

The simple partnership provides an overview of configuring federated partnerships using partnership federation.
The remaining chapters in the guide provide detailed procedures for every task you can perform. For detailed configuration instructions, use these procedures as well as the Help in the Administrative UI.
The session store holds data for the following federation features:
A SAML assertion and the associated artifact are generated at the asserting party. The artifact identifies the generated assertion. The asserting party returns the artifact to the relying party. The relying party uses the artifact to retrieve the assertion, which the asserting party stores in the session store.
A persistent session is required for this process to work.
Note: The SAML POST profile does not store assertions in the session store.
The single use policy feature prevents assertions from being reused at the relying party to establish a second session. The relying party stores time-based data about the assertion, which is known as expiry data, in its session store. Expiry data verifies that the assertion is only used one time.
A session store is required at the relying party, but a persistent session is not required.
If single logout is enabled, either partner can stores information about the user session. The session information is kept in the session store. When a single logout request is completed, the session information for the user is removed, invalidating the session.
A persistent session is required at the Identity Provider and Service Provider.
If sign-out is enabled, user context information is placed in the session store. This information enables the Policy Server to generate a sign-out request. When a sign-out request is completed, the session information for the user is removed, invalidating the user session.
A persistent session is required at the Identity Provider and Resource Partner.
You can select the option Persist Authentication Session Variables when configuring federation at a relying party. This option instructs the Policy Server to save authentication context data in the session store as session variables. The Policy Server has access to these variables for use in authentication decisions.
You can select Persist Attributes as a redirect mode at the relying party. The redirect mode determines how a user is redirected to the target application. This mode instructs the Policy Server to store assertion attributes in the session store so they can be supplied as HTTP header variables.
For the IdP to handle an authentication request that is delivered using HTTP-POST binding, the IdP must store the request in the session store.
Enable the session store to hold this type of user session, assertion, and expiry data.
Enable the session store to hold data when using SAML artifact for single sign-on, single logout, and enabling the single use of a policy.
Enable the session store from the Policy Server Management Console.
Follow these steps:
If you are going to use persistent sessions in one or more realms, enable the Session Server. When enabled, the Session Server impacts Policy Server performance.
Note: The Use Policy Store database option is disabled. For performance reasons, the session server cannot be run on the same database as the policy store.
The following features require a shared session store to store SAML assertions and user session information.
To implement these features across a clustered Policy Server environment, set up the environment as follows:
Persistent sessions are part of the realm configuration.
Sharing the session store verifies that all Policy Servers have access to assertions when each one receives a request for an assertion.
Sharing the session store verifies that all Policy Servers have access to user session data when each one receives a request for a session logout.
All Policy Servers that generate or consume assertions or process a persistent SMSESSION cookie must be able to contact the common session store. For example, a user logs in to example.com and gets a persistent session cookie for that domain. Every Policy Server that is handling requests for example.com must be able to verify that the session is still valid.
The following illustration shows a Policy Server cluster communicating with one session store:
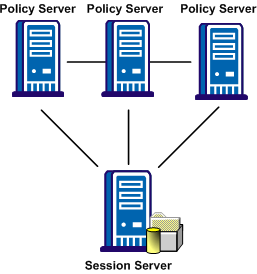
To share a session store, use one of the following methods:
In the Policy Server Management Console, configure the Policy Server to use the designated session store.
For instructions on replicating a database, use the documentation for your database.
|
Copyright © 2014 CA.
All rights reserved.
|
|