

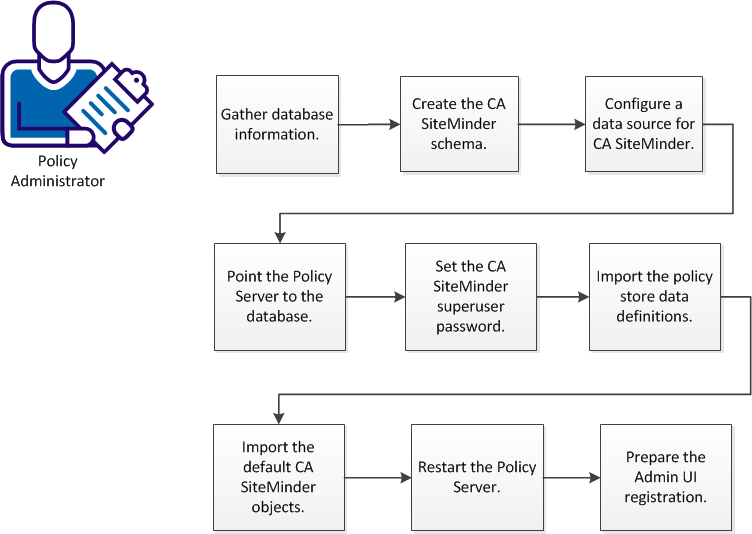
The following diagram depicts the process for configuring a PostgreSQL server database as a Policy Store:
Prerequisites:
Example:
smdatastore
Follow these steps:
Configuring a single PostgreSQL server database to function as a policy store or any other type of CA SiteMinder® data store requires specific database information.
Gather the following information before configuring the policy store or any other type of CA SiteMinder® data store:
Determine the name of the database instance that is to function as the policy store or data store.
Determine the user name and password of an account with privileges to create, read, modify, and delete objects in the database.
Determine the name you will use to identify the data source.
Example: SM PostgreSQL Server Wire DS.
Determine the name of the PostgreSQL server database that contains the instance that is to function as the policy store.
Determine the explicit path to where the Policy Server is installed.
Determine the IP Address of the PostgreSQL server database.
You create the CA SiteMinder® schema so that SQL Server database can store policy, key, session, and audit logging information.
Follow these steps:
The policy and key store schema is added to the database.
The policy store schema is extended.
sm_postgresql_logs.sql
Note: You are not required to configure the policy store to store additional CA SiteMinder® data. You can configure individual databases to function as a separate audit log database, key store, and session store.
The database can store CA SiteMinder® data.
ODBC requires that you configure a data source for the SQL Server wire protocol.
Follow these steps:
The ODBC Data Source Administrator appears.
Example: CA SiteMinder® Data Source.
Note: Take note of your data source name. This information is required as you configure your database as a policy store.
The connection settings are tested and a prompt appears specifying that the connection is successful.
The PostgreSQL data source is configured and appears in the System Data Sources list.
You configure the CA SiteMinder® ODBC data sources using a system_odbc.ini file, which you create by renaming postgresqlwire.ini, located in policy_server_installation/db, to system_odbc.ini. This system_odbc.ini file contains all of the names of the available ODBC data sources as well as the attributes that are associated with these data sources. This file must be customized to work for each site. Also, you can add additional data sources to this file, such as defining additional ODBC user directories for CA SiteMinder®.
The first section of the system_odbc.ini file, [ODBC Data Sources], contains a list of all of the currently available data sources. The name before the “=” refers to a subsequent section of the file describing each individual data source. After the “=” is a comment field.
Note: If you modify of the first line of data source entry, which is [CA SiteMinder® Data Source], take note of the change because you use this value when configure your ODBC database as a policy store.
Each data source has a section in the system_odbc.ini file describing its attributes. The first attribute is the ODBC driver to be loaded when this data source is used by CA SiteMinder®. The remaining attributes are specific to the driver.
Adding a PostgreSQL server data source involves adding a new data source name in the [ODBC Data Sources] section of the file, and adding a section that describes the data source using the same name as the data source. You need to change the system_odbc.ini file if you create a new service name or want to use a different driver. You have entries for the Oracle or SQL drivers under [CA SiteMinder® Data Source].
You configure the wire protocol driver to specify the settings CA SiteMinder® uses to connect to the database.
Note: This procedure only applies if the Policy Server is installed on a UNIX system. If you have not already done so, copy one of the following files and rename it system_odbc.ini. The file you rename depends on the database vendor you are configuring as a CA SiteMinder® data store.
These files are located in siteminder_home/db
The system_odbc.ini file contains the following sections. The data source that you are configuring determine the section or sections that you edit:
Specifies the settings CA SiteMinder® is to use to connect to the database functioning as the policy store.
Specifies the settings CA SiteMinder® is to use to connect to the database functioning as the audit log database.
Specifies the settings CA SiteMinder® is to connect to the database functioning as the key store.
Specifies the settings CA SiteMinder® is to connect to the database functioning as the session store.
Specifies the settings CA SiteMinder® is to connect to the database functioning as the sample user data store.
Follow these steps:
SiteMinder Data Source=DataDirect 7.1 PostgrSQL Server Wire Protocol
Driver=nete_ps_root/odbc/lib/NSpsql27.so Description=DataDirect 7.1 PostgreSQL Server Wire Protocol Database=SiteMinder Data Address=myhost, 1433 QuotedId=No AnsiNPW=No
Note: When editing data source information, do not use the pound sign (#). Entering a pound sign comments the information, which truncates the value. The truncated value can cause ODBC connections to fail.
Specifies the explicit path of the Policy Server installation, rather than a path with an environment variable.
Example: export/smuser/siteminder
Specifies the PostgreSQL Server database instance name.
Specifies the IP Address of the PostgreSQL Server database.
Represents the default listening port for PostgreSQL Server.
TraceFile=nete_ps_root/db/odbctrace.out TraceDll=nete_ps_root/odbc/lib/NStrc27.so InstallDir=nete_ps_root/odbc
Specifies the explicit path to the Policy Server installation directory. This path cannot contain an environment variable.
The wire protocol driver is configured.
You point the Policy Server to the database so the Policy Server can access the CA SiteMinder® data in the policy store.
Follow these steps:
ODBC
Policy Store
Note: We recommend retaining the 25 connection default for best performance.
Key Store
ODBC
Use the Policy Store database
Audit Logs
ODBC
Use the Policy Store database
The Policy Server is configured to use the database as a policy store, key store, and logging database.
The default CA SiteMinder® administrator account is named:
siteminder
The account has maximum permissions.
We recommend that you do not use the default superuser for day–to–day operations. Use the default superuser to:
Follow these steps:
Specifies the Policy Server installation path.
Note: The utility is at the top level of the Policy Server installation kit.
smreg -su password
Specifies the password for the default CA SiteMinder® administrator.
Limits:
Note: If you are configuring an Oracle policy store, the password is case–sensitive. The password is not case–sensitive for all other policy stores.
The password for the default CA SiteMinder® administrator account is set.
Importing the policy store data definitions defines the types of objects that can be created and stored in the policy store.
Follow these steps:
Specifies the Policy Server installation path.
XPSDDInstall SmMaster.xdd
Imports the required data definitions.
Importing the default policy store objects configures the policy store for use with the Administrative UI and the Policy Server.
Consider the following items:
Specifies the Policy Server installation path.
Follow these steps:
XPSImport smpolicy.xml -npass
XPSImport smpolicy-secure.xml -npass
Specifies that no passphrase is required. The default policy store objects do not contain encrypted data.
Both files include the default policy store objects. These objects include the default security settings in the default Agent Configuration Object (ACO) templates. The smpolicy–secure file provides more restrictive security settings. For more information, see Default Policy Store Objects Consideration.
XPSImport ampolicy.xml -npass
XPSImport fedpolicy-12.52 SP1.xml -npass
The policy store objects are imported.
Note: Importing smpolicy.xml makes available legacy federation and Web Service Variables functionality that is separately licensed from CA SiteMinder®. If you intend on using the latter functionality, contact your CA account representative for licensing information.
Enable the advanced authentication server as part of configuring your Policy Server.
Follow these steps:
Note: If you are installing another (nth) Policy Server, use the same encryption key for the Advanced Authentication server that you used previously.
The advanced authentication server is enabled.
You restart the Policy Server for certain settings to take effect.
Follow these steps:
The Policy Server stops as indicated by the red stoplight.
The Policy Server starts as indicated by the green stoplight.
Note: On UNIX or Linux operating environments, you can also execute the stop-all command followed by the start-all command to restart the Policy Server. These commands provide an alternative to the Policy Server Management Console.
You use the default CA SiteMinder® super user account (siteminder) to log into the Administrative UI for the first–time. The initial login requires that you to register the Administrative UI with a Policy Server, which creates a trusted relationship between both components.
You prepare for the registration by using the XPSRegClient utility to supply the super user account name and password. The Policy Server uses these credentials to verify that the registration request is valid and that the trusted relationship can be established.
Consider the following items:
Follow these steps:
XPSRegClient siteminder[:passphrase] -adminui-setup -t timeout -r retries -c comment -cp -l log_path -e error_path -vT -vI -vW -vE -vF
Specifies the password for the default CA SiteMinder® super user account (siteminder).
Note: If you do not specify the passphrase, XPSRegClient prompts you to enter and confirm one.
Specifies that the Administrative UI is being registered with a Policy Server for the first–time.
(Optional) Specifies the allotted time from when you to install the Administrative UI to the time you log in and create a trusted relationship with a Policy Server. The Policy Server denies the registration request when the timeout value is exceeded.
Unit of measurement: minutes
Default: 240 (4 hours)
Minimum Limit: 15
Maximum Limit: 1440 (24 hours)
(Optional) Specifies how many failed attempts are allowed when you are registering the Administrative UI. A failed attempt can result from submitting incorrect CA SiteMinder® administrator credentials when logging in to the Administrative UI for the first time.
Default: 1
Maximum Limit: 5
(Optional) Inserts the specified comments into the registration log file for informational purposes.
Note: Surround comments with quotes.
(Optional) Specifies that registration log file can contain multiple lines of comments. The utility prompts for multiple lines of comments and inserts the specified comments into the registration log file for informational purposes.
Note: Surround comments with quotes.
(Optional) Specifies where the registration log file must be exported.
Default: siteminder_home\log
siteminder_home
Specifies the Policy Server installation path.
(Optional) Sends exceptions to the specified path.
Default: stderr
(Optional) Sets the verbosity level to TRACE.
(Optional) Sets the verbosity level to INFO.
(Optional) Sets the verbosity level to WARNING.
(Optional) Sets the verbosity level to ERROR.
(Optional) Sets the verbosity level to FATAL.
XPSRegClient supplies the Policy Server with the administrator credentials. The Policy Server uses these credentials to verify the registration request when you log in to the Administrative UI for the first–time.
|
Copyright © 2014 CA.
All rights reserved.
|
|