for the corporate intranet looks like the following:
|
Resource |
Domain/EPM Application Filter |
Realm/Component Filter |
|---|---|---|
|
Corporate Intranet |
intranet.example.com |
N/A |
|
Learning |
intranet.example.com/learning |
N/A |
|
Performance Management |
intranet.example.com/performance |
N/A |
|
Support |
intranet.example.com/support |
N/A |
|
Business Tools |
intranet.example.com/tools |
N/A |
|
Corporate |
intranet.example.com/corporate |
N/A |
Defining a SiteMinder policy realm or an EPM component depends on identifying sets of individual resources (URLs) that share the same security or personalization requirements within a SiteMinder policy domain or EPM application. The contents of a realm or EPM component share the same authentication scheme. As a result, identifying these resources early in the process can help you determine the authentication schemes required to meet individual security requirements.
Note: For more information about SiteMinder policy realms and EPM components, see the Policy Server Configuration Guide.
For example, although the Performance Management and Business Tools applications each let a specific user population access the root of the application, each application contains additional SiteMinder policy realms or EPM components to provide a level of security or personalization appropriate for the resource:
Note: Although not illustrated, SiteMinder policy rules and EPM resources are used to control specific Web Agent, authentication, and authorization events. For more information, see the Policy Server Configuration Guide.
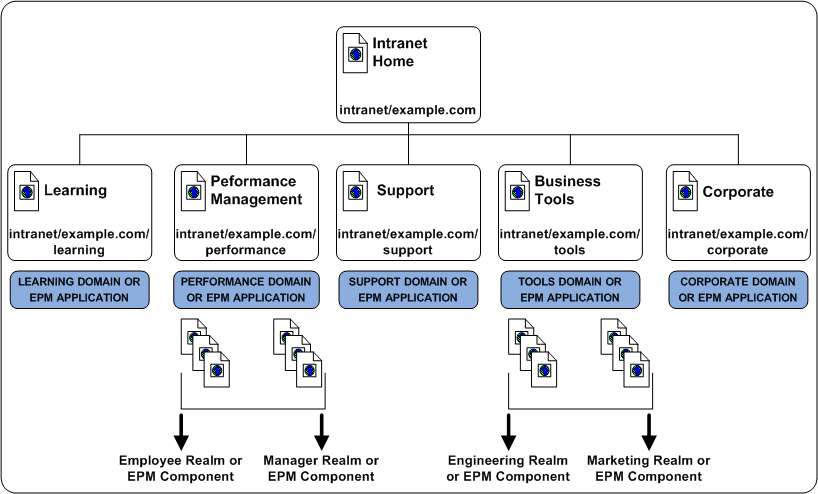
The resource table for the applications looks like the following:
|
Resource |
Domain/EPM Application Filter |
Realm/Component Filter |
|---|---|---|
|
Corporate Intranet |
intranet.example.com |
N/A |
|
Learning |
intranet.example.com/learning |
N/A |
|
Performance Management |
intranet.example.com/performance |
/employee /manager |
|
|
|
|
|
Support |
intranet.example.com/support |
N/A |
|
Business Tools |
intranet.example.com/tools |
/engineering /marketing |
|
|
|
|
|
Corporate |
intranet.example.com/corporate |
N/A |
SiteMinder can authenticate and authorize users through one or more connections to existing user stores in your enterprise network. After you identify the applications to secure, consider the following questions:
Identifying the stores each application uses helps you to:
Note: For more information about configuring user store connections within a domain, see the Policy Server Configuration Guide.
Note: For more information about directory mapping, see the Policy Server Configuration Guide.
When gathering information about each application, use a table similar to the following to organize information:
|
User Store Name |
User Store Type |
Authentication? |
Authorization? |
|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
SiteMinder supports multiple authentication methods to meet the varying levels of protection your resources require:
|
|
|
|
|
|
|
|
|
|
After you identify the applications to secure, in which we recommend identifying sets of resources (URLs) that share the same security requirements, consider the following questions:
Answering these types of questions helps you to
Note: For more information about configuring authentication schemes, see the Policy Server Configuration Guide.
When gathering information about each resource, we recommend organizing your information by the applications you plan on securing. For example, the following table assumes that an application is grouped into individual domains and realms, as detailed in applications to secure.
|
Resource |
URL |
Realm |
Authentication Method |
|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Do any security policies require your organization to manage user passwords? Do you anticipate managing user passwords in the future?
You can use SiteMinder password policies to enforce the password requirements of your enterprise. A password policy can validate the user's password against any of the following types of characteristics before accepting it:
Verifies the minimum or maximum length, the types of characters allowed, and if or how often any of those characters can be repeated in a password.
Verifies the time limits for how long the same password can be used, how long a password can remain inactive before it must be changed, and how long or how often before an expired password can be reused. You can specify one of the following responses for users with expired passwords:
Records the number of times the user has previously entered an incorrect password, and takes one of the following actions when that number is exceeded:
Note: For more information, see the SiteMinder Policy Server Configuration Guide.
|
Copyright © 2012 CA.
All rights reserved.
|
|