

The following illustration provides a possible federation and claims-based authentication scenario.
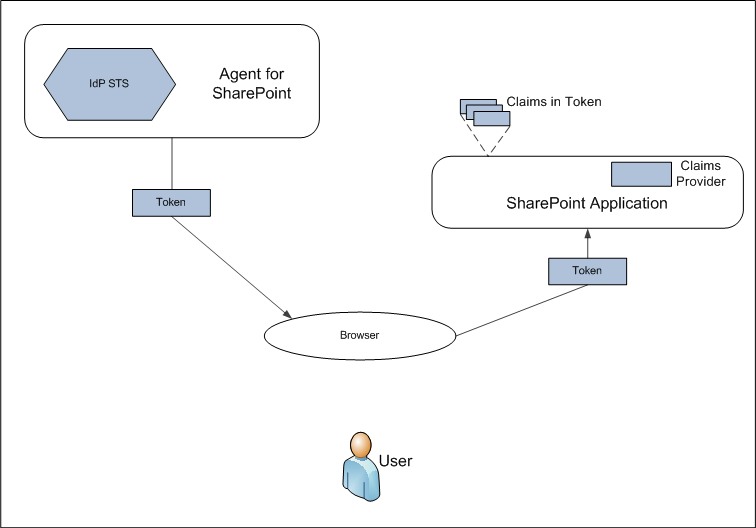
In the illustration, a SharePoint application works on behalf of a user, such as a web browser or another client. This SharePoint application asks an IdP-STS (Agent for SharePoint) for a token containing claims for this user. An HTTP protocol makes the request, the IdP-STS authenticates the user in some way, such as verifying the password of the user. Therefore, the IdP-STS can be certain that the user is authentic.
The request sent to an IdP-STS typically contains a URI identifying the SharePoint application this user wishes to access. The IdP-STS asserts the identity of the user and the application. Once the STS finds account information and other attributes about the user and the application, it generates the token and returns it to the browser.
|
Copyright © 2013 CA.
All rights reserved.
|
|