

In a federated network, the relying party can establish accounts for users federating from different asserting parties. Dynamic provisioning supports the process of creating client accounts with the necessary account rights and access privileges for accessing data and applications.
Remote provisioning employs a third-party provisioning application to create a user account. The application then passes the necessary information back to the Policy Server at the federation system with CA SiteMinder® Federation. The Policy Server uses the data to create a user credential.
Remote provisioning occurs at the relying party. The following figure shows a remote provisioning setup.
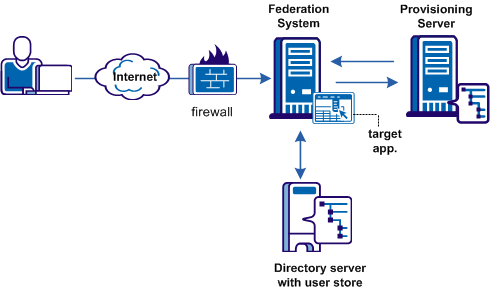
The high-level provisioning process is as follows:
The provisioning application can consume the open-format cookie using the CA SiteMinder® Federation Java or .NET SDK.
Note: The provisioning application must know the URI of the assertion consumer service at the relying party. For example, the SAML 2.0 URI for CA SiteMinder® as the relying party is https://sp_server:port/affwebservices/public/saml2assertionconsumer.
The redirect mode that you select for the target application determines the data delivery method to the target application.
To accomplish remote provisioning, CA SiteMinder® redirects the browser with the assertion data to the provisioning application.
CA SiteMinder® can pass the assertion data using one of these methods:
Delivers SAML assertion information in an open-format cookie. The cookie contains a login ID based on the assertion data.
Note: If you use the open-format cookie, the CA SiteMinder® system and the remote provisioning system must be in the same domain.
The cookie can be created in one of two ways:
If you select one of the FIPS algorithms (AES algorithms), use a CA SiteMinder® Federation SDK to generate the cookie. If you are planning to use the .NET SDK, use only the AES128/CBC/PKCS5Padding encryption algorithm. If the provisioning application uses .NET, the .NET SDK on the provisioning server reads the open format cookie.
The provisioning application must use the same language as the SDK that it is using to create a cookie. If you are using the CA SiteMinder® Federation Java SDK, the application must be in Java. If you are using the .NET SDK, the application must support .NET.
To create an open-format cookie without using a CA SiteMinder® Federation SDK, use any programming language. Review the details about the contents of the open-format cookie.
The language for writing the cookie must support UTF-8 encoding and any of the PBE encryption algorithms that you can select in the Administrative UI.
If you select FIPS-compatible (AES) algorithm to encrypt the cookie, the provisioning application must use an SDK to read the open-format cookie.
Verify that the open-format cookie gets set in the browser.
CA SiteMinder® can also pass assertion information as HTTP headers. If you use HTTP headers, the CA SiteMinder® system and the remote provisioning system can be in different domains.
Learn more about using HTTP headers to pass assertion data and how to protect the headers.
The delivery option is configurable in the Application Integration step of the partnership wizard.
After the user is redirected to the provisioning application, CA SiteMinder® no longer has control over the process. If provisioning a user account is a time-consuming process, the provisioning application is responsible for handling this situation. For example, by the application can send a message to the user explaining that provisioning is in process. This information lets the user know not to keep trying to log in before a user account is available.
To configure remote provisioning, determine a delivery option for the assertion data and supply the URL of the provisioning server.
In addition to configuring remote provisioning, you can select the Allow IdP to create User Identifier option. This option enables the IdP to create a persistent identifier if no identifier for the user exists. This Allow/Create feature is not exclusively for provisioning using local account linking, though it is required for the local method.
When you want the IdP to generate a user identifier that is sent with other attributes, you can enable the Allow/Create feature together with remote provisioning. The application at the remote provisioning server determines how it uses the generated identifier. The application can perform local account linking, but not CA SiteMinder® local account linking.
To configure remote provisioning
Note: Click Help for a description of fields, controls, and their respective requirements.
You have completed remote provisioning configuration.
|
Copyright © 2013 CA.
All rights reserved.
|
|