Federation Security Services Guide › Authenticate SAML 1.x Users at a Consumer › SAML 1.x Authentication Schemes › SAML 1.x POST Profile Authentication Scheme Overview
SAML 1.x POST Profile Authentication Scheme Overview
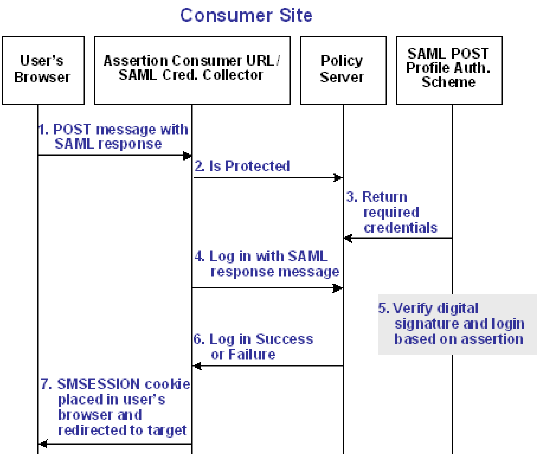
The following illustration shows how the SAML POST profile authentication scheme processes requests.
Note: The SPS federation gateway or the Web Agent Option Pack can provide the Assertion Consumer Service and SAML Credential Collector functionality necessary for the authentication process.
Unless otherwise stated, the following process takes place at the consumer site:
- A user's browser POSTs an HTML form to the Assertion Consumer URL (which is the URL for the SAML credential collector). This form contains a SAML response message and target URL originally generated at the producer.
- The SAML credential collector makes a call to the Policy Server to determine if the target resource is protected.
- The Policy Server replies that the target URL is protected by the SAML POST profile authentication scheme. This indicates to Federation Web Services application that a signed response from the POSTed form is the expected credential for the login call.
- The SAML credential collector makes a login call to the Policy Server, passing the digitally signed SAML response as credentials.
- The SAML POST profile authentication scheme verifies the signature and other fields of the response and the assertion.
- If the checks succeed and the user is found in the directory, then authentication succeeds. If any of the checks fail, authentication fails.
- Assuming login succeeds, the SAML credential collector sets an SMSESSION cookie, which it puts in the user's browser, and then redirects the user to the target resource. If the login fails, the credential collector redirects the user to the configured No Access URL.
