

Installation and Upgrade Guides › SiteMinder Upgrade Guide › Using FIPS-Compliant Algorithms › Migration Roadmap—Re-Encrypt Sensitive Data
Migration Roadmap—Re-Encrypt Sensitive Data
Before your environment can operate in FIPS-only mode, you must:
- Set specific components to operate in FIPS-migration mode.
- Re-encrypt existing sensitive data using FIPS-compliant algorithms.
The following figure illustrates a sample 12.52 SP1 environment and details:
- The order in which you configure components to operate in FIPS-migration mode.
- The existing sensitive data that you must re-encrypt.
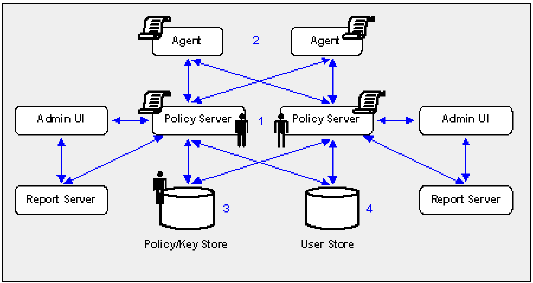
- Each Policy Server in the environment is set to operate in FIPS-migration mode.
- The policy store key is encrypted using algorithms that are not FIPS–compliant. Re-encrypt this key for each Policy Server in the environment before configuring the environment for FIPS-only mode. The policy store key is located in the EncryptionKey.txt file.
- The policy store administrator password is encrypted using algorithms that are not FIPS–compliant. Re-encrypt this password before configuring the environment for FIPS-only mode.
Important! If you have configured a separate database for a key store, audit logs, token data, or a session store, these passwords are encrypted using algorithms that are not FIPS–compliant. Re-encrypt these passwords before configuring the environment for FIPS-only mode.
- The CA SiteMinder® superuser password is encrypted using algorithms that are not FIPS–compliant. Re-encrypt the password before configuring the environment for FIPS-only mode.
Note: The password is for the default CA SiteMinder® administrator account. The account is used for all administrative tasks that do not require direct access to the Administrative UI. The password is not the password for the Administrative UI administrator account with superuser privileges.
- Each CA SiteMinder® Agent, including custom Agents, in the environment is set to operate in FIPS-migration mode.
The shared secrets that the Policy Servers and Agents use to establish encrypted communication channels are encrypted using algorithms that are not FIPS–compliant. Re-encrypt the shared secrets before configuring the environment for FIPS-only mode.
- Keys and sensitive policy store data is re-encrypted.
Note: The previous figure depicts a single database instance as a policy/key store. Your environment can use separate database instances for individual policy and key stores.
Sensitive data stored in a policy store or policy and key stores is encrypted using algorithms that are not FIPS–compliant. Re-encrypt the keys and sensitive policy store data before configuring the environment for FIPS-only mode.
- (Optional) If your environment uses basic password services, a Policy Server operating in FIPS-migration mode re-encrypts each Password Blob with FIPS–compliant algorithms when the respective user is challenged for authentication. To prevent users from losing their password history and being locked out, identify the Password Blobs that the Policy Server did not re-encrypt and notify users to log in or to change their password.
Note: How the password policy is configured determines when the Policy Server re-encrypts the Password Blob:
- If the password policy is configured to track successful or failed logins, the Policy Server re-encrypts the Password Blob when the user logs in.
- If the password policy is not configured to track logins, the Policy Server re-encrypts the Password Blob when the user changes the password.
Copyright © 2014 CA.
All rights reserved.
 
|
|


