

Agent for Windows Authentication Guide › Introduction to the Federation Agent for Windows Authentication › NTLM Protocol
NTLM Protocol
NTLM includes various authentication and session security protocols. NTML is based on a challenge-response model, consisting of three types of messages exchanged in the following order:
- The client sends a type 1 message (negotiation) to the server. The type 1 message specifies the features supported by the client and requested of the server.
- The server sends a type 2 message (challenge) to the client. The primary function of this message is to challenge the identity of the client user.
- The client sends a type 3 message (authentication) to the server. The type 3 message includes the domain and user name of the client user and responds to the challenge in the type 2 message.
The following graphic shows how CA SiteMinder® Federation Standalone and the Federation Agent for Windows Authentication use the NTLM protocol:
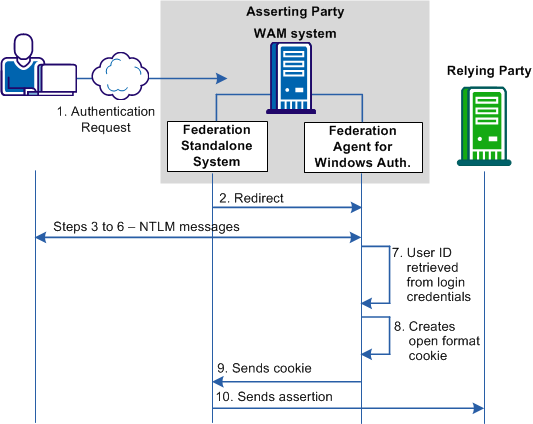
The following process references annotations in the preceding diagram:
- An authentication request is made to federation system at the asserting party.
- The federation system recognizes the request as a delegated authentication request and redirects to the request to the Federation Agent.
- The Agent sends a response back to the browser.
- If the browser is configured for IWA, the browser sends an NTLM Negotiate token (type 1 message) in the authorization header to the Federation Agent.
- The Federation Agent sends an NTLM Challenge token (type 2 message) to the browser.
- The browser sends an NTLM Authenticate token (type 3 message) to the Federation Agent.
- If a security context is associated with a user, the Federation Agent retrieves the user identity from the established context.
- The Agent creates an open format cookie containing the user identity information.
- The Agent sends the cookie to the federation system.
- The federation system sends an assertion to the relying party to complete federation processing.
Copyright © 2013 CA.
All rights reserved.
 
|
|


