

The following graphic shows the required steps to configure an Active Directory user store connection:
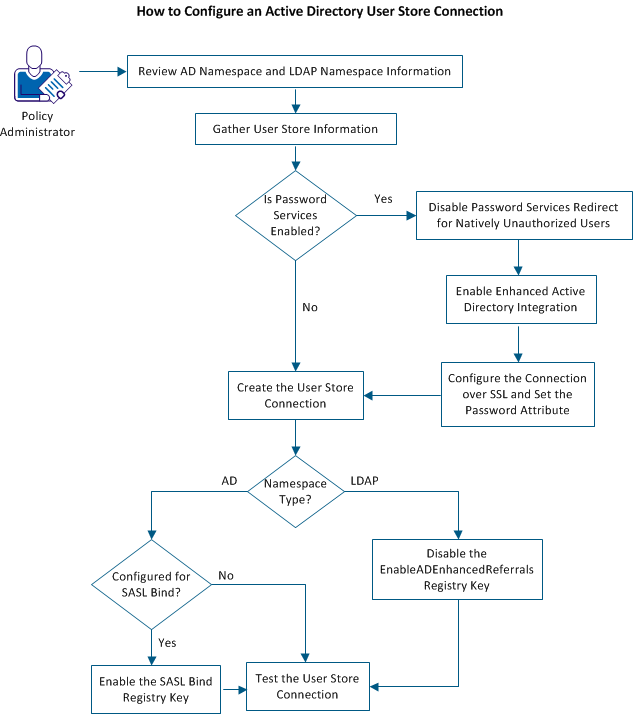
To configure an AD user store connection, complete the following procedures:
Verify that the following are in place before you configure an AD user store connection:
You can configure the user store connection as either an AD or LDAP namespace. The type of namespace that you select affects supported features and other areas of CA SiteMinder® functionality.
The following table describes the advantages and disadvantages of the AD and LDAP namespaces:
|
Namespace Type |
Advantages |
Disadvantages |
|---|---|---|
|
AD |
Note: Both the Policy Server and the systems hosting Active Directory user stores must have an established trust.
|
Note: Regardless of the code page that you are using, CA SiteMinder® treats characters as they are defined in Unicode. Although your code page can reference a special character as single-byte, CA SiteMinder® treats it as a multibyte character if Unicode defines it as such. |
|
LDAP |
|
For CA SiteMinder® to run efficiently with an Active Directory user directory, index the object class attribute in Active Directory. Note: For more information, see your vendor-specific documentation.
An agent can run in a Windows user security context for accessing web resources on IIS web servers. Before SiteMinder can provide the Windows user security context, configure a session store and enable persistent sessions on a per realm basis. To enable this feature, select the following option under Directory Setup while creating a user directory using the Administrative UI: Use authenticated user's security context |
Gather the required information for the LDAP settings and the user attributes, before creating the user store connection.
Contact the directory server administrator to gather this information.
Specifies the IP address and port of the Active Directory host system.
Specifies the location in the LDAP tree that the Policy Server uses as the starting point for the directory connection. The Policy Server begins searching at the root when locating a user.
Example: dc=domainname,dc=com
Specifies the text string of an LDAP search expression or user DN for locating users in an LDAP user store. A complete lookup requires a Start and End string. The combination of the Start string, username, and End string is used to search the LDAP user store.
Example (Start): (sAMAccountName=
Example (End): )
Specifies the name of the attribute SiteMinder uses as the Universal ID.
Example: sAMAccountName
Specifies the name of the user directory attribute that holds the disabled state of the user.
Example: carLicense (or any integer attribute)
Specifies the name of the user directory attribute that CA SiteMinder® uses to authenticate the password of a user.
Example: unicodePwd
Specifies the name of the user directory attribute that SiteMinder can use for Password Services data.
Example: audio
The value for Password Data can be any large binary attribute. A value is needed only if you are using Basic Password Services.
By default, SiteMinder reprompts users for credentials if those users are natively disabled in the directory server. SiteMinder redirects these users to Password Services, even if Password Services is not enabled for the authentication scheme protecting the resource.
To prevent this behavior, the following registry key is required:
IgnoreDefaultRedirectOnADnativeDisabled
Contact the policy server administrator and request that the key be created and enabled.
Follow these steps:
HKEY_LOCAL_MACHINE\Software\Netegrity\SiteMinder\CurrentVersion\Ds\LDAPProvider
Value: 0 (disabled) or 1 (enabled)
Default: 0
Important! If a password policy that specifies a redirect to Password Services is in effect, CA SiteMinder® redirects the natively disabled users to Password Services regardless of this registry key setting.
Active Directory 2008 has several user and domain attributes that are specific to the Windows network operating system (NOS). The LDAP standard does not require these user and domain attributes. If Password Services is enabled, enable Enhanced Active Directory Integration using the Administrative UI. This option improves the integration between the user management feature of the Policy Server and Password Services with AD by synchronizing AD user attributes with CA SiteMinder® mapped user attributes.
Follow these steps:
Enhanced Active Directory integration is enabled.
Configuring the user store connection lets the Policy Server communicate with Active Directory. If the environment uses Password Services, an SSL connection and a password attribute (Ex: uincodePWD) are required.
Note: For more information about configuring Active Directory to communicate over SSL, see your vendor-specific documentation.
Follow these steps:
Note: If the Policy Server and an Active Directory namespace communicate over SSL, specify the IP address and port in Server under Directory Setup. When the IP address is not specified, an error is logged that states the user directory cannot be contacted. A Windows Event is also logged that reports the certificate does not match the server name.
Note: The certificates that the Policy Server and the directory store use must be FIPS-compliant under the following conditions:
Note: When configuring a user directory in the Active Directory (AD) namespace, specify the fully qualified domain name (FQDN) of the administrator in the Username field. Otherwise, user authentication can fail.
The user directory connection is created.
If the user store connection is configured with the LDAP namespace, disable the EnableADEnhancedReferals registry key. Disabling this registry key prevents LDAP connection errors from occurring.
Contact the policy server administrator and request that the key be disabled.
Follow these steps:
HKEY_LOCAL_MACHINE\Software\Netegrity\SiteMinder\CurrentVersion\Ds\LDAPProvider
Value: 0 (disabled) or 1 (enabled)
Default: 1
A Windows-based Policy Server can authenticate a user in an Active Directory using SASL. To enable the use of a SASL bind, create and enable the EnableSASLBind registry key.
Note: When enabling this setting, set the administrator name on the user directory configuration to the AD login name, rather than the fully qualified distinguished name.
Important! If you are configuring an SSL connection between the Policy Server and the user store, do not enable the registry key.
Contact the policy server administrator and request that the key be created and enabled.
Follow these steps:
HKEY_LOCAL_MACHINE\Software\Netegrity\SiteMinder\CurrentVersion\Ds\LDAPProvider
Test the connection by querying for a user.
Follow these steps:
Example: sAMAccountName
The account details appear. You have successfully connected to the user store.
|
Copyright © 2014 CA.
All rights reserved.
|
|