

Enterprise applications and services are increasingly distributed across organizations. They have customers and partners who reside outside of the enterprise that need access to SharePoint applications within the enterprise. As a result, the need for secure but seamless access to SharePoint resources has increased.
CA SiteMinder® Agent for SharePoint lets you protect your SharePoint resources using CA SiteMinder® web access management capabilities. The federation capabilities allow partnering organizations to trust and share digital identities and attributes of employees, customers, and suppliers across trust domains. These trust domains can exist within one organization or between different organizations.
These federation capabilities also provide single sign-on across partner sites. The CA SiteMinder® Agent for SharePoint provides a custom CA SiteMinder® solution which issues claims and packages claims into security tokens, used to validate and access SharePoint resources.
The following section gives an overview about federation and claims-based authentication used in this solution.
Claims-based authentication enables applications to authenticate users with the minimum required information. Claims-based authentication allows applications to verify and validate user claims.
The following list explains the fundamental concepts of Claims-based authentication:
Claims represent any identity information about a user. In some instances, the user can be an application or a computer. A claim enables the user to gain access to multiple resources, such as applications and network resources, without entering credentials multiple times.
A claim is a statement about a user (for example, a name). The bits of identity information include, name, e-mail address, age, or organizational roles and responsibilities. A claim can also include the right of a user to perform something like access a file. Claims can also contain a restrictive right like the financial limit of a user.
A claim is given one or more values and then packaged in security tokens issued by a security token service (STS).
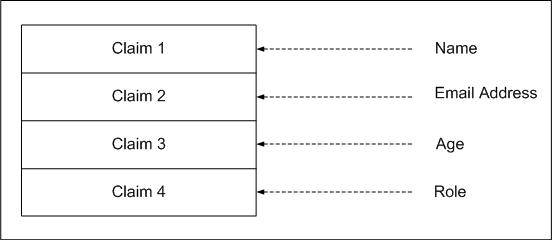
The previous illustration represents a claims token. The illustration shows claim values inside the token.
Claims information is transferred in security tokens. Each token contains a set of one or more claims, and contains information about the user to whom this token applies. A security token service (STS) issues the token.
Tokens can be issued in different formats, such as Security Assertion Markup Language (SAML) tokens or WS-Federation (WS-FED) tokens. Security tokens can be signed with an X.509 certificate to protect the contents of the token in transit. The application that receives the token validates it before using the claims.
The CA SiteMinder® Agent for SharePoint uses WS-FED tokens and X.509 certificates to protect its content.
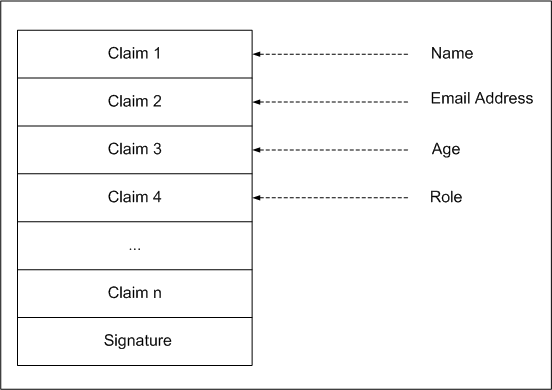
The previous illustration represents a security token. This token contains claim values and a digital signature.
The STS (Security Token Service) is a web service that issues, manages, and validates security tokens. STS makes assertions based on the evidence that it trusts, whoever trusts it.
An identity provider is a system that creates, maintains, and manages identity information and asserts identities to other service providers within a federation. For example, a user Adam, has an email address of adam@example.com and authenticated to this domain using a password mechanism.
An identity provider is also known as a SAML authority, asserting party, trusted identity provider, or source site, and is often abbreviated as IdP.
In the CA SiteMinder® Agent for SharePoint solution, the CA SiteMinder® Agent for SharePoint is the IdP STS. The identity provider owns the STS and affirms the tokens created by the STS.
A CA SiteMinder® claims provider uses virtual attribute mappings in your CA SiteMinder® directories to support searches of your CA SiteMinder® users with the SharePoint people picker.
The claims provider finds and selects user, group, and role-based claim values.
The following illustration provides a possible federation and claims-based authentication scenario.
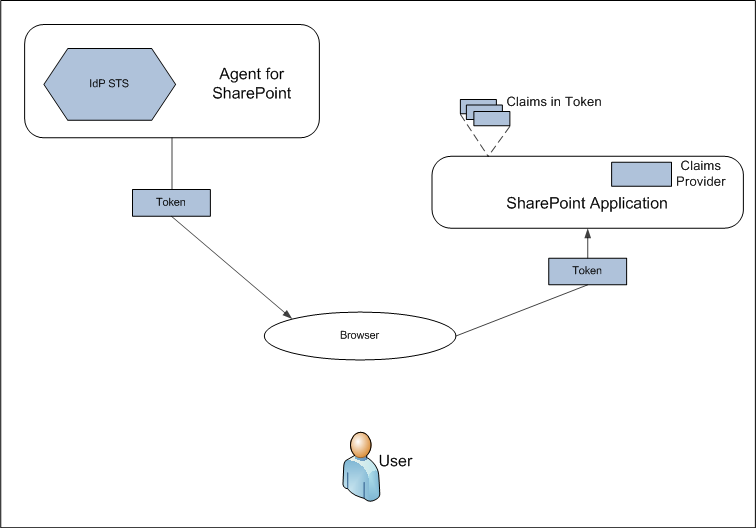
In the illustration, a SharePoint application works on behalf of a user, such as a web browser or another client. This SharePoint application asks an IdP-STS (CA SiteMinder® Agent for SharePoint) for a token containing claims for this user. An HTTP protocol makes the request, the IdP-STS authenticates the user in some way, such as verifying the password of the user. Therefore, the IdP-STS can be certain that the user is authentic.
The request sent to an IdP-STS typically contains a URI identifying the SharePoint application this user wishes to access. The IdP-STS asserts the identity of the user and the application. Once the STS finds account information and other attributes about the user and the application, it generates the token and returns it to the browser.
This release of the Agent for SharePoint includes a connection wizard that automatically creates the Federation objects it requires on your CA SiteMinder Policy Server. The connection wizard also creates a PowerShell script that you modify and run on your SharePoint central administration server. This PowerShell script creates the Trusted Identity provider (IdP).
|
Copyright © 2014 CA.
All rights reserved.
|
|