

The SAML Session Ticket authentication scheme provides a mechanism for single sign-on across web services that are protected by the same policy store. The scheme authenticates XML messages using credentials that are obtained from SAML Session Ticket assertions in an HTTP header, a SOAP envelope, or a cookie. SAML Session Tickets are strongly secure assertions that a SiteMinder WSS Agent in the same Policy Server domain generates after initial authorization of the request.
A SAML Session Ticket assertion is a data structure that contains a SiteMinder session ticket and a public key (both encrypted). The SAML Session Ticket authentication scheme uses the assertions to do the following operations:
By including the session ticket and the public key in the assertion, a web service consumer can access web services protected by SiteMinder WSS Agents in the same Policy Server domain without being rechallenged for credentials.

To configure CA SiteMinder® Web Services Security to validate user identities using SAML Session Ticket authentication, complete the following process:
SAML Session Ticket assertions can be placed the in a SOAP document, in an HTTP header separate from the XML document, or in a cookie as shown in the following illustration:
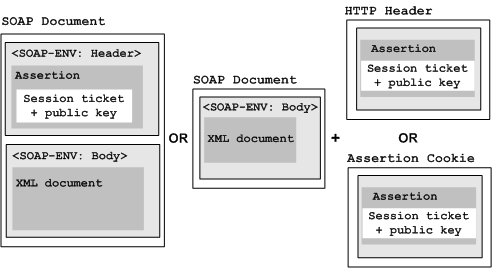
If a request message contains more then one associated assertion, assertions found within assertion cookies take precedence over assertions in the SOAP envelope or HTTP header. The SiteMinder WSS Agent first collects all SAML Session Ticket assertions from the cookie and the header or envelope as specified in the authentication scheme. The agent then tests each assertion until it finds the first one with a valid session ticket (that is, it can be decrypted with the agent key) and valid signatures, if they are required. Authentication is then performed using this assertion.
Note: If the authentication fails later in the authentication process because the first valid session ticket is found to be expired or revoked, authentication will fail—potential session tickets included in other assertions are not subsequently evaluated.
To obtain security information from SAML Session Ticket assertions in an HTTP header, a SOAP envelope, or a cookie that is associated with an incoming message, configure the SAML Session Ticket authentication scheme.
Follow these steps:
The Create Authentication Scheme pane opens.
Authentication scheme settings open.
The authentication scheme is saved. You can now assign it in application object components or realms.
|
Copyright © 2014 CA.
All rights reserved.
|
|