

‑The following figure shows the configuration process for each partner. CA SiteMinder® Federation does not have to be installed at each site.
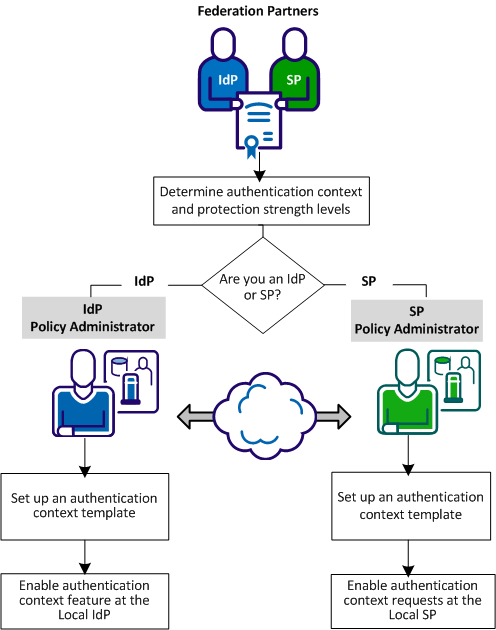
Complete the following steps to configure authentication context processing:
The SP can require specific authentication contexts and strength levels before it permits access to a requested resource. Based on the sensitivity of the resources at the SP, the SP has to have confidence in the assertion it receives from the IdP.
The administrators at the IdP and SP have to establish guidelines for supported authentication contexts and the relative strength of each authentication context URI. The order of the URIs at the IdP together with the associated strength levels affects how the IdP responds to the SP.
For example, an SP requests an authentication context for an X.509 certificate and a comparison value of exact. The IdP has to authenticate the requesting user at a suitable strength level and satisfy the comparison value during the evaluation of the authentication context.
Set up an authentication context template to implement authentication context processing. This procedure is the same for an Identity Provider or Service Provider.
Follow these steps:
The View Authentication Context Templates window opens.
The template wizard opens at the first step.
Map the protection levels from an authentication scheme to the URIs. The protection levels indicate the strength of an authentication scheme, ranging between 1 through 1000, with 1000 being the strongest. Individual URIs can have unique protection levels; however, grouping URIs means that they have the same level of strength.
Consider the following information when assigning protection levels:
Read more about protection level assignments.
The template is complete.
The protection levels indicate the strength of the authentication. Assign protection levels to each selected authentication context URI. Specify the maximum level for each URI in the list. The minimum protection level is automatically determined based on the maximum level for the subsequent URI in the list. This range reflects the protection level.
The protection level assignments must reflect the protection levels of the configured Policy Server authentication schemes. For example, the Policy Server can have an X.509 authentication scheme at a protection level of 20. The protection level range that the template specifies must include 20. Finally, the Policy Server generates a URI strength level that is based on the protection level.
Example
|
Authentication Schemes set at the Policy Server |
Protection |
|---|---|
|
urn:oasis:names:tc:SAML:2.0:ac:classes:X509 |
20 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes:MobileTwoFactorContract |
15 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes:InternetProtocol |
10 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes:Password |
5 |
For each URI, the Policy Server automatically maps the protection level to a URI strength level. The ranges cover the protection level of the authentication scheme. For example:
|
URI |
Protection Level Max |
URI Strength |
|---|---|---|
|
urn:oasis:names:tc:SAML:2.0:ac:classes:X509 |
1000 |
4 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes: |
15 |
3 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes:InternetProtocol |
10 |
2 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes:Password |
5 |
1 |
If you group several of the URIs, the grouping enables URIs with different protection levels to have the same URI strength. This strength means that the URIs are considered equivalent.
The following modified table shows the grouping of the X.509 URI and the MobileTwoFactorContract URI.
|
URI |
Protection Level Max |
URI Strength |
|---|---|---|
|
urn:oasis:names:tc:SAML:2.0:ac:classes:X509 |
1000 |
3 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes: |
800 |
3 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes:InternetProtocol |
700 |
2 |
|
urn:oasis:names:tc:SAML:2.0:ac:classes:Password |
200 |
1 |
The range of strength levels reflects the total number of groups in the list. For example, if there are three groups, the strength level ranges from 1 to the total number groups, which are 3.
The Policy Server acting as the IdP can obtain the authentication context for an assertion in these two ways:
Specify a URI for the authentication class and ignore the context request from the SP. A hard-coded entry can act as the default authentication context for IdP-initiated single sign-on.
The Policy Server automatically detects the user session authentication context using the authentication context template.
The IdP uses the template even if the authentication request from the SP does not include the <RequestedAuthnContext> element. The presence of the element triggers extra evaluation by the IdP and constrains the choices of what it can put in the assertion.
You can find more information about the flow of authentication context processing.
Follow these steps:
The following table shows how the Configure AuthnContext and the Ignore RequestedAuthnContext settings work together:
|
Configure AuthnContext |
Ignore RequestedAuthnContext |
SP requests AuthnContext |
Result |
|---|---|---|---|
|
Predefined Class |
Selected |
Yes |
IdP ignores the <RequestedAuthnContext> and uses the defined value in the assertion. |
|
Predefined Class |
Selected |
No |
IdP returns the defined value in the assertion by default. |
|
Predefined Class |
Not selected |
Yes |
Transaction fails because the IdP is not configured to handle the authentication context request. The IdP returns an error message to the SP. |
|
Predefined Class |
Not selected |
No |
IdP returns the defined class value in the assertion by default. |
|
Automatically Detect Class |
Selected |
Yes |
IdP compares the protection level for the authentication scheme against the authentication context template and returns the matching authentication URI in the assertion. The IdP ignores the values in the SP request. |
|
Automatically Detect Class |
Selected |
No |
IdP compares the protection level for the authentication scheme against the authentication context template and returns the matching authentication URI in the assertion. The IdP ignores the values in the SP request. |
|
Automatically Detect Class |
Not selected |
Yes |
IdP compares the protection level against the authentication context class that the SP sends. The IdP uses the authentication context template to determine the authentication URI it places in the assertion. |
|
Automatically Detect Class |
Not selected |
No |
IdP compares the protection level for the authentication scheme against the authentication context template and returns the matching authentication URI in the assertion. |
|
Copyright © 2014 CA.
All rights reserved.
|
|