

In a SAML 2.0 federated environment, a Service Provider sometimes requires information about a user that is not provided in the assertion. The Service Provider can request the values of predetermined user attributes. If the Identity Provider does not have these values, it can request the values from a third party. In a CA SiteMinder® environment, this feature is referred to as a proxied attribute query.
The following diagram illustrates the process for enabling a proxied attribute query:
To enable a proxied attribute query, complete the following tasks:
The proxied attribute query feature is based on the SAML 2.0 Assertion Query/Request profile and extends the search for user attributes. The Attribute Authority first searches the user directory and the session store for attributes. If the attribute is not found and the user initially authenticated at a third-party IdP, the request can be forwarded to the third-party IdP.
To implement a proxied attribute query, a single CA SiteMinder® system acts as a relay point between two remote systems. To relay the request from one remote system to another, the single system takes on two roles. The system first serves as the Attribute Authority for the original Attribute Requester. The system also serves as an Attribute Requester to the third-party IdP. As the Attribute Requester, the system proxies the attribute query to the original IdP.
The following figure shows how a single system processes the proxied query:
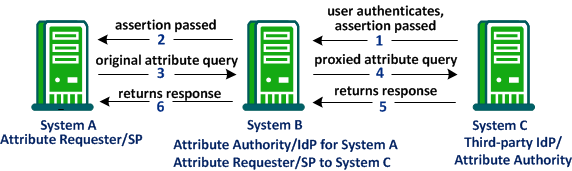
The following steps explain the flow of a proxied attribute query:
Important! The configured attribute names and the name format (unspecified, uri, or basic) at System A must match the names of these attributes at System C. This information is communicated before any transactions occurs.
To implement a proxied query transaction, configure two partnerships on the same CA SiteMinder® system:
For CA SiteMinder® to serve as an Attribute Authority, modify an existing IdP-to-SP partnership or create a partnership. In this partnership, CA SiteMinder® is the local IdP/Attribute Authority and the remote partner is the SP/Attribute Requester.
Note: This system also serves as the Attribute Requester in the SP-to-IdP partnership.
Follow these steps:
Note: Click Help for a description of fields, controls, and their respective requirements.
An example for an LDAP user directory is uid=%s. At least one search specification is required.
The system can now serve as an Attribute Authority to the original Attribute Requester.
To implement a proxied query transaction, configure two partnerships on the same CA SiteMinder® system:
Note: Partnership federation supports the SP as an Attribute Requester only for the proxied attribute query feature.
For CA SiteMinder® to serve as an Attribute Requester, modify an existing SP-to-IdP partnership or create a partnership. In this partnership, CA SiteMinder® is the local SP/Attribute Requester and the remote third party is the remote IdP/Attribute Authority.
Note: This system also serves as the Attribute Authority in the IdP-to-SP partnership.
Follow these steps:
Note: Click Help for a description of fields, controls, and their respective requirements.
The Service Provider can now serve as an Attribute Requester.
|
Copyright © 2013 CA.
All rights reserved.
|
|