

CA SiteMinder® for Secure Proxy Server (CA SiteMinder® SPS) is a stand-alone server that provides a proxy-based solution for access control. CA SiteMinder® SPS employs a proxy engine that provides a network gateway for the enterprise and supports multiple session schemes that do not rely on traditional cookie-based technology.
This section contains the following topics:
Traditional Reverse Proxy Server Architecture
CA SiteMinder® SPS in an Enterprise
CA SiteMinder® SPS Support for Extranet Access Control
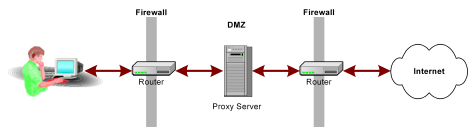
A traditional proxy server is located between a firewall and an internal network and provides caching of resources and security for the users on the internal network. Traditional proxy servers act as a proxy on behalf of a group of users for all resources on the Internet.
The following illustration shows a proxy server configuration. The proxy server caches frequently accessed resources so that requests for those resources are handled faster in the Demilitarized Zone (DMZ).
A reverse proxy server represents one or more destination servers. A typical use of reverse proxy architecture provides:
Rather than requesting a resource directly from a destination server, the reverse proxy server caches much of the content from the destination servers, providing ready access for users. This type of proxy server deployment is considered a reverse proxy, because the proxy is transparent to the user and works on behalf of the destination servers in the enterprise. Multiple reverse proxy servers can be used for load balancing and can also provide some SSL acceleration for HTTPS requests. A reverse proxy server also provides an additional layer of security by insulating destination servers that reside behind the DMZ.
CA SiteMinder® SPS is not a traditional reverse proxy solution, because it does not provide resource caching. CA SiteMinder® SPS serves as a single gateway for access to enterprise resources, regardless of the method of network access.
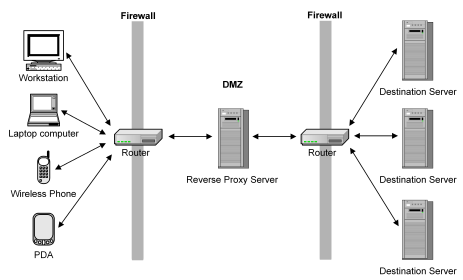
A set of configurable proxy rules determines how CA SiteMinder® SPS handles a user request. Users can access resources through multiple session schemes based on mapping between user agent types and virtual hosts. Requests can be routed to different destination servers based on the type of device being used to access the network.
The following illustration shows a configuration of CA SiteMinder® SPS. Users access CA SiteMinder® SPS using various devices. CA SiteMinder® SPS determines the session scheme to create based on the access device, and then forwards or redirects requests to the appropriate destination servers. Users are not aware that there is a reverse proxy server in the enterprise.
A stand-alone CA SiteMinder® SPS consists of an HTTP listener (Apache) and a Tomcat servlet container, as shown in the following illustration:
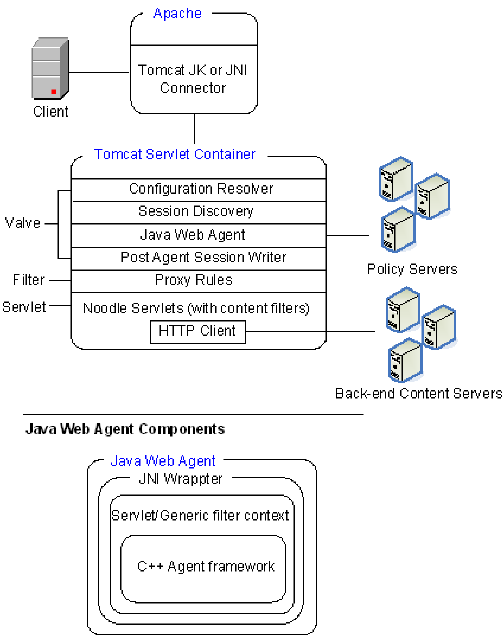
CA SiteMinder® SPS architecture includes the following components:
CA SiteMinder® SPS uses the open source Apache Web server to act as the HTTP listener for incoming requests. An additional component, mod_jk (1.2.18), acts as the Tomcat connector, which enables communication between the Apache Web server and Tomcat using the Apache JServ protocol (AJP).
The Tomcat server provides Tomcat servlet container for CA SiteMinder® SPS. The Tomcat initialization is customized so it does not allow deployment of any external applications or servlets. The standard Tomcat xml (server.xml) is not used for initialization. The components inside the Tomcat container of CA SiteMinder® SPS include the following:
The configuration resolver proxybootstrap is responsible for reading the CA SiteMinder® SPS configuration from the server.conf file and initializes the CA SiteMinder® SPS.
The session discovery component analyzes the incoming requests for extracting CA SiteMinder® SPS session information. Depending on the user agent type and the virtual host being used, this component uses the appropriate session scheme for extracting the CA SiteMinder® SPS session information.
If the request uses an existing CA SiteMinder® SPS session, this component uses the CA SiteMinder® SPS session identifier contained in the request to extract the corresponding SiteMinder session from the in-memory session store. CA SiteMinder® SPS passes the SiteMinder session to the Java Web Agent for session validation. If the request does not contain an existing CA SiteMinder® SPS session, this component passes the request on to the Java Web Agent for user authentication.
The Java Web Agent, together with the SiteMinder Policy Server, authenticates and authorizes the user.
The post Agent session writer performs additional processing for cookieless session schemes. After the Java Web Agent authenticates and authorizes the user and creates a SiteMinder session, this component creates a CA SiteMinder® SPS session identifier. This identifier is attached to the SiteMinder session created by the Java Web Agent.
This session identifier is then maintained in the in-memory session store of CA SiteMinder® SPS. In addition to maintaining the session in the session store, this component transforms the URI. For example, the Post Agent Session Writer manipulates the URI for the simple_url session scheme.
The proxy rules servlet filter loads the proxy rules from the proxyrules.xml file. Depending upon the incoming request and the proxy rule, the request is forwarded or redirected to the backend server. If the request is forwarded, an open source component Noodle is used.
Any changes made to the proxy rules do not require a restart for the changes to take effect. The proxyrules are reloaded when there is any change in the proxyrules.xml file.
The Noodle servlet forwards requests to the backend servers. Noodle also supports the use of proxy pre-filters which enable the request to be modified before sending the same to the backend server. Similarly support for proxy post-filters is also available which enables modification of the response received from the backend server before sending it back to the user client.
The HTTP client sends requests to the backend server and receives responses from the backend server.
CA SiteMinder® SPS offers the following features:
CA SiteMinder® SPS allows you to control the flow of HTTP and HTTPS requests to and from destination servers using an embedded SiteMinder web agent. In addition, CA SiteMinder® SPS is fully integrated with SiteMinder to manage e-business transactions.
The embedded web agent in CA SiteMinder® SPS enables single sign-on (SSO) across an enterprise, including SSO with SiteMinder Web agents that can be installed on destination servers within the enterprise.
A session scheme is a method for maintaining the identity of a user after authentication. Core SiteMinder products use cookies to maintain a session. CA SiteMinder® SPS, however, can maintain sessions based on SSL ID, mini-cookies, device IDs for handheld devices, URL rewriting, IP addresses, and schemes created using the Session Scheme API.
CA SiteMinder® SPS is equipped with an in-memory session store. The session store maintains session information. CA SiteMinder® SPS uses a token, such as a mini-cookie or SSL ID, to refer to the session information in the session store. Multiple session schemes and in-memory session storage enable CA SiteMinder® SPS to provide a solution for e-business management beyond computers, wireless devices such as PDAs and wireless phones.
Some enterprises prefer solutions that do not use cookie technology. Because of the session schemes and the session store built into CA SiteMinder® SPS, it offers a solution to enterprises that want an alternative to cookie-based session management.
Proxy rules allow you to configure different paths for fulfilling client requests from CA SiteMinder® SPS based on characteristics such as the requested virtual host or URI string. The proxy engine interprets a set of proxy rules to determine how to handle user requests.
By providing a single gateway for network resources, CA SiteMinder® SPS separates the corporate network and centralizes access control.
CA SiteMinder® SPS is designed to be scalable, manageable, and extensible.
The following conditions apply to CA SiteMinder® SPS:
Enterprises that provide access to network resources for employees, customers, and partners face a number of challenges, including:
SiteMinder provides solutions to many of these challenges, including authentication and authorization of users, and a complex engine for evaluating user entitlements. CA SiteMinder® SPS further expands the benefits of core Policy Server and Web Agent functionality by providing a reverse proxy solution.
This reverse proxy solution adds the following capabilities:
You can deploy CA SiteMinder® SPS in an enterprise to serve the following functions:
To limit access to destination servers and provide a central entry point to the network, CA SiteMinder® SPS can be placed in front of all destination servers in the enterprise. HTTP or HTTPS requests that come into the enterprise can be filtered through CA SiteMinder® SPS, and forwarded to the appropriate destination server for fulfillment.
The following illustration shows how CA SiteMinder® SPS handles all HTTP and HTTPS requests.
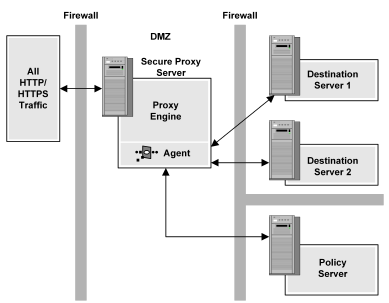
Destination servers that contain content do not require SiteMinder Web Agents. The only network element that resides behind the first firewall is CA SiteMinder® SPS. All users must be authenticated and authorized by SiteMinder residing behind the second firewall. The destination servers provide content after SiteMinder and CA SiteMinder® SPS verify user entitlements.
This deployment provides the following benefits:
CA SiteMinder® SPS uses proxy rules defined in XML configuration files to establish how CA SiteMinder® SPS handles requests. Proxy rules can be based on:
In addition, the conditions for proxy rules can be nested to create rules that incorporate multiple conditions.
All HTTP and HTTPS traffic passes through CA SiteMinder® SPS. Based on the proxy rules established for CA SiteMinder® SPS, requests are forwarded to the appropriate destination servers for fulfillment.
CA SiteMinder® SPS uses the built-in web agent to communicate with SiteMinder and perform authentication and authorization of requests.
Most solutions use cookie technology. However, when accessing resources over HTTP or HTTPS, some enterprises want alternatives for establishing and maintaining a user session and provide single sign-on with a cookieless solution.
CA SiteMinder® SPS provides an in-memory session store and allows the use of any of the following cookieless session schemes:
The following illustration shows a deployment in which CA SiteMinder® SPS provides a combination of standard sessions using cookies and sessions without cookies:
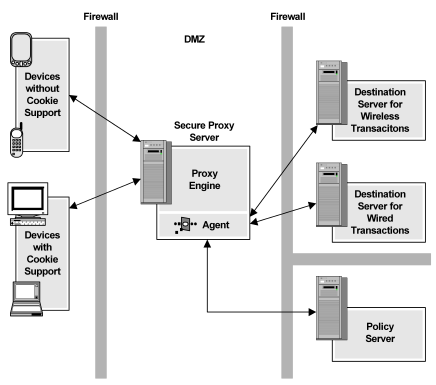
The deployment shown in the previous illustration provides the following benefits:
Through a set of proxy rules, CA SiteMinder® SPS forwards, or redirects, requests based on the type of device issuing the requests. For example, all initial requests can be directed at CA SiteMinder® SPS, which forwards requests to destination servers based on device types. Browser requests can be redirected to destination servers, and CA SiteMinder® SPS handles wireless requests.
Both standard SiteMinder cookies and cookieless session schemes are employed for maintaining user sessions. Session schemes are assigned based on user agent type for each virtual host. For example, all users accessing the network through web browsers are assigned to a standard cookie session scheme. Users accessing resource through a wireless telephone are assigned to a device ID session scheme.
Through an in-memory session store and the support of multiple session schemes, CA SiteMinder® SPS provides alternatives to cookie-based sessions. CA SiteMinder® SPS maintains session information in the session store and returns a token. This token is exchanged with all transactions, allowing CA SiteMinder® SPS to match the token to the session information captured in the session store.
CA SiteMinder® SPS, with its built-in handling of cookieless session schemes, enables it to be deployed in environments where the user agent, such as a wireless device, does not support traditional SiteMinder cookies.
If you deploy CA SiteMinder® SPS in a SiteMinder federation security services environment, the following process is enforced when a user request is received:
If CA SiteMinder® SPS is using a rewritable session scheme such as simple_url session scheme, CA SiteMinder® SPS rewrites the redirect response to include the session key information in the redirected URL.
Another deployment of CA SiteMinder® SPS provides access control for external users, but allows direct access to destination servers for internal users. If a destination server provides access to secure applications for individuals within the enterprise, a standard SiteMinder Web Agent can be installed on the destination server to provide access control. Users who are properly authenticated through CA SiteMinder® SPS can use single sign-on.
The following illustration shows an example of an extranet network deployment.

This deployment provides the following benefits:
All extranet traffic passes through CA SiteMinder® SPS and is forwarded to the appropriate destination server once users are authenticated and authorized for requested resources.
All information is located behind multiple firewalls to protect from extranet attacks. Information that is appropriate for intranet users does not incur the overhead of agent to SiteMinder communication. SiteMinder can still protect sensitive resources, however.
CA SiteMinder® SPS and intranet Web Agents use the same Policy Server and provide single sign-on for authorized extranet users on all destination servers.
|
Copyright © 2014 CA Technologies.
All rights reserved.
|
|