Federation Security Services Guide › Identify Service Providers for a SAML 2.0 Identity Provider › Configure Single Sign-on for SAML 2.0 › Indexed Endpoints Flow Diagram
Indexed Endpoints Flow Diagram
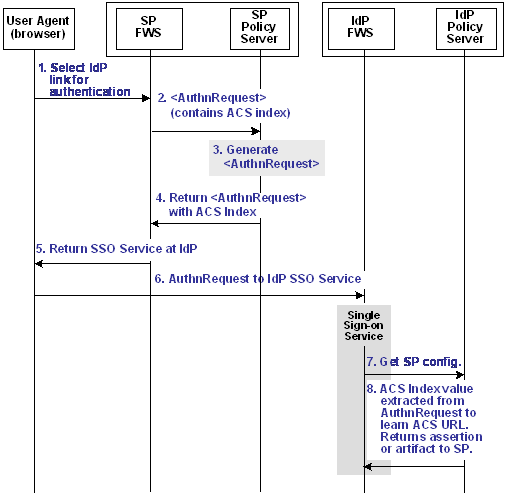
The following diagram shows how single sign-on works using an indexed endpoint.
Note: The Web Agent Option Pack or the SPS federation gateway can provide the FWS functionality.
Using indexed endpoints, the sequence of events is as follows:
- The user selects a link to authenticate with a specific IdP. The link contains the IdP ID and AssertionConsumerServiceIndex query parameters index as query parameters because the index feature is enabled.
- The SP Federation Web Services (FWS) application asks for an AuthnRequest from its local Policy Server. In the request it sends, it includes the IdP ID and optionally, the AssertionConsumerServiceIndex and ForceAuthn query parameters.
Note: A protocol binding is not part of the request because the ACS Index and the Protocol Binding parameters are mutually exclusive. The AssertionConsumerServiceIndex is already associated with a binding so there is no need to specify a Protocol Binding value. If the protocol binding and the AssertionConsumerServiceIndex are passed as query parameters in the AuthnRequest, the local Policy Server responds with an error denying the request.
- The AuthnRequest service extracts the IdP information from the SP Policy Server and generates the AuthnRequest message, which includes the AssertionConsumerServiceIndex. Because the AssertionConsumerServiceIndex is one of the query parameters, its value is checked against the IdP metadata collected from an IdP descriptor document previously sent from the IdP to the SP.
The AuthnRequest service reacts as follows:
- If the index for the artifact binding is set in the IdP metadata, this index is compared to the AssertionConsumerServiceIndex value. If the values match, the index value remains part of the AuthnRequest. If the index values do not match, the IdP metadata is checked to see if the AssertionConsumerServiceIndex corresponds to the POST binding.
- If the index corresponding to the HTTP-POST binding, this index value is again compared with the AssertionConsumerServiceIndex in the AuthnRequest. If the value of the AssertionConsumerServiceIndex parameter does not match the POST binding, the AuthnRequest service generates an error stating that the AssertionConsumerServiceIndex does not match the index in the IdP metadata.
- Assuming that the IdP metadata index and AssertionConsumerServiceIndex values match, the SP Policy Server generates the AuthnRequest.
- The SP Policy Server returns the AuthnRequest in an HTTP-redirect binding.
- The AuthnRequest is then redirected by the SP FWS application to the single sign-on service at the IdP. The SP knows the URL of the single sign-on service because the URL is part of the configuration information in the AuthnRequest.
- The browser requests the single sign-on service.
- The single sign-on service extracts the AssertionConsumerServiceIndex value from the AuthnRequest. The service determines the Assertion Consumer Service URL based on the AssertionConsumerServiceIndex, unless the value of the Index is not found in the SP metadata. If the Index is not found, an error is generated stating that an invalid AssertionConsumerServiceIndex is specified in the AuthnRequest message.
The Assertion Consumer URL is used by the single sign-on service to send the assertion or artifact to the SP, depending on the binding associated with the SP.
Note: If the AssertionConsumerServiceIndex parameter is not specified in the incoming AuthnRequest, the value of the Assertion Consumer Service and the corresponding binding are used by default.
