Federation Security Services Guide › Authenticate SAML 1.x Users at a Consumer › SAML 1.x Authentication Schemes › SAML 1.x Artifact Authentication Scheme Overview
SAML 1.x Artifact Authentication Scheme Overview
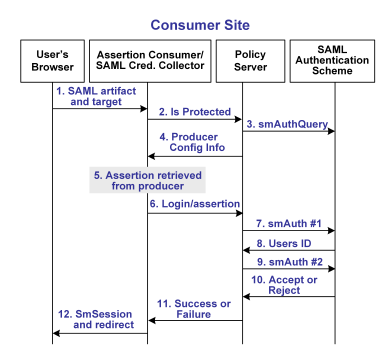
The following illustration shows how the SAML 1.x artifact authentication scheme processes requests.
This illustration shows the SAML 1.x artifact authentication functional model.
Note: The SPS federation gateway or the Web Agent and Web Agent Option Pack can provide the Agent and SAML Credential Collector functionality necessary for the authentication process.
Unless otherwise stated, all activity in this process occurs at the consumer site:
- A user is redirected to the SAML credential collector with a SAML artifact and a target URL.
The artifact and target is originally generated from the SiteMinder Web Agent at the producer site.
- The SAML credential collector calls the Policy Server to check if the requested resource is protected. This resource is protected by the SAML artifact authentication scheme.
- The Policy Server passes the necessary data to the SAML artifact authentication scheme, which extracts the producer configuration information, such as the affiliate name and password.
- The Policy Server returns the producer configuration information to the SAML credential collector. This information enables the credential collector servlet to call a producer site and retrieve a SAML assertion.
- The SAML credential collector takes the data from the Policy Server and uses it to retrieve the SAML assertion stored at the producer Policy Server.
- Once an assertion is returned, the credential collector uses the assertion as credentials, and logs in to the Policy Server.
- The Policy Server makes the initial user disambiguation call to the SAML authentication scheme.
- Using the authentication scheme data and the assertion, the scheme locates the user and returns a unique identifier for the user to the credential collector.
- The Policy Server makes the second user authentication call to the authentication scheme.
Note: The two-step authentication process is the standard authentication process as dictated by the SiteMinder Authentication API. For more information, see the SiteMinder Programming Guide for C or the SiteMinder Programming Guide for Java.
- The scheme validates the SAML assertion and returns an accept or reject message to the Policy Server.
- The Policy Server sends the accept or reject message to the credential collector.
- If the login to the Policy Server succeeds, the SAML credential collector creates a session cookie and places it in the user's browser then redirects the user to the target resource. If the login fails, the credential collector servlet redirects the user to a No Access URL.
