

This section contains the following topics:
Use Case: Single Sign-on Based on Account Linking
Use Case: Single Sign-on Based on User Attributes
Use Case: Single Sign-on with No Local User Account
Use Case: SAML 2.0 Single Logout
Use Case: WS-Federation Sign-out
Use Case: Identity Provider Discovery Profile
Use Case: Federation with Multiple SSO Profiles
Use Case: SAML 2.0 User Authorization Based on a User Attribute
Use Case: Single Sign-on with No Name ID at the IdP
Use Case: SSO Using Security Zones
Use Case: SSO with Dynamic Account Linking at the SP
In this use case, smcompany.com contracts with a partner, ahealthco.com to manage employee health benefits.
An employee of smcompany.com authenticates at an employee portal at the company website, smcompany.com and clicks a link to view her health benefits at ahealthco.com. The employee is taken to the ahealthco.com web site and is presented with the correct health benefit information without having to sign on to the website.
The following illustration shows this use case.
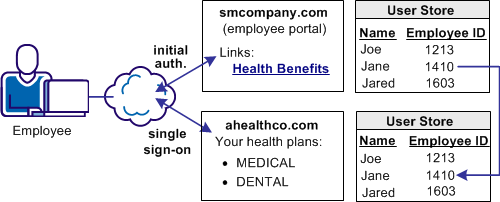
Account linking can be used for browser-based single sign-on, where each partner maintains separate user accounts for the same user. Account linking uses the SAML assertion to associate a federated identifier with the local identity at a partner.
In this use case, ahealthco.com maintains all health-related information and user identities for every employee at smcompany.com. When an employee of smcompany.com accesses ahealthco.com, an identifier for the employee is passed from smcompany.com to ahealthco.com in a secure manner. This identifier allows ahealthco.com to determine who the user is and the level of access to allow for that user.
Federation can be deployed at smcompany.com and ahealthco.com to solve Use Case: Single Sign-on Based on Account Linking.
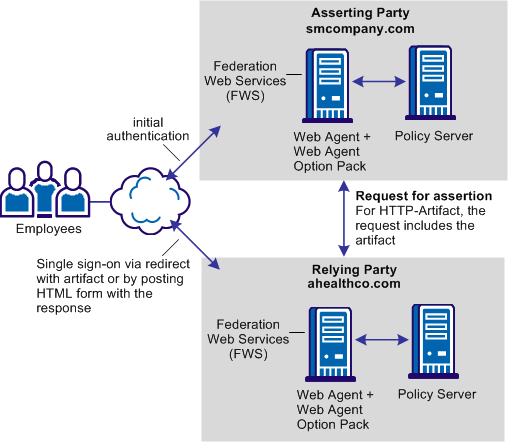
CA SiteMinder® is deployed at both sites. The Web Agent with the Web Agent Option Pack are installed on a webserver system and the Policy Server is installed on another system. The installations are the same for smcompany.com and ahealthco.com.
The FWS application provides the servlets which retrieve assertions for the HTTP-Artifact profile and which consume assertions.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
In this example, smcompany.com is the producer. The administrator at smcompany.com configures a SAML 1.1 producer-to-consumer partnership between smcompany.com and ahealthco.com. This partnership uses the HTTP-Artifact profile for single sign-on.
The partnership at smcompany.com has the following information:
An employee of smcompany.com logs into the company site and is initially authenticated by the Web Agent. The employee of smcompany.com accesses the employee portal web site and the sequence of events is as follows:
Ahealthco.com is the consumer site. The administrator at ahealthco.com configures a consumer-to-producer partnership with smcompany.com. This partnership uses the HTTP-Artifact profile for single sign-on.
The partnership configuration has the following information:
Ahealthco.com receives the assertion and the sequence of events follows:
In this example, smcompany.com is the producer. The administrator at smcompany.com configures a producer-to-consumer partnership. The partnership uses SAML 1.x POST profile for single sign-on.
The partnership configuration has the following information:
When an employee of smcompany.com accesses the employee portal site, the sequence of events is as follows:
Ahealthco.com is the consumer site. The SAML credential collector service at ahealthco.com handles the SAML response. The administrator at ahealthco.com configures a consumer-to-producer partnership with smcompany.com that uses the SAMl 1.1 HTTP-POST profile for single sign-on.
The partnership configuration has the following information:
The sequence of events is as follows:
In this example, smcompany.com is the Identity Provider. The administrator at smcompany.com configures an IdP-to-SP partnership with ahealthco.com as the remote SP.
The partnership configuration contains the following information:
An employee accesses the employee portal site and the following sequence of events occurs:
Ahealthco.com is the Service Provider. The administrator at ahealthco.com configures an SP-to-IdP partnership with smcompany.com, which uses the artifact profile. The partnership configuration has the following information:
The sequence of events is as follows:
In this example, smcompany.com is the Identity Provider. The administrator at smcompany.com configures an IdP-to-SP partnership. The partnership uses SAML 2.0 HTTP-POST profile for single sign-on.
The partnership configuration has the following information:
An employee of smcompany.com logs in to the employee portal site.
After a successful initial authentication, the following sequence occurs:
The Identity Provider initiates the request, which triggers an unsolicited response.
Ahealthco.com is the Service Provider. The administrator at ahealthco.com configures an SP-to-IdP partnership with smcompany.com. The configuration uses the SAML 2.0 HTTP-POST profile for single sign-on.
The partnership configuration has the following information:
The sequence of events at ahealthco.com is as follows:
In this example, smcompany.com is the Identity Provider. The administrator at smcompany.com configures a WSFED IP-to-RP partnership. The partnership uses the WS-Federation Passive Requester profile for single sign-on. In this use case, ahealthco.com, the Resource Partner, initiates single sign-on.
The SAML token type is SAML 1.1. This part of the IP entity configuration.
The partnership configuration has the following information:
When an employee of smcompany.com accesses the employee portal, the following sequence of events occurs:
Ahealthco.com is the Resource Partner.
The partnership configuration has the following information:
The sequence of events is as follows:
In Use Case 2, smcompany.com buys parts from a business partner named partsco.com.
An engineer authenticates at smcompany.com and clicks a link to access information at partsco.com. As an engineer at smcompany.com, the user is taken directly to the Specifications portion of the partsco.com website without having to log in.
A buyer for smcompany.com authenticates and clicks a link for partsco.com. The buyer is taken directly to the Parts List portion of the partsco.com website. The buyer does not have to log in.
The following graphic shows the relationship between the two partners.
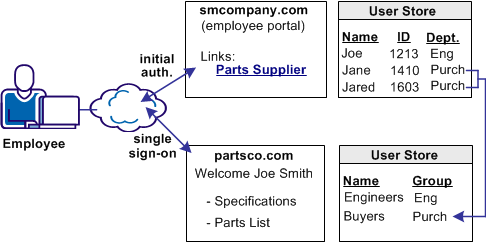
Other attributes, such as the user name are passed from smcompany.com to partsco.com to personalize the interface for the individual user.
Partsco.com does not want to maintain user identities for all smcompany.com employees, but the company wants to control access to sensitive portions of the website. To control the access, partsco.com maintains a limited number of identities for users at smcompany.com. One identity is maintained for Engineers and one identity is maintained for Buyers.
When an employee of smcompany.com accesses partsco.com, smcompany.com sends user attributes in a secure manner to partsco.com. Partsco.com uses the attributes to determine which identity controls access for the user.
Federation can be deployed at smcompany.com and partsco.com to solve Use Case: Single Sign-on Based on User Attribute Profiles.
The illustration is similar for SAML 1.1, SAML 2.0, and WS-Federation.
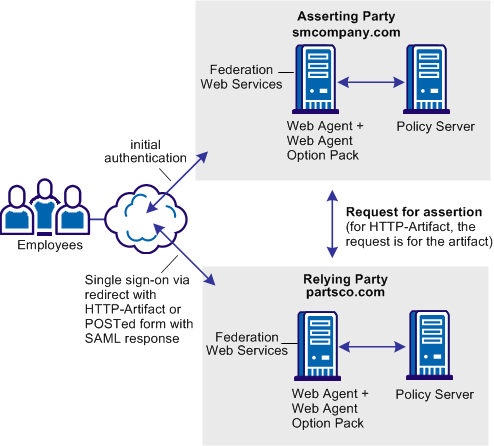
CA SiteMinder® is deployed at both sites. The interaction between the user and each site is similar, where partsco.com is acting as the relying party. The Federation Web Services application contains all the necessary servlets to process the transaction.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The sequence of events is similar to the solution for Single Sign-on based on Account Linking, except for the following items:
In this use case, smcompany.com offers employee discounts by establishing a partnership with discounts.com.
An employee authenticates at smcompany.com and clicks a link to access discounts.com. The employee is taken to the discounts.com website and is presented with the discounts available for smcompany.com employees, without logging in to the discounts.com website.
The following illustration shows this use case.
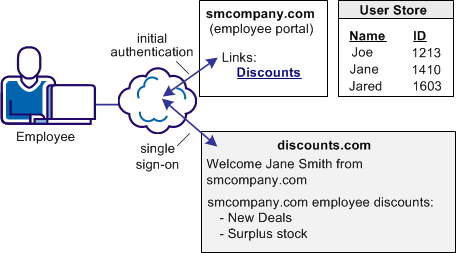
Discounts.com does not maintain any identities for smcompany.com. The company allows all employees of smcompany.com to access discounts.com as long as they have been authenticated at smcompany.com. Smcompany.com sends authentication information about the user requesting a resource to discounts.com in a secure manner so access is permitted.
Federation is deployed at smcompany.com and discounts.com to solve Use Case: Single Sign-on with No Local User Account.
The following figure shows single sign-on with no local user account. SAML 1.1 is the SSO profile in use.
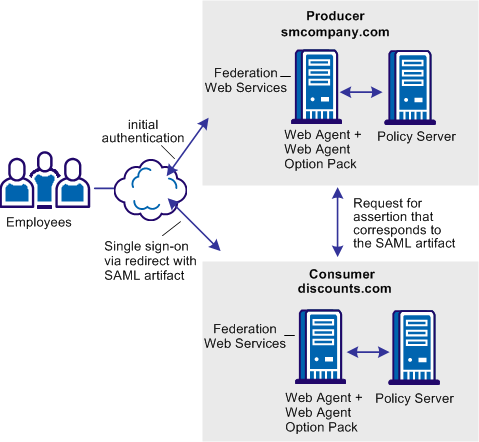
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
In this deployment, CA SiteMinder® is at both sites. Smcompany.com is the SAML 1.1 producer. The administrator at smcompany.com configures a SAML 1.1 partnership that includes a remote entity representing discounts.com. Any attributes that are configured in the partnership get included in the assertion.
For this solution to work, every user must map to a single user account, making the single user essentially an anonymous user.
When an smcompany.com employee accesses the employee portal, the following process occurs:
Discounts.com is the consumer site. The administrator at discounts.com configures an SP-to-IdP partnership. The partnership configuration specifies the location of the assertion retriever service at smcompany.com, and the protected target resources.
The user identification configuration for the partnership must specify a custom user search specification that looks up a single user. For example, if the user directory is LDAP, the search specification is uid=user1.
Important! To map every user to a single user, a user directory at discounts.com must exist. This user directory must contain a single user record. An alternative is to create a user directory using the Policy Server API that returns the same user record.
The following process occurs:
In this use case, an employee of smcompany.com authenticates at the employee portal and selects a link to view the health benefits at ahealthco.com. The employee is taken to the ahealthco.com website and presented with the health benefit information without logging in to the site.
After the employee logs out from ahealthco.com, the site wants to verify the termination of the user session at ahealthco.com and at smcompany.com. Terminating both sessions prevents an unauthorized employee from using the existing session to access resources at smcompany.com or to view benefits of the authorized employee.
Note: In this case, the initial logout occurs at ahealthco.com and results in both sessions being terminated.
The following illustration shows the use case.
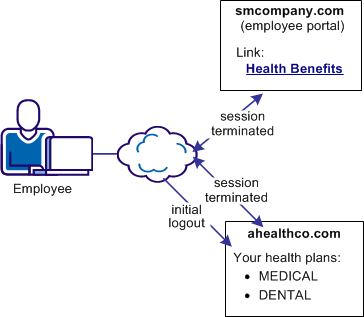
You can use federation to solve Use Case: SAML 2.0 Single Logout.
In this solution:
The following figure shows the solution for single logout.
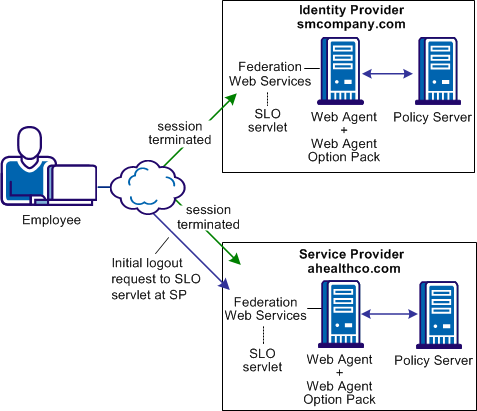
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The following sequence of events for SP-initiated single logout occurs:
Note: The termination does not remove the session from the session store; it sets the state to LogoutInProgress.
Note: Other Service Providers are not identified in the illustration.
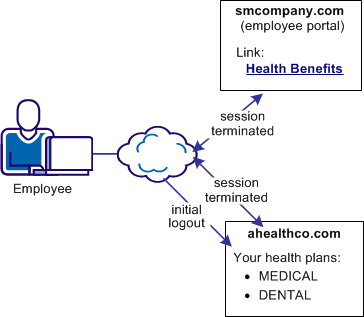
In this use case, an smcompany.com employee authenticates at the employee portal. The employee selects a link to view health benefits at ahealthco.com. The employee is taken to the ahealthco.com website and presented with the health benefit information without having to sign on to the site.
When the employee logs out, ahealthco.com wants the user session at its site and at smcompany.com terminated. Terminating both sessions prevents an unauthorized person from using the existing sessions to access resources at smcompany.com or ahealthco.com.
The following illustration shows the use case.
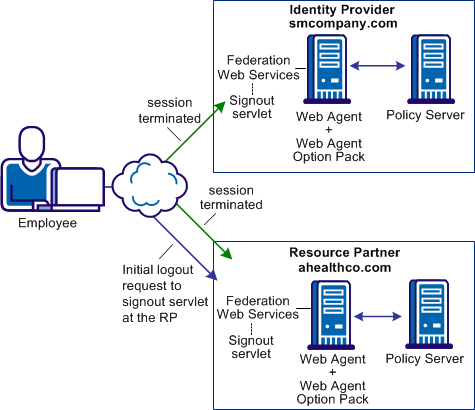
The following federated deployment solves Use Case: WS-Federation Sign-out.
In this solution:
The following figure illustrates WS-Federation sign-out.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The following sequence of events occurs:
The SignoutConfirm page generates a frame-based HTML page. Each frame contains a Signout Cleanup URL for each Resource Partner that is associated with the user session.
In this use case, several companies contract health benefits from ahealthco.com. A user logs on to ahealthco.com to view their health benefits. Ahealthco.com must determine which Identity Provider it sends an authentication request to for a particular user.
IdP discovery is useful in federated networks that have more than one partner providing assertions. This profile provides a dynamic way for a Service Provider to determine which Identity Provider has the necessary user record.
The following illustration shows a network with the Identity Provider Discovery profile in use.
Note: A prior business agreement between the sites in this network exists so that all sites interact with the Identity Provider Discovery service.
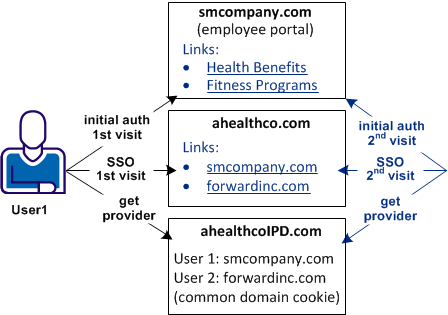
In this example, User1 arrives at ahealthco.com. Ahealthco.com determines that User1 came from smcompany.com. Aheathco.com sets a cookie for smcompany.com in the common domain cookie at ahealthco.com. Other companies, such as forwardinc.com is another Identity Provider that uses ahealthco.com as a health provider. When a user from forwardinc.com comes to ahealthco.com, a cookie is set in the common domain cookie also.
Federation can solve Use Case: Identity Provider Discovery Profile.
The IdP Discovery profile (SAML 2.0 only) is implemented using a cookie domain that is common to the two federated partners. A cookie in the agreed upon domain contains the list of IdPs that a user has visited.
Note: The user that the Service Provider wants to authenticate must have visited the Identity Provider and authenticated before arriving at the Service Provider.
In this solution:
The following illustration shows the federated network for this solution.
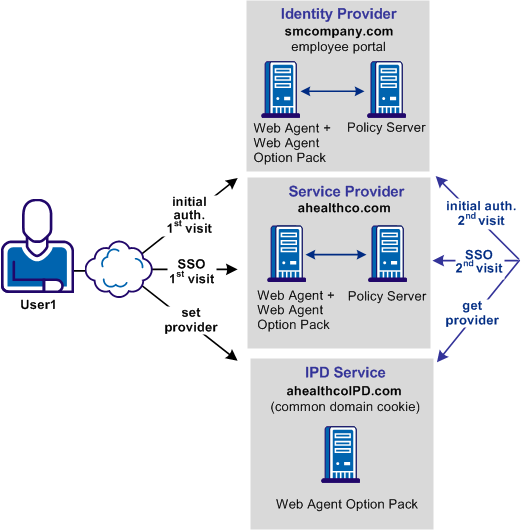
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The transaction flow is as follows:
An agreement exists between smcompany.com and ahealthco.com to use ahealthcoIPD.com as the IPD service.
In this use case, smcompany.com issues assertions for ahealthco.com and discounts.com. Ahealthco.com uses the SAML 2.0 profile. Discounts.com uses the WS-Federation profile. The assertions issued must be generated according to the appropriate profile so that the relying party can consume the assertion.
The following illustration shows the multiprotocol use case.
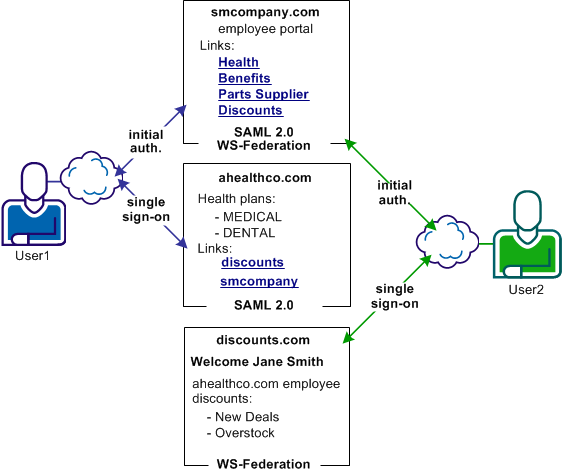
The following federation deployment solves the Use Case: Federation with Multiple SSO Profiles.
Note: The single sign-on transactions in this solution are similar to the using account linking transactions.
In this solution:
User 1
User 2
The following illustration shows a federated network that implements multiprotocol support.
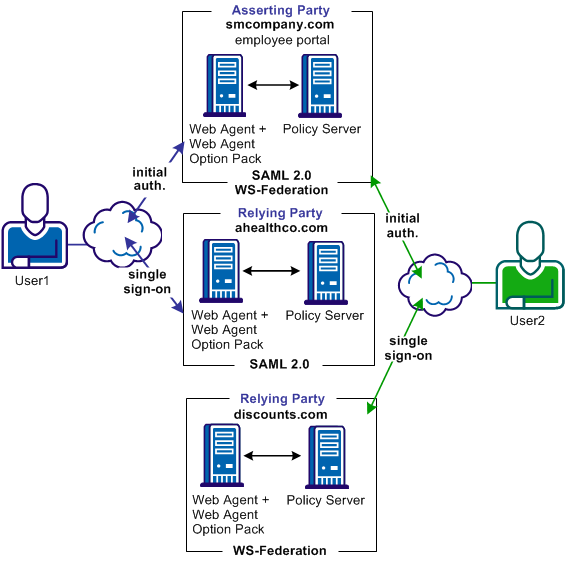
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
In this multiprotocol solution, the flow of the single sign-on transactions for the various SSO profiles is similar to the account linking SSO transactions.
For this solution, the following partnerships are configured at smcompany.com
The following partnership is configured at ahealthco.com:
The following partnership is configured at discounts.com:
In this use case, forwardinc.com is a car rental service and exampleair.com is a travel agency.
A customer of forwardinc.com logs in and authenticates at forwardinc.com, then clicks a link at the site to get a quote for a car rental. The customer profile at forwardinc.com includes the customer frequent flyer number for exampleair.com. The frequent flyer account determines a certain status level at forwardinc.com. The status level determines which discount offers the customer receives for car rentals.
The following illustration shows this use case.
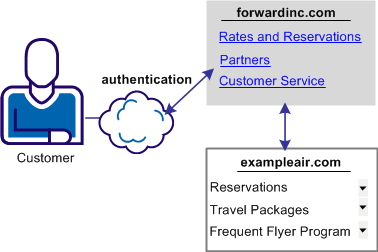
Forwardinc.com wants to present the appropriate discount information to its customers. However, it does not want customers to log in and authenticate at exampleair.com first then having to log in again at its site.
The SAML 2.0 Attribute Query/Response profile can solve Use Case: SAML 2.0 User Authorization Based on a User Attribute.
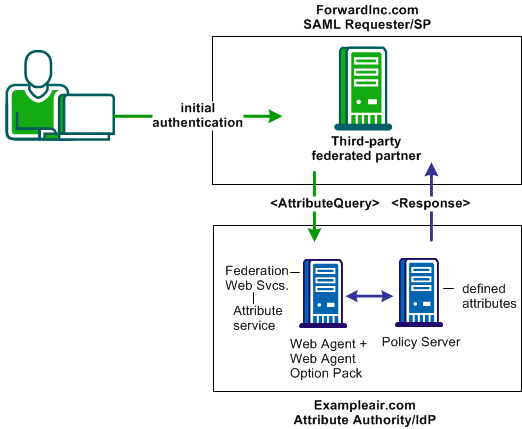
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
In this deployment,
Note: CA SiteMinder® must be serving as an IdP to implement the attribute query profile. This means that CA SiteMinder® can only be an Attribute Authority and respond to attribute queries. CA SiteMinder® cannot serve as an SP and cannot send attribute queries.
Forwardinc.com is acting as a SAML Requester. When a customer logs in at this site, the following sequence of events occurs:
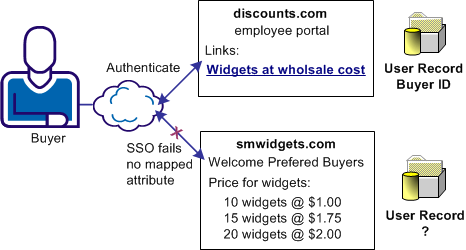
In this use case, discounts.com purchases widgets from smwidgets.com.
A buyer for discounts.com clicks on a link to access the latest widget price list at smwidgets.com. The buyer is taken to the smwidgets.com website and presented with the price list without having to log in to the discounts.com website.
The following illustration shows this use case.
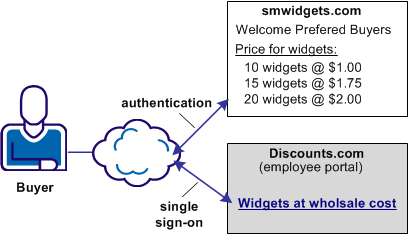
There are no buyer identities stored locally at discounts.com, so discounts.com wants to obtain an identity for buyers at smwidgets.com. Discounts.com sends an authentication request to smwidgets.com. Smwidgets.com receives the request, but it cannot find a value for the NameID attribute. It generates a unique persistent identity for the buyer and adds this identity to the assertion. Discounts.com uses this unique identifier to allow the buyer access to the requested resource.
Use of the Allow/Create attribute solves Use Case: Single Sign-on with No Name ID at the IdP.
NOTE: This solution requires the SAML 2.0 profile.
Federation is deployed at discounts.com and smwidgets.com. A Web Agent and Web Agent Option pack is installed on one system, and the Policy Server is installed on another system.
In the following illustration, smwidgets.com is the Identity Provider and discounts.com is the Service Provider.
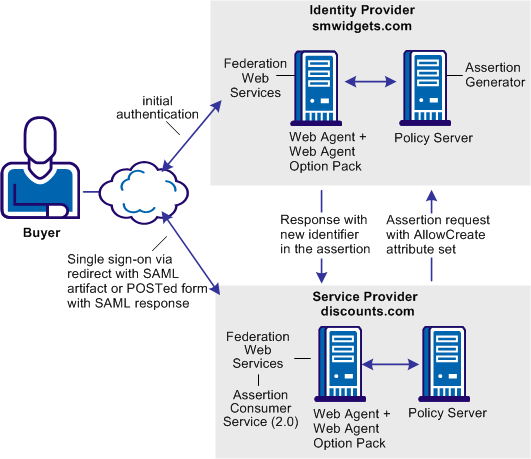
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
To enable single sign-on between the two sites with no user identity at the Identity Provider, the following sequence of events occurs.
In this use case, CompanyA protects non-federated web applications and supports federated single sign-on. In a CA SiteMinder® deployment, you cannot have two sessions for a single user that travels from the web application environment to the federated environment. As the user navigates between each environment, the session cookies would overwrite one another.
The following illustration shows a site that combines a federated environment and a web application environment.
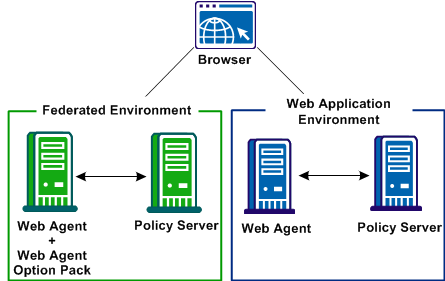
This solution illustrates how security zones lets you set up a parallel web application and a federation environment to solve the Use Case: SSO Using Security Zones.
A security zone is a segment of a single cookie domain, which is used to partition applications. You can assign different security requirements to each zone. Security zones lets the Policy Server generate different session cookies for a single user in each environment. Though two uniquely named session cookies are generated, each cookie represents the same session across the web application and federated environments. Web agents at the asserting party enforce security zones.
The following figure illustrates a deployment with two different environments at a single asserting party. One environment is for federation functionality and the other is for web application protection.
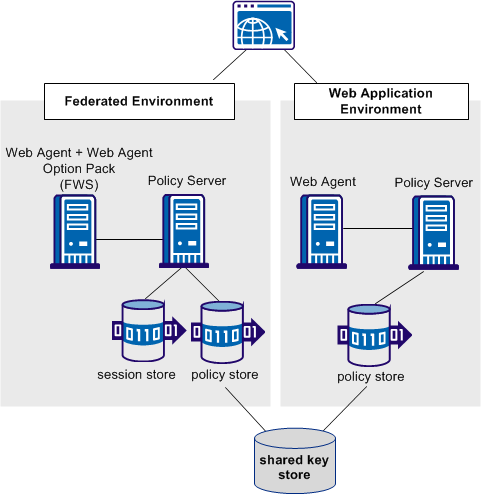
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The figure reflects the following setup:
Web Application Environment
DefaultAgent
SM (default zone)
The DefaultAgent configuration enables the Web Agent to read and write the default session cookie, SMSESSION.
Federation Environment
FedWA
The FedWA configuration enables the Web Agent to read and write SMSESSION cookies.
Note: For this solution to work, each environment must have its own Agent Configuration Object.
The following sequence of events follows:
The user already has an SMSESSION cookie from a prior authentication in the web application environment.
Federation requires a persistent session, which is stored in the session store. The SMSESSION cookie that is read from the web application environment is not persistent. When the Policy Server generates a federation cookie, it modifies the cookie and upgrades the session to be a persistent session.
In the use case, the IdP, discounts.com, includes an attribute named buyer ID that identifies a particular user. The buyer ID value is entered as the NameID in the assertion. However, there is no mapped identity at smwidgets.com for the buyer ID. Smwidgets.com must create an attribute in the appropriate user record so that the buyer can authenticate and gain access to the protected resource.
The administrator at the smwidgets.com establishes a mapping using dynamic account linking. The mapping lets smwidgets can authenticate the buyer and can allow access to resources. When a buyer at discounts.com selects a link to access the latest price list on widgets at smwidgets.com, the buyer is logged in without having to reauthenticate.
The following illustration shows this use case.
Federation can be deployed at IdPA.com and SPB.com to solve Use Case: SSO with Dynamic Account Linking at the SP.
Note: Dynamic account linking is only supported with SAML 2.0.
CA SiteMinder® is deployed at both sites. Each site has a Web Agent and Web Agent Option Pack installed on one system, and the Policy Server on another system.
The following illustration shows single sign-on with dynamic account linking at the Service Provider.
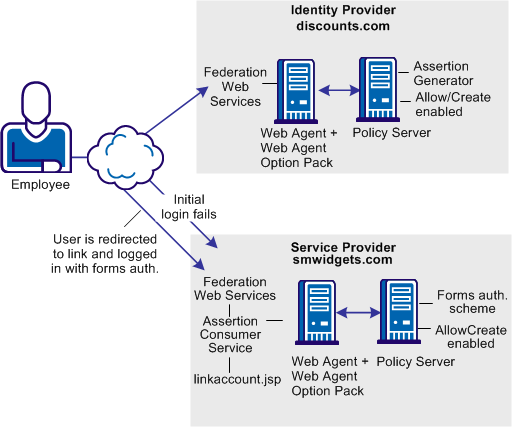
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The following sequence of events occurs:
Note: The linkaccount.jsp file must be part of a protected realm. The default location for this file is http://sp_home/affwebservices/public/. Copy the file from this location to a protected realm.
The search specification configured in the SAML 2.0 partnership indicates which attribute is mapped to the NameID. In this case, the search specification is buyerID=%s.
The next time that the same user presents an assertion with the buyer ID, the user successfully gains access to the requested resource.
Configure the following components at the Service Provider to enable dynamic account linking.
Note: Dynamic account linking is only supported with SAML 2.0.
Enables the creation of attributes in an existing user store.
Sends the user to the linkaccount.jsp file when authentication fails. An authentication scheme protects the redirect URL. The scheme requests the user to log in to create a session.
Must be enabled at the Service Provider Web Agent.
Indicates which attribute the NameID from the assertion replaces
Enable dynamic account linking for SAML 2.0 POST or Artifact single sign-on at the Service Provider
Follow these steps:
Note: The accountlinking must be set to yes (accountlinking=yes).
The default location for this file is http://sp_home/affwebservices/public/.
To protect resources with an authentication scheme, refer to information about authentication schemes in the Policy Server Configuration Guide.
The redirect URL is part of the SAML 2.0 authentication scheme setup at the Service Provider.
Complete the following fields with the values shown:
http://sp_home/protected_realm/linkaccount.jsp
Example: http://smwidgets.com/partner_resources/linkaccount.jsp
The default location of the linkaccount.jsp file is http://sp_home/affwebservices/public/. Copy the file from this directory to a directory that is configured as a protected realm.
HTTP POST
|
Copyright © 2014 CA.
All rights reserved.
|
|