

This section contains the following topics:
Manual CA SiteMinder®-to-CA SiteMinder® Deployment Overview
Confirm that Required Components are Installed
Set Up the Identity Provider for the Sample Network
Set up the Service Provider for the Sample Network
Add Functionality to the Federation Deployment
You can accomplish a deployment manually. The manual deployment tasks begin with a simple configuration, single sign-on with POST binding. By starting with a basic configuration, you can complete the least number of steps to see how federation works.
After getting POST single sign-on to work, additional tasks, such as configuring the artifact binding, digital signing, and encryption are described. You can add these features to reflect a real production environment.
Important! The deployment exercise is only for SAML 2.0. These procedures do not apply to a SAML 1.x or WS-Federation configuration.
The manual deployment examples are different from the sample application deployment in the following ways:
The procedures throughout the manual deployment use sample data. To use data from your environment, specify entries for your Identity Provider and Service Provider configuration.
Federation requires that the following components are installed:
This sample federation deployment example assumes that these components are installed and working.
Optionally, set up these features:
SSL is optional for securing communication across the back channel for HTTP-artfact single sign-on.
The session store is required for storing the assertion at the asserting party when using HTTP-Artifact binding. The session store is also required for single logout at either party.
For instructions on setting up a session store database, see the Policy Server Installation Guide. Enable the session store using the Policy Server Management Console. See the Policy Server Administration Guide for instructions.
The sample websites in the CA SiteMinder® federated network are an Identity Provider named idp.demo, and a Service Provider named sp.demo. A business partnership is established between idp.demo and sp.demo.
The following illustration shows the sample federated network.
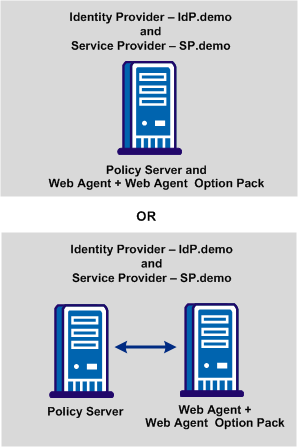
IdP.demo is the Identity Provider. The following table contains sample data for the most basic SAML 2.0 POST single sign-on configuration.
|
Identity Provider Component |
Sample Network |
|---|---|
|
IdP Policy Server
|
Server: www.idp.demo:80 Server type: IIS Web Server |
|
IdP policy store |
IP Address: www.idp.demo:389 Storage: LDAP Root DN: o=idp.demo Admin Username: cn=Directory Manager Password: federation |
|
User store |
Directory name: IdP LDAP Server: www.idp.demo:42088 Server Type: Sun One Directory Server (LDAP) User store: The LDAP directory contains the following users:
userpassword: test mail: <user_name>@idp.demo Root: dc=idp,dc=demo Start: uid= End: ,ou=People,dc=idp,dc=demo |
|
IdP Web Agent with Web Agent Option Pack |
Server: www.idp.demo:80 Server Type: IIS Web Server Agent name: idp-webagent |
|
Assertion Consumer Service URL |
URL: http://www.sp.demo:81/affwebservices/ public/saml2assertionconsumer |
|
Assertion Retrieval Service URL |
URL: http://www.idp.demo:80/affwebservices/assertionretriever |
|
Authentication URL |
URL: http://www.idp.demo/siteminderagent/ |
The following table contains sample data for more advanced SAML 2.0 features, such as the artifact profile, signing and encrypting assertions.
|
Identity Provider Component |
Sample Network |
|---|---|
|
Session store |
Server: www.idp.demo Database type: ODBC Database Source Information: SiteMinder Session Data Source User Name: admin Password: dbpassword |
|
SSL-enabled server |
Server: www.idp.demo:443 Server Type: IIS 6.0 Web The web server with the Web Agent Option Pack is SSL-enabled for artifact binding |
|
Certificate of the Certificate Authority (CA) |
Certificate of CA: docCA.crt DER-encoded Cert: docCA.der This CA signs the server-side certificate to enable SSL |
|
Private key/certificate pair to sign SAML responses |
Certificate: post-cert.crt Private key: post-pkey.der Password: fedsvcs |
|
Certificate (public key) for encryption |
Public key: sp-encrypt.crt |
|
Attribute to include in assertion |
Attribute: unspecified (default) Attribute Kind: User DN Variable Name: firstname Variable Value: givenname
|
The Service Provider is SP.demo. The following table contains sample data for the most basic SAML 2.0 POST single sign-on configuration.
|
Service Provider Component |
Sample Network |
|---|---|
|
SP Policy Server |
Server: www.sp.demo:80 Server type: IIS Web Server |
|
SP policy store |
IP Address: www.sp.demo:389 Storage: LDAP (Sun One Directory Server) Root DN: o=ca.com Admin Username: cn=Directory Manager Password: federation |
|
User Store |
Directory name: SP LDAP Server: www.sp.demo:32941 Server Type: LDAP (Sun One Directory Server) User store: The LDAP directory contains the following users:
userpassword: customer mail: <user_name>@sp.demo Root: dc=sp,dc=demo Start: uid= End: ,ou=People,dc=sp,dc=demo |
|
SP Web Agent and Web Agent Option Pack |
Server: www.sp.demo:81 Server type: Sun ONE 6.1 Web Server Agent name: sp-webagent |
|
Single Sign-on Service |
SSO Service: http://www.idp.demo:80/affwebservices/public/saml2sso |
|
Target Resource |
Target Resource: http://www.sp.demo:81/ |
The following table lists sample data for more advanced SAML 2.0 features, such as setting up the artifact profile, signing and encrypting assertions.
|
Service Provider Component |
Sample Network |
|---|---|
|
Artifact Resolution |
Resolution Service: https://www.idp.demo:443/ |
|
Certificate of Certificate Authority |
Certificate of CA: docCA.crt DER-encoded cert: docCA.der This CA signs the server-side certificate to enable SSL |
|
Certificate (public key) Used to verify signature of SAML responses |
Certificate: post-cert.crt
|
|
Private key/certificate pair Used for decryption and digital signing |
Private key: sp-encrypt.der Public key: sp-encrypt.crt Password: fedsvcs Issuer DN: CN=Certificate Manager,OU=IAM,O=CA.COM Serial Number: 008D 8B6A D18C 46D8 5B |
|
Copyright © 2014 CA.
All rights reserved.
|
|