

The ability of CA SiteMinder® Web Services Security to obtain security information from XML documents without user interaction and produce WS-Security headers, SAML Session Ticket assertions, and SiteMinder session cookies lets you securely deploy web services using a number of service models.
All requests are authenticated and handled by a single web service.
All requests are sent to a web service responsible for authentication, which then returns the message and authentication data back to the web service consumer. The web service consumer application can then send requests containing this authentication data to other related web services within or across domains.
All requests are received by a web service responsible for authentication and then passed, with authentication data, to one or more other web services for handling. That is, message and authentication data always flows from the authentication web service directly to the next required web service, and from there to the next web service and so on, without further interaction from the web service consumer.
Choosing the appropriate authentication service model is the first, and probably most significant, decision you must make when designing a web service implementation. Your choice of service model also plays a significant role in determining the most appropriate CA SiteMinder® Web Services Security authentication schemes to use.
The single-step service model is the simplest possible model for web services—requests from a web service consumer are authenticated and handled by a single web service. The following diagram shows the process by which web services consumers are authenticated using this simple model:
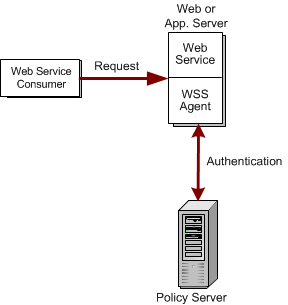
Appropriate authentication schemes for use in the single-step authentication model are as follows:
The multistep authentication model is like the CA SiteMinder cookie-based single sign-on implementation, in which WS-Security headers or SAML Session Ticket assertions take the place of the cookie.
In the multistep authentication model, a single web service is responsible for authenticating all incoming web service requests. This authentication service verifies a web service consumer’s identity and returns an XML message with authentication data in the form of WS-Security headers or a SAML Session Ticket assertion. The web service consumer can then use this to add to subsequent requests to facilitate authentication by other associated web services.
The process that the web service consumer goes through when making a request has two phases:
The following illustration shows how request are processed in the multistep authentication service model:
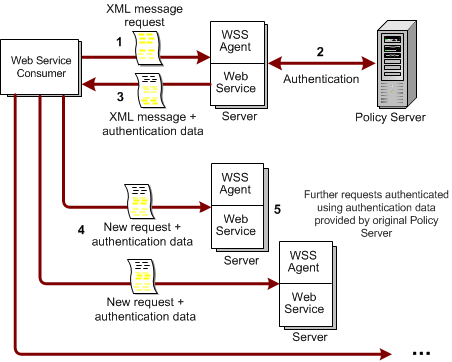
After authentication, the request goes through the authorization process. A response attribute associated with the authorizing policy causes the Policy Server to generate a response which it sends to the SiteMinder WSS Agent, instructing it to return authentication data to the web service.
Appropriate authentication schemes for initial authentication by the authentication web service in the multistep authentication model are as follows:
The authorizing policy for the authentication web service should trigger one of the following response types:
These responses instruct the SiteMinder WSS Agent to pass authentication data in the form of WS-Security headers or SAML Session Ticket assertions (as appropriate) back to the web service consumer for use in requests to associated web services. The associated web services should be protected using the corresponding authentication scheme:
The chain authentication model is appropriate for solutions that require XML messages to flow between multiple web services without further intervention from the requesting web service consumer.
In the chain authentication service model, a single web service is responsible for authenticating all incoming web service requests. This authentication service verifies a web service consumer’s identity, and then adds authentication data in the form of WS-Security headers or a SAML Session Ticket assertion to the XML message. It then passes the document to downstream web services for processing.
The following illustration shows the flow of data in the chain authentication model.
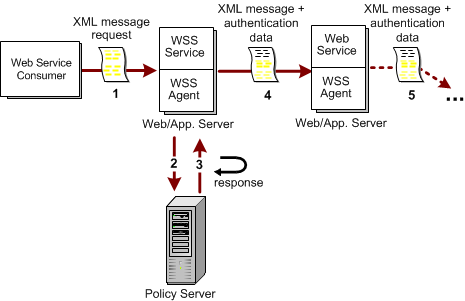
The most appropriate authentication schemes for initial authentication of requests from the web service consumer by the authentication web service in the chain authentication model are as follows:
The authorizing policy for the authentication web service should trigger one of the following responses:
These responses instruct the SiteMinder WSS Agent to add WS-Security headers or SAML Session Ticket assertions (as appropriate) to the XML request passed to the next downstream web service in the chain, which should then be protected using the corresponding authentication scheme:
Although CA SiteMinder® Web Services Security is primarily designed to provide message content-based security for web services, it also provides limited support for CA SiteMinder® session ticket-based session management. A CA SiteMinder® session cookie contains basic information about the user account that is associated with a request and authentication information for that user. The session cookie can be used to identify a user session across all sites within a single cookie domain in your WSS environment..
SiteMinder WSS Agents always add session cookies to HTTP request headers upon successful authentication and authorization. SiteMinder WSS Agents that have access to HTTP header information can be configured to authenticate a request using a session cookie in the HTTP request header. In this case, there is no need to configure responses to generate other token types at the authentication web service.
For example, in the following environment, session cookies can be used without the need to configure WS-Security or SAML Session Ticket responses at the authentication web service:
To configure SiteMinder WSS Agents to validate requests using associated session tickets, set the XMLSDKAcceptSMSessionCookie agent configuration parameter. See the SiteMinder WSS Agent documentation for details.
|
Copyright © 2014 CA.
All rights reserved.
|
|