

Policy Servers evaluate polices in the application tier and user credentials and attributes in the data tier to protect resources. Consider the following guidelines to performance tune the application tier:
CA SiteMinder® policies define how users interact with resources. When you create CA SiteMinder® policies in the Administrative UI, you link together (bind) objects that identify users, resources, and actions associated with the resources.
You can improve or degrade performance in the way you configure specific CA SiteMinder® components or by choosing to enable optional features. A performance strategy includes:
The business rules and security requirements of your enterprise should ultimately dictate your CA SiteMinder® policy design. The following guidelines are available to help you balance CA SiteMinder® performance, while meeting these requirements.
CA SiteMinder® requires that you configure core CA SiteMinder® policy objects in a specific order. The following diagram lists this order, where shaded items represents objects that affect performance during user authentication or authorization.
Note: The Host Configuration Object (HCO) and Agent Configuration Object (ACO) affect the performance of your Web tier.
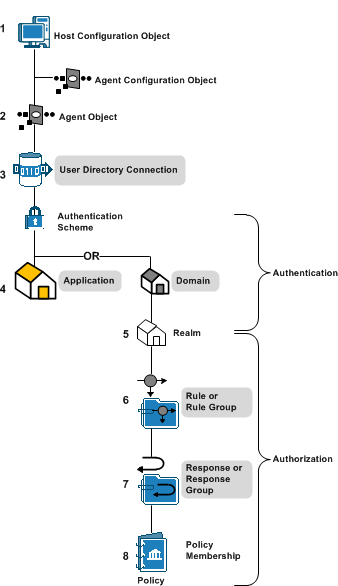
You can improve or degrade performance during authentication and authorization in the way you configure applications.
An application is a Policy Server object that defines a complete security policy for one or more related web services. Applications associate web service resources with user roles to specify entitlement policies that determine what web service users can access what web service application resources.
When you create an application, you bind it to one or more user directory connections against which the Policy Server attempts to authenticate users. Therefore, the number of directory connections, and order in which they are listed, directly affects CA SiteMinder® performance during authentication.
The number of web service ports and operations that are defined as protected resources in an application correlates to CA SiteMinder® performance during authorization.
Resources can be bound to one or more responses. When a resource is accessed, the associated response returns information to an agent, such as user attributes, DN attributes, static text, or customized active responses.
The types of responses you bind to web service resources directly correlate to CA SiteMinder® performance during authorization.
You can improve or degrade performance during authentication in the way you configure domains.
A CA SiteMinder® policy domain is a logical grouping of resources associated with one or more user directories. When you create a domain, you bind one or more user directory connections to the domain.
The Policy Server attempts to authenticate users using these directory connections. Therefore, the number of directory connections, and order in which they are listed, directly correlates to CA SiteMinder® performance during authentication.
Note: For more information about configuring domains, see the Policy Server Configuration Guide.
You can improve or degrade performance during authentication in the way you configure realms.
You group the resources in a domain into one or more realms. A realm is a set of resources (URLs) with a common security (authentication) requirement. The resource filter you define and the authentication scheme you select directly correlate to performance during authentication:
Realm settings also determine:
Note: For more information about realms, see the Policy Server Configuration Guide. For more information about authentication schemes, see the Policy Server Configuration Guide.
You can improve or degrade performance during authorization in the way you configure realms.
You create rules or rule groups in the context of a realm. Rules:
The resource filter you define in the rule, which is prefixed with the realm filter, identifies the resource that requires protection.
The Policy Server evaluates rules to determine which resource filter best matches the requested resource. Upon a match, the Policy Server fires the policies to which the rule is bound to determine if the user is authorized to access the resource.
The number of rules within a realm and how you define each of the resource filters directly correlates to CA SiteMinder® performance during authorization.
Note: For more information about rules, see the Policy Server Configuration Guide.
You can improve or degrade performance during authorization in the way you configure responses.
Responses or response groups are bound to specific rule or rule groups. When a rule fires, a response can:
Policies rules can be bound to one or more responses. The types of responses you bind to CA SiteMinder® policy rules directly correlates to CA SiteMinder® performance during authorization.
Note: For more information about responses, see the Policy Server Configuration Guide.
CA SiteMinder® performance during the authentication (IsAuthenticated?) step typically correlates with:
Authentication performance can improve or degrade depending on how you configure specific CA SiteMinder® policy objects or by choosing to enable optional features associated with those objects.
CA SiteMinder® requires that you configure core CA SiteMinder® policy objects in a specific order. The following diagram lists this order, where shaded items represent objects that affect performance during user authentication.
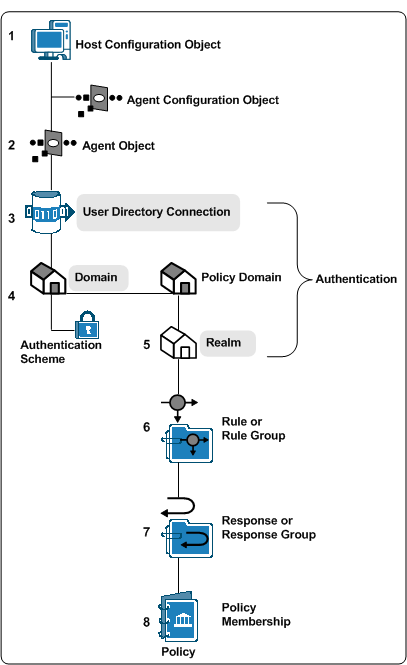
Configuring a domain requires that you bind one or more user directory connections to the domain. The Policy Server uses the search criteria you specify in the user directory connection to verify user credentials during the authentication step.
Note: For more information about configuring user directory connections, see the Policy Server Configuration Guide.
The following factors affect user authentication performance at the directory level:
Different CA SiteMinder® Web Services Security authentication schemes impose different level of WSS Agent processing overhead, which can also vary between WSS Agent types.
In general, authentication throughput is greater for authentication schemes that do not require digital signature verification or payload confidentiality.
Digital signature verification is more CPU- and data-intensive on WSS Agent for Web Servers, but also slightly impacts WSS Agents for application servers.
The following factors affect user authentication performance at the domain (or application object general) level:
Evaluate ways to reduce the number of directory connections in a domain to prevent unnecessary Policy Server requests. Consider:
The following factors affect user authentication performance at the realm (or application object component) level. Consider each as you configure realms:
Note: For more information about configuring authentication schemes, see the Policy Server Configuration Guide. For more information about using credential collectors, see the Web Agent Configuration Guide.
Some CA SiteMinder® features require persistent sessions. You can configure a realm for Persistent Sessions. Agents protecting resources in this realm write the session ticket a CA SiteMinder® session store, which results in additional requests to the session store for each authentication.
Important! Persistent sessions can have a significant impact on performance.
Note: For more information about user sessions, see the Policy Server Configuration Guide.
Evaluate the need for event actions that occur when users authenticate to gain access to a resource. If you do not require authentication actions, disable Authentication Events for the realm to speed the authentication step.
Note: For more information about realms, see the Policy Server Configuration Guide.
CA SiteMinder® performance during the authorization step typically correlates with:
The complexity of your CA SiteMinder® policy design affects each of these areas.
You can improve or degrade authentication performance in the way you configure specific CA SiteMinder® policy objects or by choosing to enable optional features associated with those objects. The following policy objects can affect performance during user authorization:
The following factors affect user authorization performance at the rule (or application object resource) level:
Note: For more information about rules, see the Policy Server Configuration Guide.
The following filters are listed in the order in which they have the smallest affect on performance:
Example: A company creates a customer realm (/customer) and specifies a rule with a specific page of their portal application (lending_home.html). The resulting resource filter is /customer/lending_home.html. Evaluating a match between the requested resource and the rule only requires the Policy Server to compare the requested resource with the resource filter to determine if it is a match.
Example: A company creates an employee realm (/employee) and specifies a rule with "*.html". The * prefix specifies that all html files in the employee realm are protected. The resulting resource filter is /employee /*.html. Evaluating a match between the requested resource and the resource filter requires the Policy Server to evaluate if the requested resource is part of the employee directory and is an HTML file.
The type of response attributes bound to rules in a CA SiteMinder® policy affect performance. The following response types are listed in the order in which they have the smallest affect on performance:
Note: This type of response requires the Policy Server to search the user directory.
Note: This type of response requires the Policy Server to search the user directory.
Policy membership is the part of a CA SiteMinder® policy that specifies which users apply to the policy. CA SiteMinder® policies are stored in domains, and as a result, you use filters to apply CA SiteMinder® policy membership to any or all users stored in the user directories bound to the domain. The type of filter you define determines how the Policy Server evaluates CA SiteMinder® policy membership.
Note: For more information about adding users to a CA SiteMinder® policy, see the Policy Server Configuration Guide.
The following filters are listed in the order in which they have the smallest affect on performance:
When CA SiteMinder® authenticates a user, the Policy Server issues a session ticket. The session ticket identifies the user directory in which the user is stored. The Policy Server only has to compare the session ticket with the directory bound to the CA SiteMinder® policy to determine that the policy applies to the user.
Note: For more information about user sessions, see the Policy Server Configuration Guide.
The organization or organizational unit, which contains the dn of the authenticated user, is stored in the session ticket. The Policy Server has to compare the session ticket information with the CA SiteMinder® policy membership filter to determine if the policy applies to the user.
The Policy Server must search each user group and all sub–groups in the directory to determine if the CA SiteMinder® policy applies to the user.
Important! Directories with deep group hierarchies can have a significant effect on the time it takes the Policy Server to evaluate policy membership.
Note: You can enable the User Authorization cache to reduce the number of requests the Policy Server makes to user directories to resolve policy membership.
The user authorization cache reduces the number of user directory requests to determine CA SiteMinder® policy membership by storing the relationship between users and policies.
Note: The user authorization cache does not store data about the user, store user attribute values, or cache user entries.
For example, three policies are configured to apply to an "Administrator" group, to which user A belongs. The first–time the Policy Server evaluates CA SiteMinder® policy membership, it must resolve the group membership and make three requests (one for each policy) to the user directory to determine that each CA SiteMinder® policy applies.
The Policy Server writes these results to the user authorization cache. Subsequent policy evaluation does not require the Policy Server to make user directory requests. Rather, the Policy Server uses the cached authorization information to determine policy membership.
Note: The Policy Server polls for policy updates periodically. The default interval is 60 seconds. If the policy membership changes, the Policy Server reloads the policy and removes the cache entries that are related to the updated policy.
The user authorization cache is most efficient when:
If these factors are not met, the efficiency of the User Authorization cache is reduced.
Example: the user authorization cache and agents configured to round–robin load balance
The more Policy Servers that are in the CA SiteMinder® agent round–robin pool, the greater the chance that the efficiency of the user authorization cache is reduced.
If a single CA SiteMinder® Agent is configured to round–robin between two Policy Servers, the first request for a protected resource results in a user authorization cache entry on one of the Policy Servers. There is approximately a 50 percent chance that the Policy Server that does not have the cache entry must service the second request. Moving forward, however, both Policy Servers have cached the data for subsequent requests.
Consider now, the effect of a single Agent configured to round–robin between 10 Policy Servers. After a Policy Server authorizes a user and enters the result in to the authorization cache, there is only a 10 percent chance that the same Policy Server services the next request. In this configuration, 5 cache misses must occur before there is a 50 percent chance of a cache hit.
Note: Policy Server clusters can reduce the effect round–robin load balancing has on the user authorization cache.
The default size of the user authorization cache is 10 MB. You can estimate the amount of space the user authorization cache requires and use the Policy Server Management Console to adjust the default size.
To estimate the size of the user authorization cache
expected_users * number_of_policies_per_session = entries
Specifies the total number of users authenticating to the applications CA SiteMinder® is protecting.
Specifies the average number of CA SiteMinder® policies that apply to a user during the session.
Note: Each CA SiteMinder® policy has the potential to enter a unique entry into the user authorization cache.
Specifies the number of cache entries authorizations can create.
(entries * .000062) + 1
Note: .000062 represents the approximate size of a cache entry in MB.
By default, the Policy Server writes audit events to a text file, which is known as the Policy Server log. Optionally, you can configure the Policy Server to log events to an audit database.
Note: For more information about configuring the Policy Server to log events to an audit database, see the Policy Server Administration Guide. For more information about configuring an audit database, see the Policy Server Installation Guide.
Consider the following factors if you decide to log events to an audit database:
Tuning the various CA SiteMinder® Agent parameters and following the CA SiteMinder® policy design guidelines may not significantly improve the amount of time it takes the Policy Server to service authentication and authorization requests.
When you have multiple Agents and Policy Servers, dynamic load balancing reduces latency and improves throughput because the Agents distribute requests among all of the Policy Servers.
|
Copyright © 2013 CA.
All rights reserved.
|
|